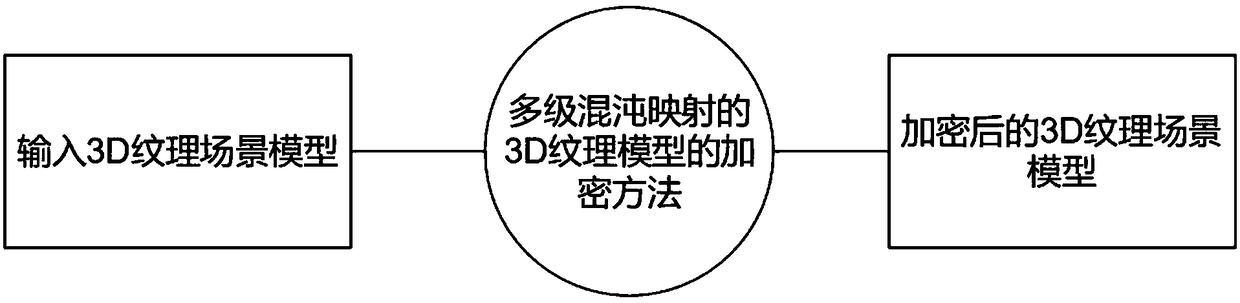
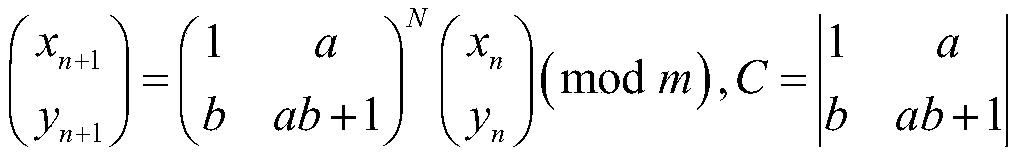Encryption method of 3D texture model based on multi-level chaotic map
A technology of texture model and chaotic mapping, which is applied in the direction of secure communication through chaotic signals, countermeasures against encryption mechanism, digital transmission system, etc. It can solve problems such as low efficiency, unsuitable for encrypting images and models, and time-consuming encryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
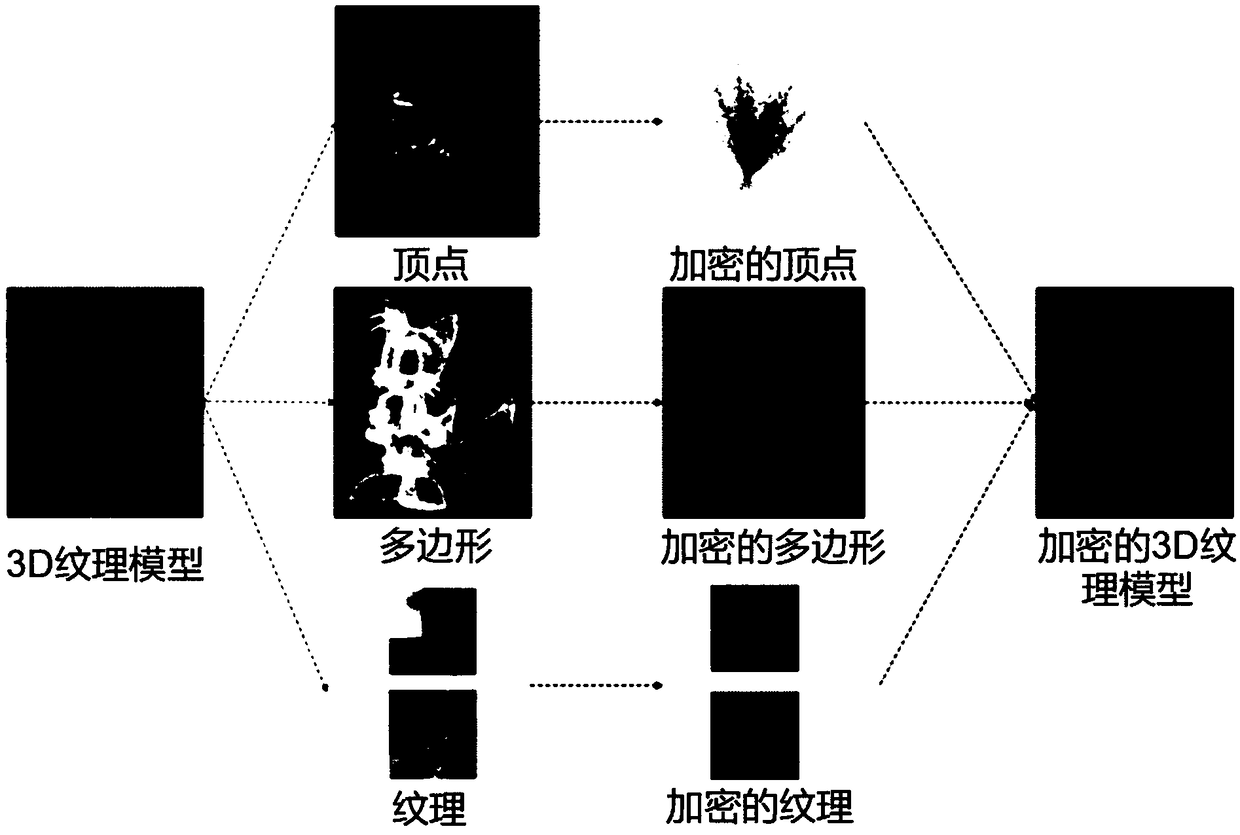
[0045] Multi-level 3D texture model encryption process:
[0046] Vertex Encryption:
[0047] As can be seen from the 3D model file, the vertices in the 3D texture model are also in the form of triplet lists:
[0048] V={(X 1 ,Y 1 ,Z 1 ),...,(X N ,Y N ,Z N )} (1)
[0049] where (X i ,Y i ,Z i ) is the 3D coordinate of the vertex and N is the number of vertices. The present invention uses 3DLu mapping to generate a random vector of size 3N:
[0050] LV={(LV 1 ,LV 2 ,LV 3 ),...,(LV 3N-2 ,LV 3N-1 ,LV 3N )} (2)
[0051] Then the elements of V and LV are multiplied accordingly, as follows:
[0052] VLV={(X 1 LV 1 ,Y 1 LV 2 ,Z 1 LV 3 ),...,(X N LV 3N-2 ,Y N LV 3N-1 ,Z N LV 3N )} (3)
[0053] The resulting new vector VLV represents the new coordinates of the vertices of the original 3D texture model:
[0054]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com