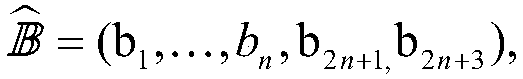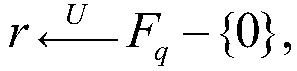Verifiable semantic security multi-keyword search method in cloud storage
A keyword search and semantic security technology, applied in the field of encrypted search, can solve problems such as untrustworthy key generation center, unclear authorization description, and no query result verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
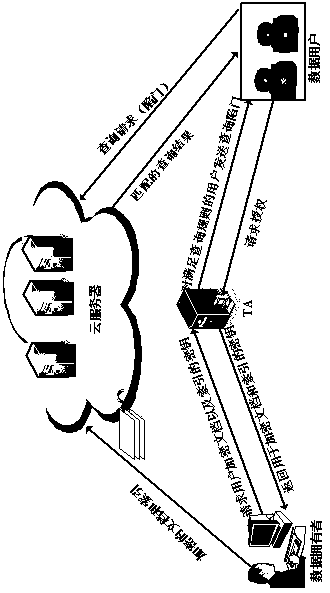
[0161] Below we combine as figure 1 The system structure diagram shown and the electronic medical record EMR shown in Table 1 illustrate that the technical solution of the present invention executes a multi-keyword search process for electronic medical records.
[0162] Table 1 Electronic Medical Records
[0163]
[0164]
[0165] Step 1, system initialization, TA is responsible for the generation of the system key, the specific process is as follows in steps 1.1-1.3:
[0166] Step 1.1: TA runs the dual vector space generation algorithm δ dpvs (1 λ ,N) output a group N is the dimension of the vector space, N=2n+3, and n is the length of the attribute vector and the query vector.
[0167] Step 1.2: TA runs the orthogonal basis generation algorithm δ ob (1 λ ,N)N=2n+3, output is an orthonormal basis, that is, for all Satisfy δ when i=j i,j = 1, otherwise δ i,j =0.
[0168] Step 1.3: TA runs initialization algorithm Setup(1 λ ,2n+3), return system publi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com