An anti-over-crawler method based on sdn
An anti-crawler and crawler technology, which is applied in the field of information security, can solve the problems that the security of sensitive data in the data center cannot be guaranteed, and the illegal crawler has no targeted defense means, so as to achieve the effect of protecting data in sensitive areas.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
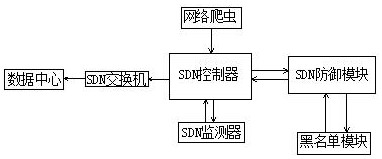
[0030] A kind of SDN-based anti-excessive crawler method, comprises the following steps:
[0031] a. Build an anti-crawler SDN environment
[0032] Build an anti-crawler SDN environment in the data center;
[0033] b. Deploy the sensitive data area on the SDN controller
[0034] By writing the API, the SDN controller will grab the robots.txt file disclosed by each newly added server, obtain the formulated crawler access rules, and integrate the rules about the same User_Agent, and integrate the Disallow page directory Define it as a sensitive data area, and deploy this information on the SDN controller;
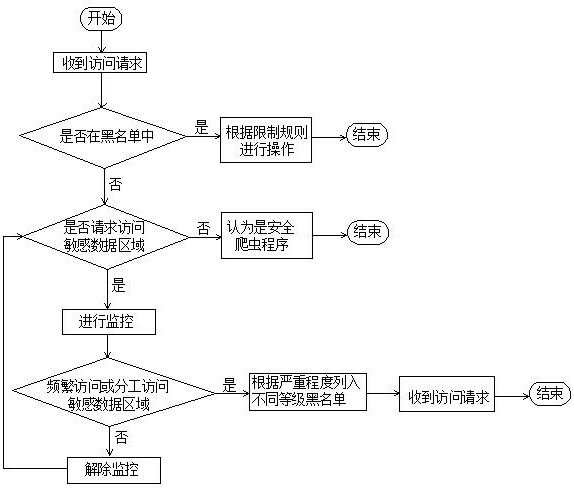
[0035] c. Blacklist level restriction
[0036] Monitor all crawlers that request access to the network through the SDN monitor. If the IP is in the blacklist, the access operation will be restricted; if there is no request to access any sensitive data area, it will be defined as a safe crawler; if there is a crawler When a program tries to access the sensitive data area s...
Embodiment 2
[0039] A kind of SDN-based anti-excessive crawler method, comprises the following steps:
[0040] a. Build an anti-crawler SDN environment
[0041] Build an anti-crawler SDN environment in the data center;
[0042] b. Deploy the sensitive data area on the SDN controller
[0043] By writing the API, the SDN controller will grab the robots.txt file disclosed by each newly added server, obtain the formulated crawler access rules, and integrate the rules about the same User_Agent, and integrate the Disallow page directory Define it as a sensitive data area, and deploy this information on the SDN controller;
[0044] c. Blacklist level restriction
[0045] Monitor all crawlers that request access to the network through the SDN monitor. If the IP is in the blacklist, the access operation will be restricted; if there is no request to access any sensitive data area, it will be defined as a safe crawler; if there is a crawler When a program tries to access the sensitive data area s...
Embodiment 3
[0049] A kind of SDN-based anti-excessive crawler method, comprises the following steps:
[0050] a. Build an anti-crawler SDN environment
[0051] Build an anti-crawler SDN environment in the data center;
[0052] b. Deploy the sensitive data area on the SDN controller
[0053] By writing the API, the SDN controller will grab the robots.txt file disclosed by each newly added server, obtain the formulated crawler access rules, and integrate the rules about the same User_Agent, and integrate the Disallow page directory Define it as a sensitive data area, and deploy this information on the SDN controller;
[0054] c. Blacklist level restriction
[0055] Monitor all crawlers that request access to the network through the SDN monitor. If the IP is in the blacklist, the access operation will be restricted; if there is no request to access any sensitive data area, it will be defined as a safe crawler; if there is a crawler When a program tries to access the sensitive data area s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com