One-Certificate Application Method and System Based on Government Affairs Data Call
A technology for data calling and business systems, applied in data processing applications, office automation, instruments, etc., to achieve the effect of ensuring information security and avoiding repeated submissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
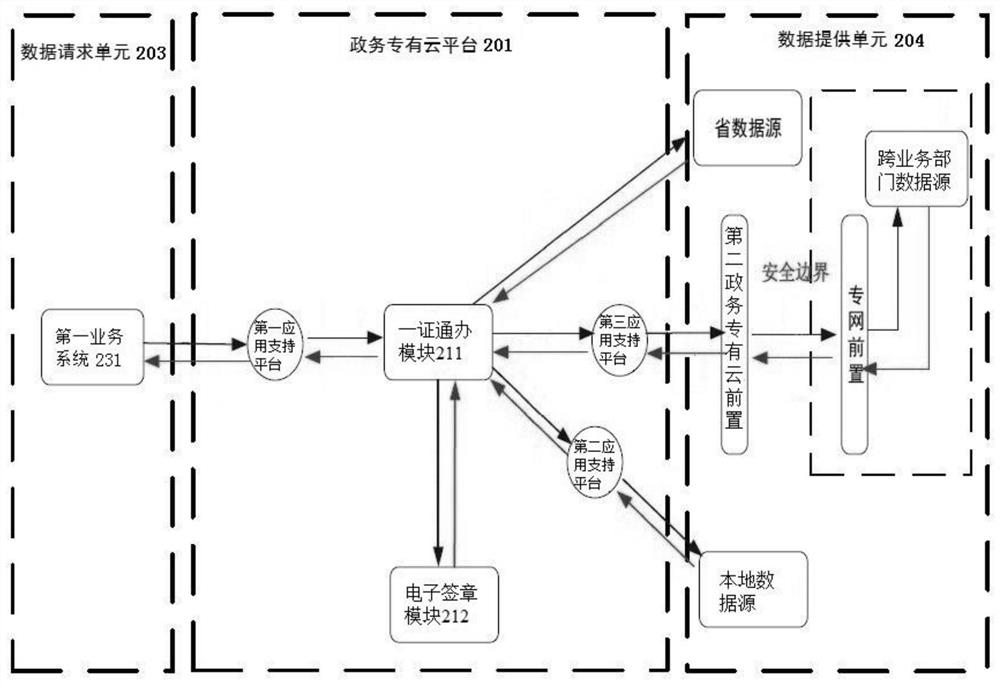
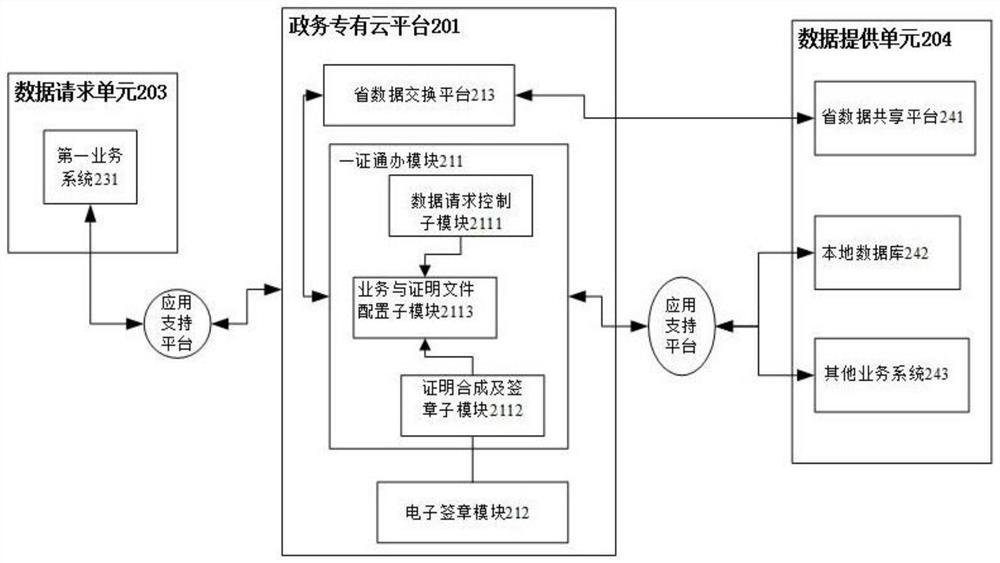
[0078] Embodiment one, such as figure 1 As shown in the figure, it is a schematic flow chart of the one-certificate-handling method based on government affairs data invocation of the present invention in the first embodiment. In this example, the first business system 231 is deployed on the government extranet or a logically isolated private network, and belongs to the same network segment as the government private cloud platform 201 . The first business system 231 includes local business systems such as social security, industry and commerce, and government services. Below, the method of the present invention will be described in detail by taking the business applicant to handle social insurance for the masses as an example.
