Threat Intelligence Exploitation and Reproduction Method Based on Statistical Learning
A statistical learning and intelligence technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as model degradation and prediction accuracy decline, and achieve the effect of improving accuracy and alleviating model degradation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
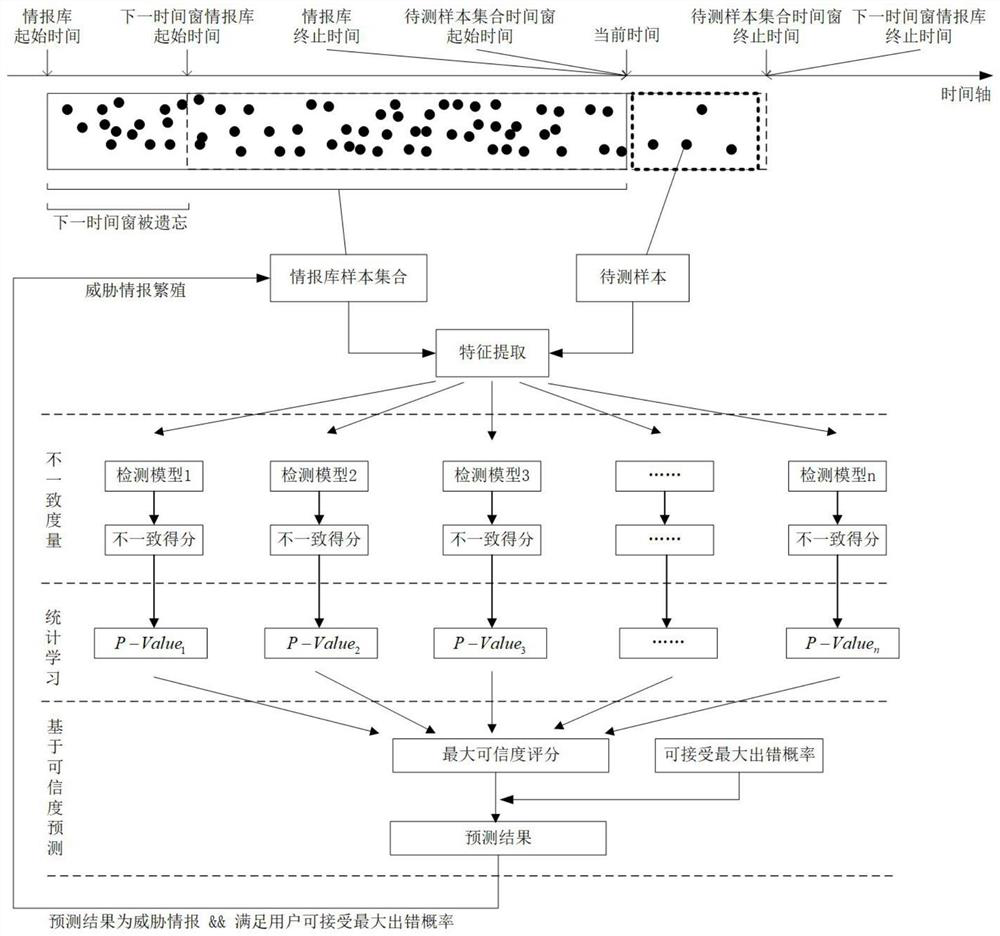
[0056] The present invention takes the detection of malicious domain names as an example for specific description. Any detection model based on a fixed threshold can be used in this method. The method flow is as follows figure 1 In this embodiment, two detection models, XGBoost and LSTM, are used as examples to illustrate, and the specific introduction is as follows:
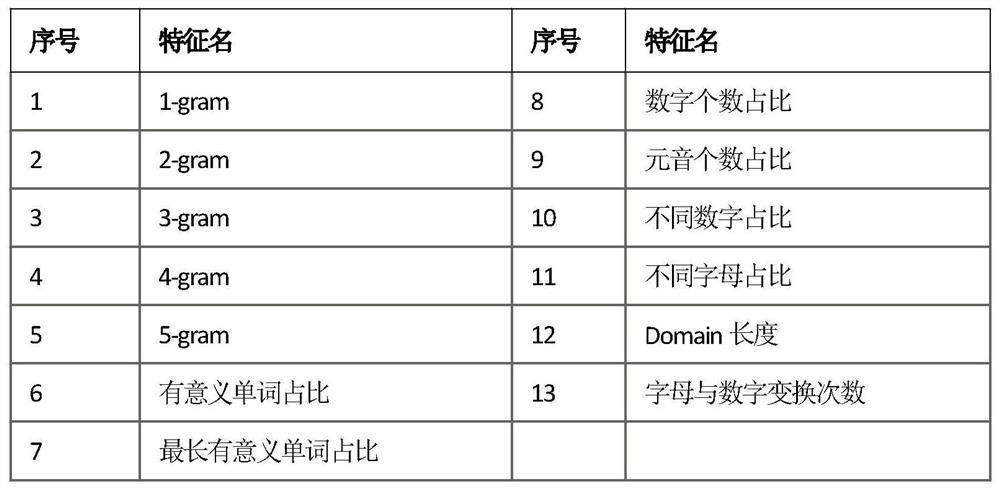
[0057] XGBoost is a Boosting algorithm based on GBDT gradient boosting decision tree. It first uses a simple model to fit the data to obtain a more general result, and then continuously adds simple models to the model. As the number of trees increases, the complexity of the entire model gradually becomes higher and approaches the complexity of the data itself. By building and fitting the CART tree of different eigenvalue sets of intelligence, the scoring of the tree structure is carried out. This method has good learning effect, fast speed, can handle large-scale data, and can effectively score massive threat i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com