An attack path reconstruction method based on similarity computation
A similarity calculation and attack path technology, applied in complex mathematical operations, platform integrity maintenance, file system types, etc., can solve the problems of insufficient real-time processing of network threats and backward analysis methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
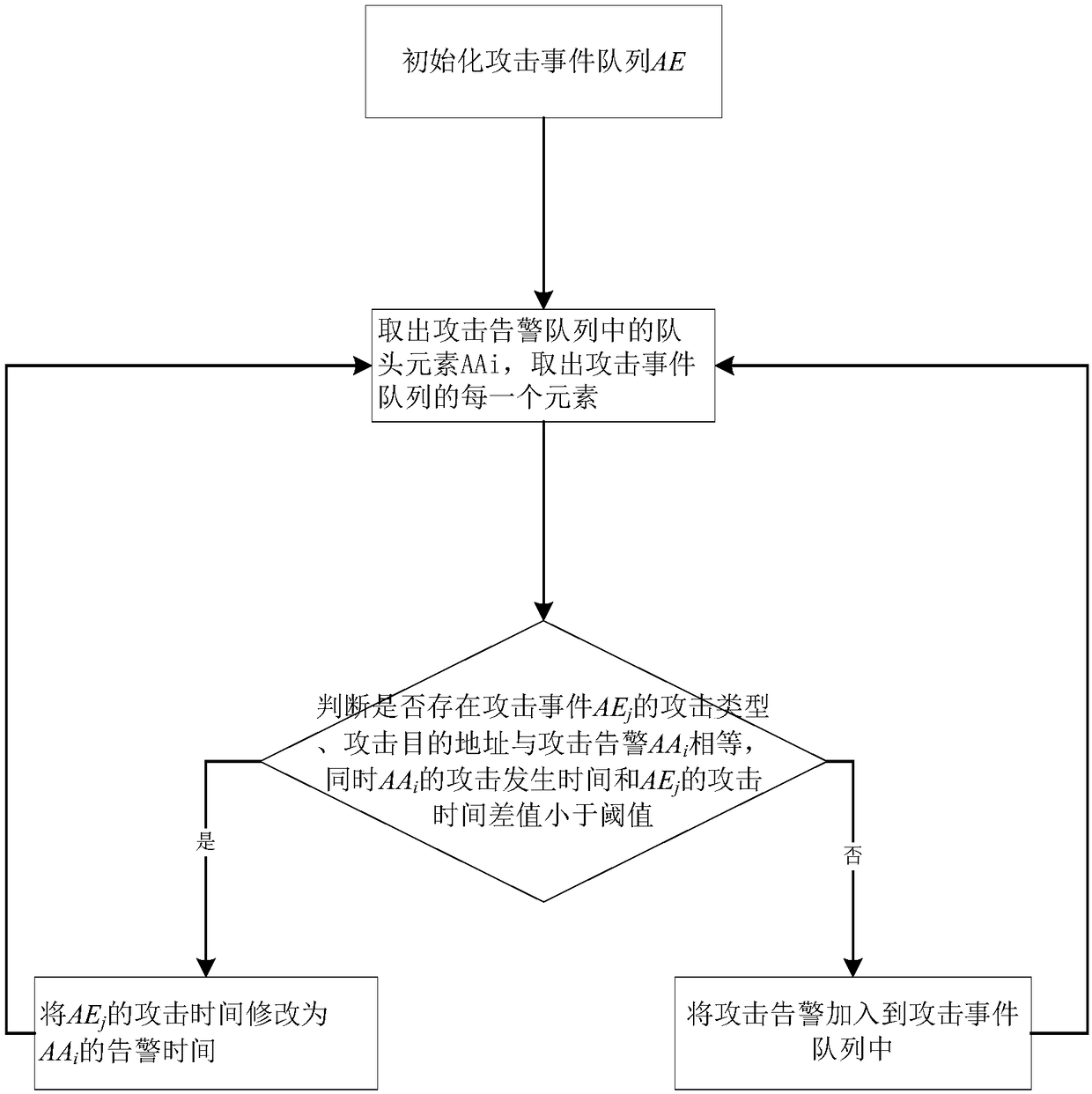
[0041] see Figure 1-Figure 4 , the present invention comprises the following steps:
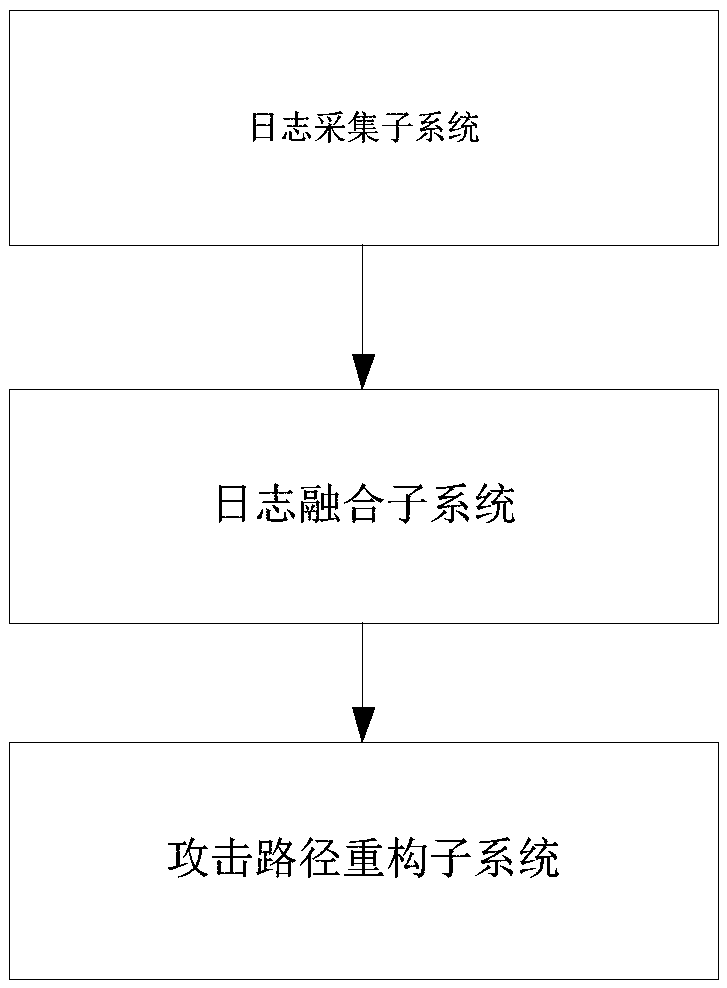
[0042] Step 1, build an attack path reconstruction system including log collection subsystem, log fusion subsystem and attack path reconstruction subsystem;
[0043] Step 2, start the attack path reconstruction system;
