A method for realizing single sign-on assets based on two-dimensional code identity authentication
An identity authentication and single sign-on technology, applied in transmission systems, electrical components, etc., can solve security risks, asset account, password management and other issues, and achieve the effect of ensuring asset security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings. It should be noted that this embodiment is based on the technical solution, and provides detailed implementation and specific operation process, but the protection scope of the present invention is not limited to the present invention. Example.
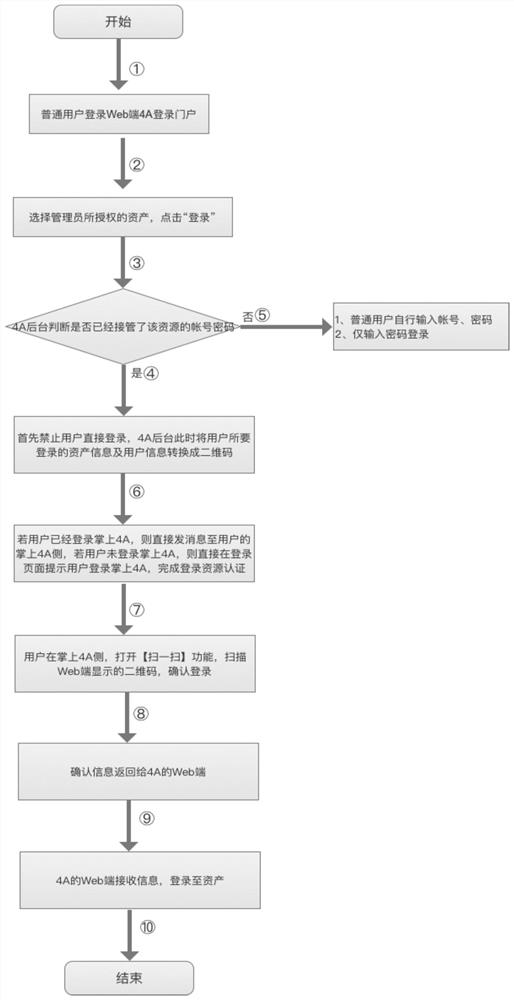
[0021] This embodiment provides a method for realizing single sign-on assets based on the two-dimensional code identity authentication method, such as figure 1 shown, including the following steps:
[0022] S1. Ordinary users select assets within the scope of authority on the login portal of 4A on the web, and click Login;
[0023] S2, 4A background judges whether the login account and asset password of the asset selected in step S1 have been taken over by 4A; if it has been taken over, the user is prohibited from directly logging in to the asset, and the background database queries the user and the asset to be logged in infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com