[0079] Business bidders will verify their identity through the business self-service terminal identification. After the identity verification is successful, the user is allowed to submit a request to apply for social security business. If the identity ...
Embodiment 2
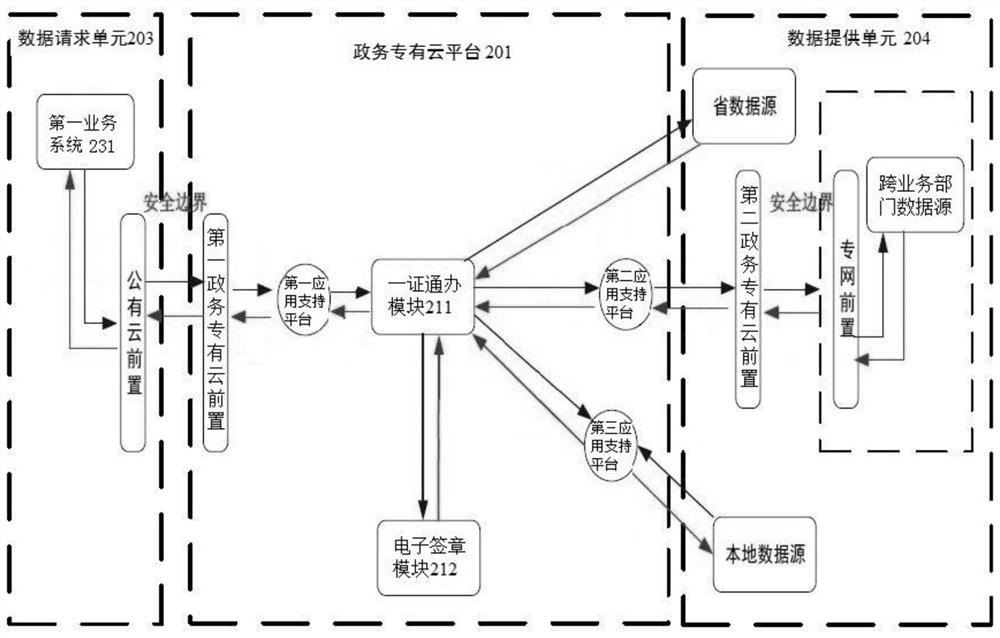
[0084] Embodiment two, such as figure 2 As shown, it is a schematic diagram of the process framework of the method and system of the one-certificate application based on government data calls in this embodiment of the present invention. In this embodiment, the business system includes public security, national land and other cross-network segment or cross-regional business systems. The first business system 231 is deployed on a public cloud or a physically isolated private network, and does not belong to the same network segment as the private government cloud platform 201 . Hereinafter, the method of the present invention will be described in detail by taking the business applicant handling public security or land-related business as a window business staff as an example. .
[0085] The window business staff verifies their identity information by identifying business certificates or account passwords. After successful identity verification, they can send a data request to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com