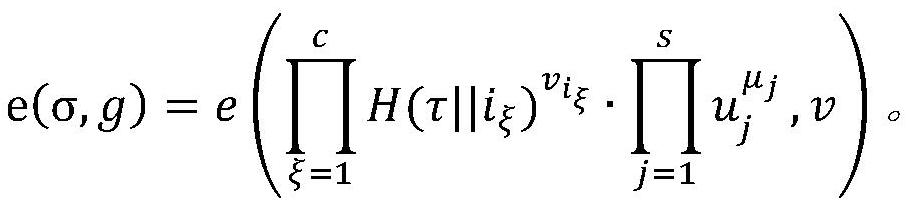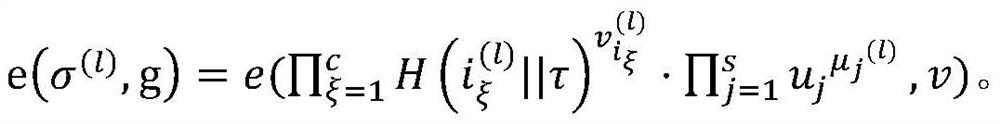Blockchain-based public cloud storage data integrity verification method
A technology for integrity inspection and data storage, applied in digital transmission systems, user identity/authority verification, secure communication devices, etc., can solve problems such as destroying public inspection functionality, destroying user data, and internal security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Applied to bilinear mapping in the present invention, its description is as follows:
[0016] A bilinear map e:G×G→G T , where G and G T They are multiplicative cyclic groups, their order is a prime number p, their generator is g, and e has bilinearity, computability and non-degeneration.
[0017] (1) System initialization stage
[0018] user Generate system parameters in the following steps:
[0019] 1. According to security parameters user Select the corresponding group G, G T And the corresponding bilinear map G×G→G T .
[0020] 2. From Z p Randomly select an α as the private key, and calculate v=g α As a public key, where g is a generator of G.
[0021] 3. Choose a pseudorandom function f() and a pseudorandom permutation function π().
[0022] 4. Select the appropriate hash function H:{0,1} * →G,h:{0,1} * → Z p ,h 1 :{0,1} * → π.key, h 2 :{0,1} * →f.key, where π.key is the key space of the pseudo-random permutation function π(), and f.key is th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com