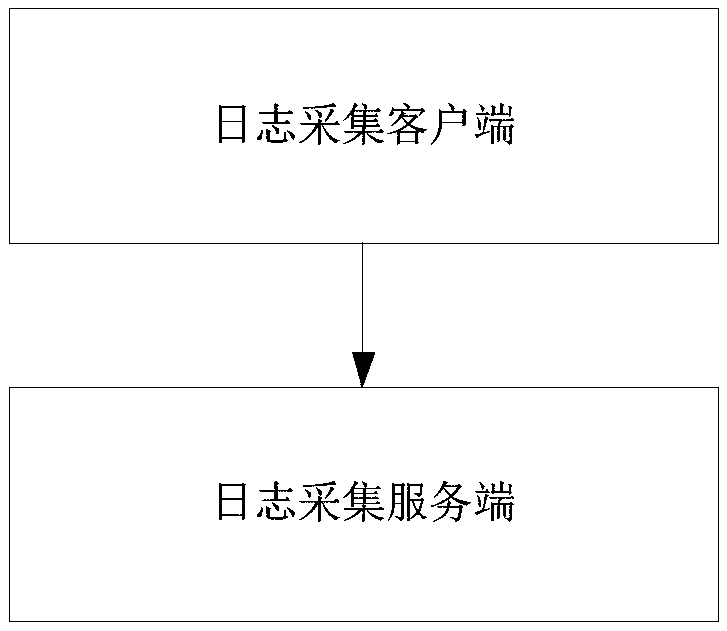
[0044] Step 3, the log collection subsystem collects network logs, host logs and application program logs; then judges whether there is an attack alarm in the log records according to feature matching, and stores the attack alarm in the attack alarm queue AA. The log collection subsystem includes a log collection client and a log collection server. The log collection client collects network logs, host logs, and application logs to the log collection server through the syslog protocol; the log server judges whether there is an attack alarm in the log records based on the feature matching method, and stores the attack alarm in the attack alarm In queue AA.
[0045] In this...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com