A method and system for manage confidential documents
A technology of secret-related documents and management methods, which is applied in the field of secret-related document management methods and systems, can solve problems such as document leakage, poor security, and inconsistent management methods, and achieve the effects of increasing production speed, wide application range, and flexible algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] For the step numbers in the embodiment of the present invention, it is only set for the convenience of explanation and description, and there is no limitation on the order of the steps. The execution order of each step in the embodiment can be carried out according to the understanding of those skilled in the art Adaptive adjustment.
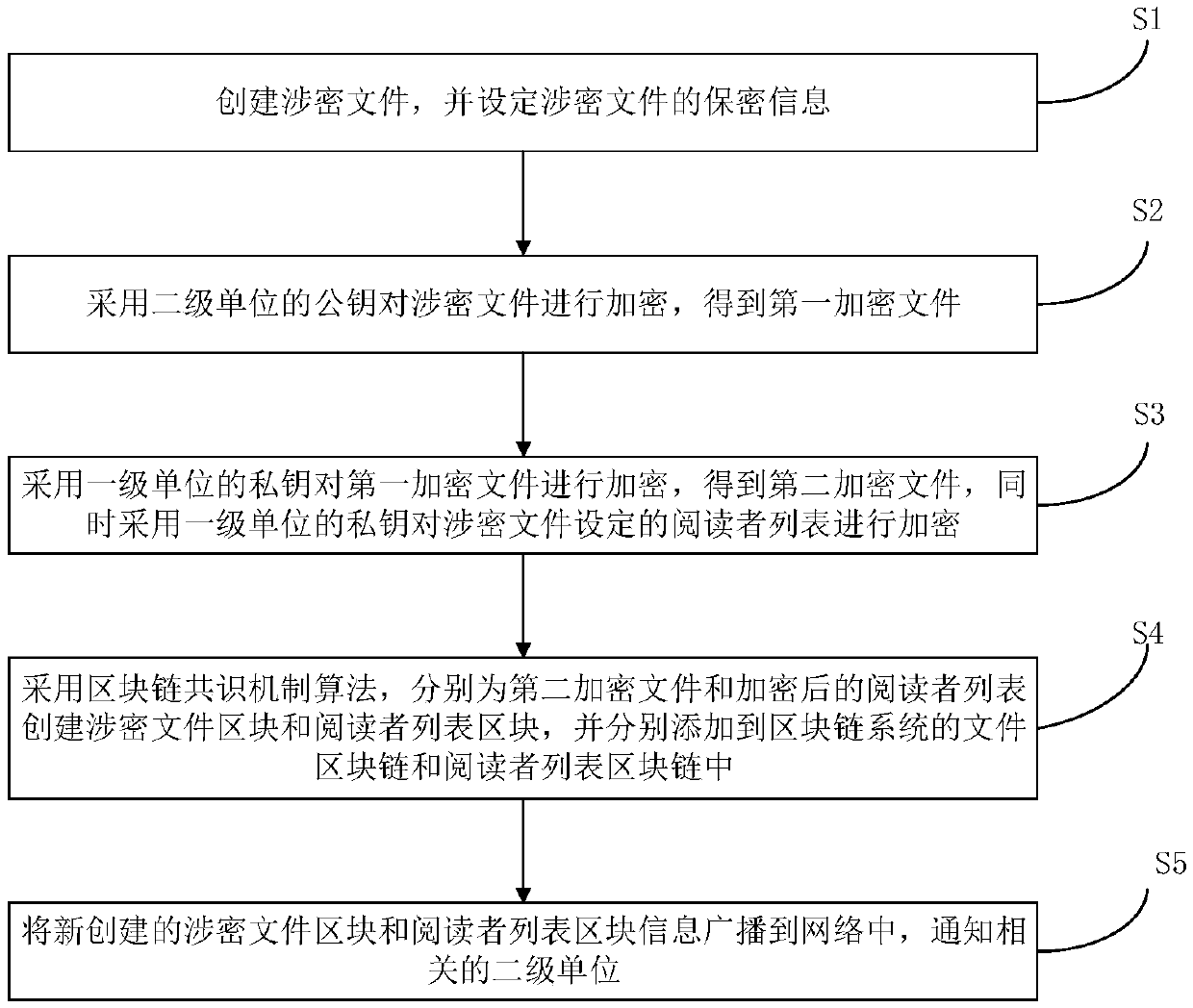
[0073] refer to figure 1 , the present embodiment provides a secret-related file management method, comprising the following steps:
[0074] S1. Create a confidential document and set the confidential information of the confidential document; the confidential information includes at least the confidentiality level, the confidentiality period, the list of document readers and the limit of reading times; the document reader list refers to the readers who can read the document The list information, the reading limit refers to the limit on the number of times each reader can read the file, which can be set to any number of times, for example...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com