A network traffic anomaly detection and defense method
A technology of abnormality detection and network traffic, applied in the direction of transmission system, electrical components, etc., can solve the problems of no test, small amount of communication data, reduction of communication amount and controller load, etc., to achieve the effect of abnormal change
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings, but the embodiments of the present invention are not limited thereto.
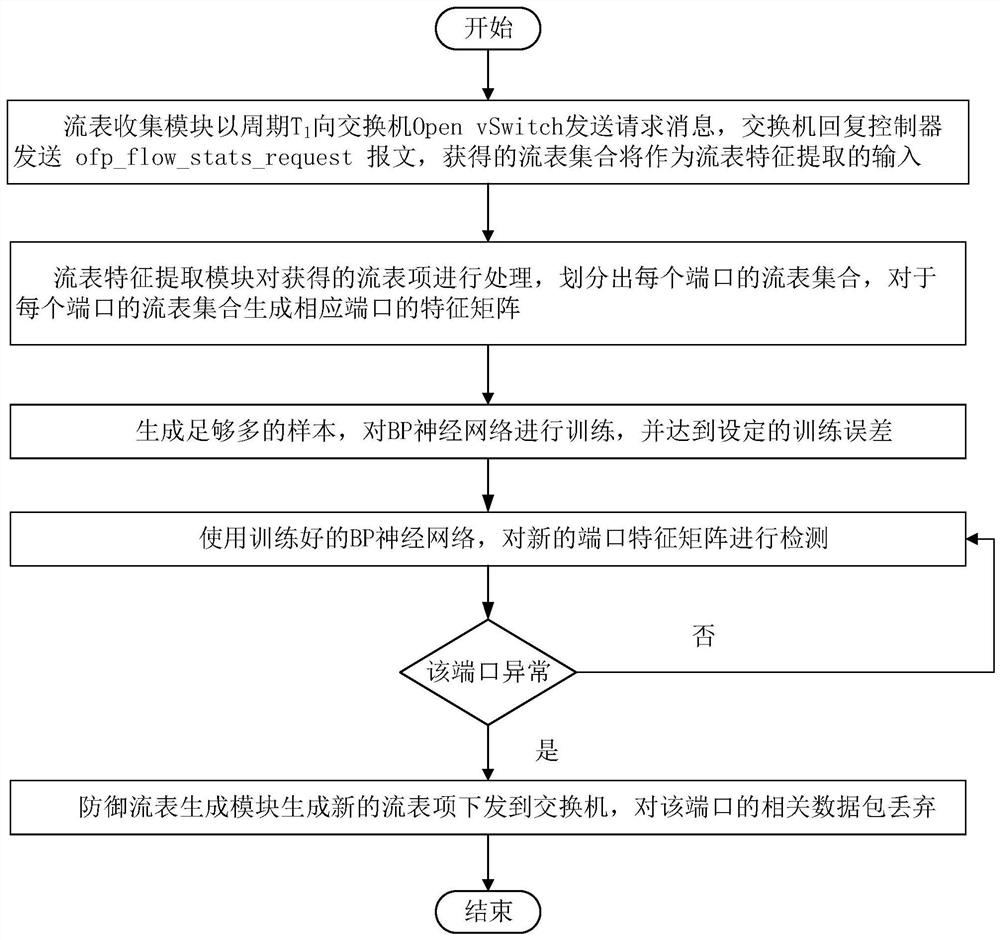
[0034] Such as Figure 1~4 As shown, a network traffic anomaly detection and defense method includes the following steps:
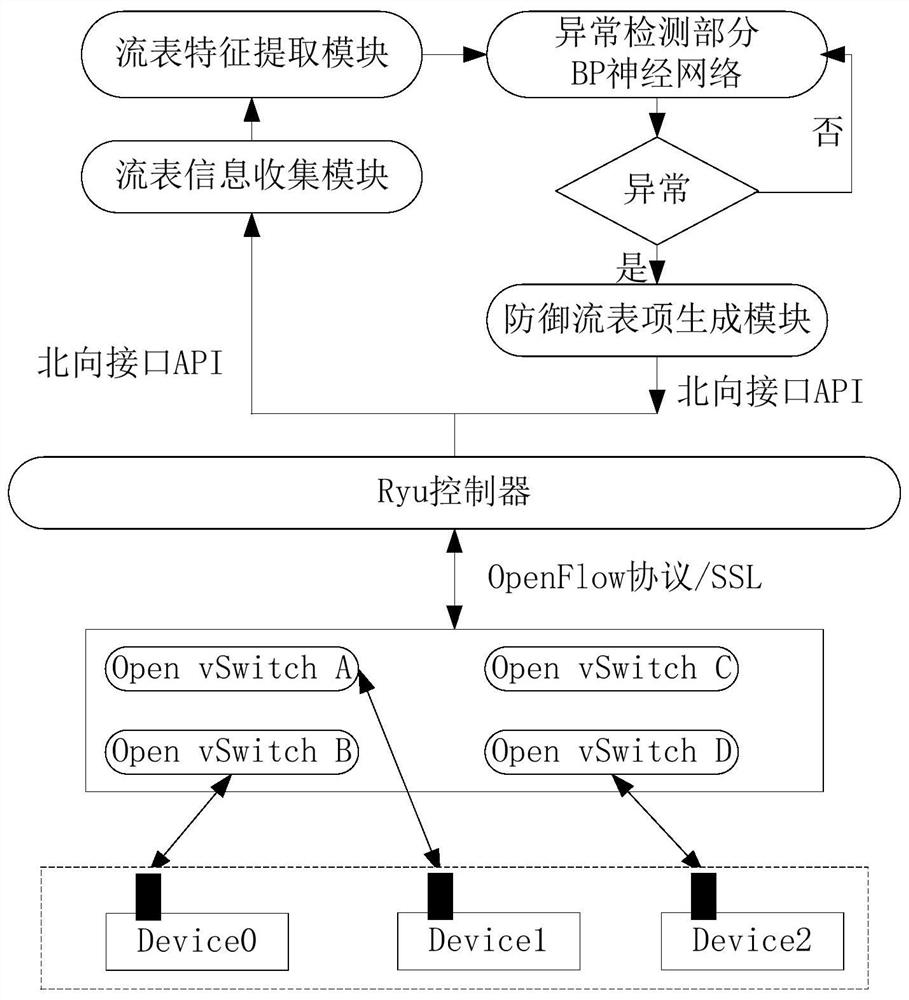
