Information matching method and device
A technology to be matched, identity information, applied in secure communication devices, homomorphic encrypted communication, digital transmission systems, etc., can solve the problem of low accuracy of matching results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
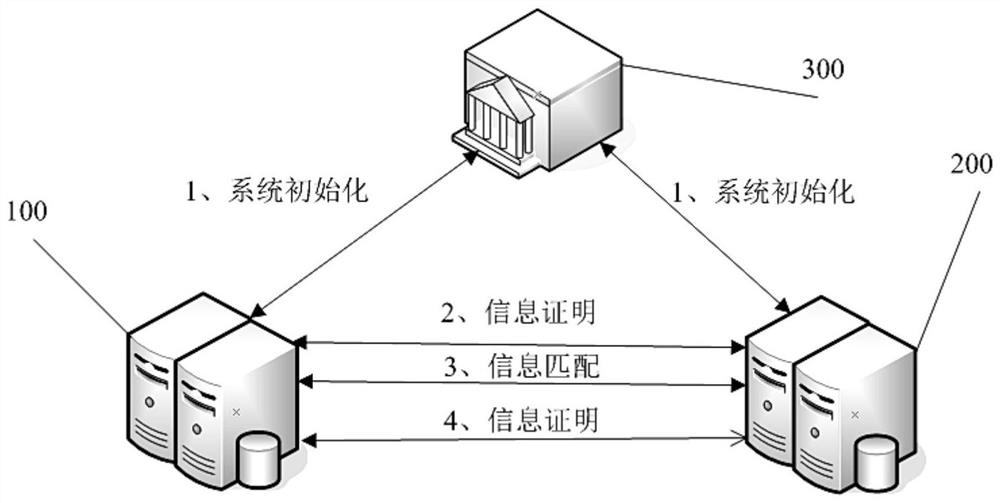
[0038] This embodiment provides an information matching method, which is applied to the matching initiator, matching receiver and trusted enterprise certification authority. Please refer to figure 1 , the method includes:
[0039] Step S101: After the matching initiator initializes the first key pair, it registers with the trusted enterprise certification authority to obtain the first digital certificate, wherein the first key pair includes the first public key and the first private key, and the first digital certificate It includes the first public key and the first identity information of the matching initiator.
[0040] Specifically, a system that includes a match initiator, a match receiver, and a trusted enterprise certification authority (ECA) can be provided, such as figure 2 As shown, the system architecture includes a matching initiator 100, a matching receiver 200, and a trusted enterprise certification authority (ECA) 300. The information matching method generally...
Embodiment 2
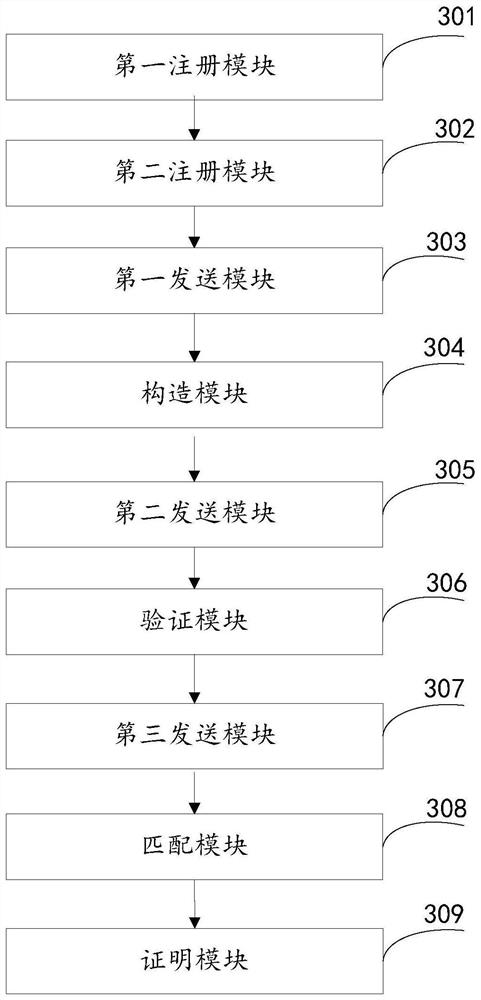
[0105] This embodiment provides an information matching device, which is applied to matching initiators, matching receivers, and trusted enterprise certification bodies. Please refer to image 3 , the device consists of:
[0106] The first registration module 301 is configured to register with a trusted enterprise certification authority after the matching initiator initializes the first key pair to obtain a first digital certificate, wherein the first key pair includes a first public key and a first private key , the first digital certificate includes the first public key and the first identity information of the matching initiator;
[0107] The second registration module 302 is used to register with the trusted enterprise certification authority after the matching receiver initializes the second key pair, and obtain the second digital certificate, wherein the second key pair includes the second public key and the second private key , the second digital certificate includes ...
Embodiment 3
[0151] Based on the same inventive concept, this application also provides a kind of computer equipment, please refer to Figure 4 , including a storage 401, a processor 402, and a computer program 403 stored in the storage and operable on the processor. The processor 402 implements the method in Embodiment 1 when executing the above program.
[0152] Those skilled in the art should understand that the embodiments of the present invention may be provided as methods, systems, or computer program products. Accordingly, the present invention can take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present invention may take the form of a computer program product embodied on one or more computer-usable storage media (including but not limited to disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com