[0035] Step one, such as figure 1 As shown in , establish a network traffic anomaly detection and defense architecture, and collect flow entry information;
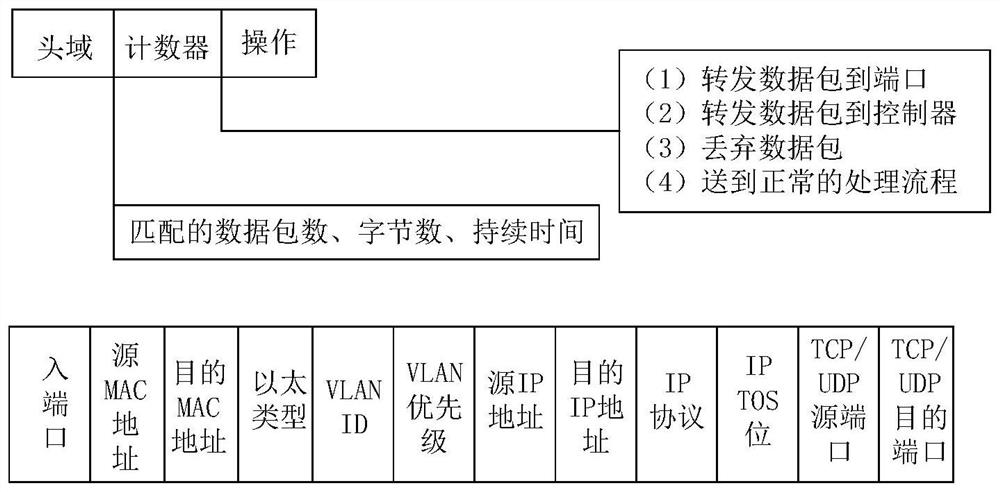
[0036] Wherein, the network traffic anomaly detection and defense framework includes a Ryu controller unit, an anomaly detection unit based on BP neural network, an OpenvSwitch switch and an access device based on the OpenFlow protocol, and the Ryu controller unit includes a flow table information collection module, A flow table feature extraction module and a defense flow table item generation module, the flow table information collection module requests all flow table item information from ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com