System and method based on user behavior authentication, and storage medium
A behavior and user technology, applied in the field of data processing, can solve problems such as poor user experience, waste of time, wrong passwords, etc., and achieve the effects of simplifying authentication steps, reminding risk information, and reducing frequency of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the objectives, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
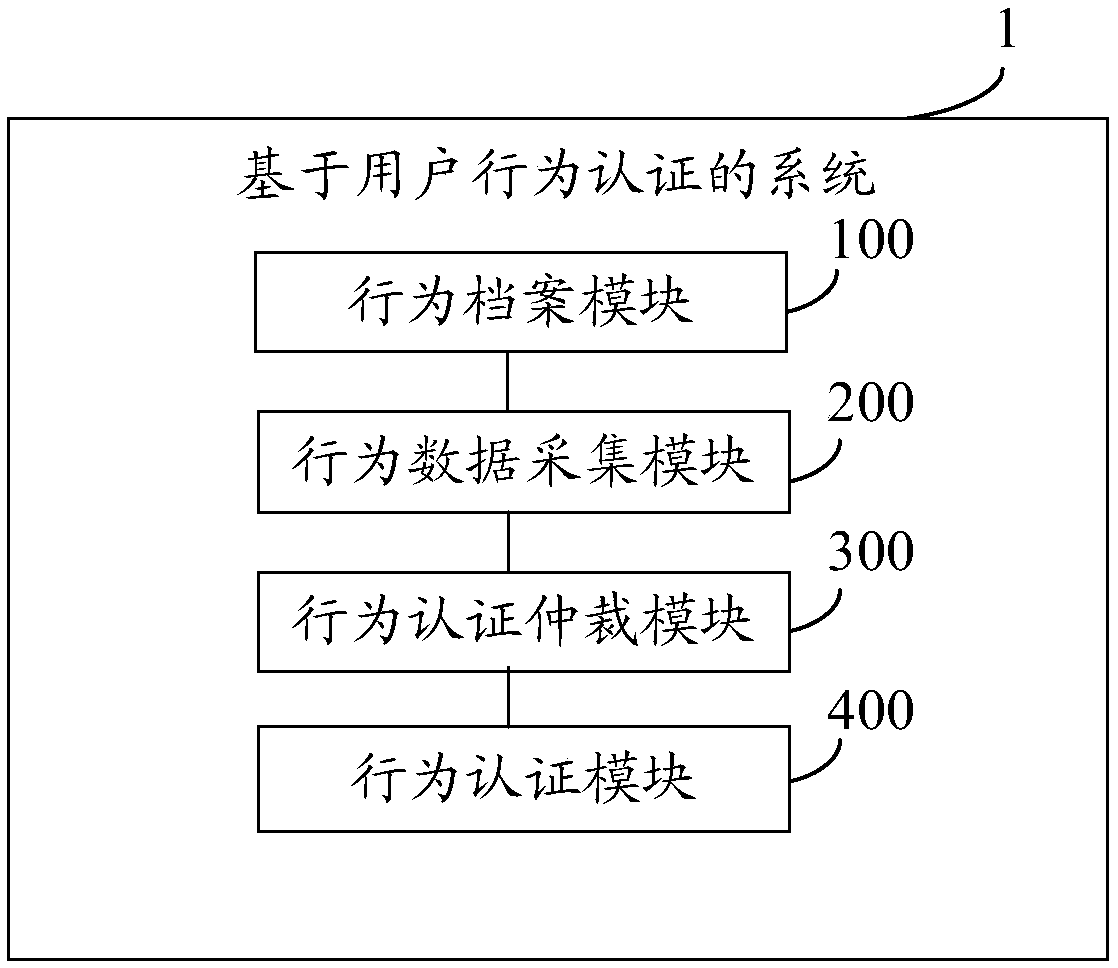
[0040] figure 1 It is a schematic structural diagram of a system 1 based on user behavior authentication according to an embodiment of the present invention. See figure 1 , The system 1 includes:
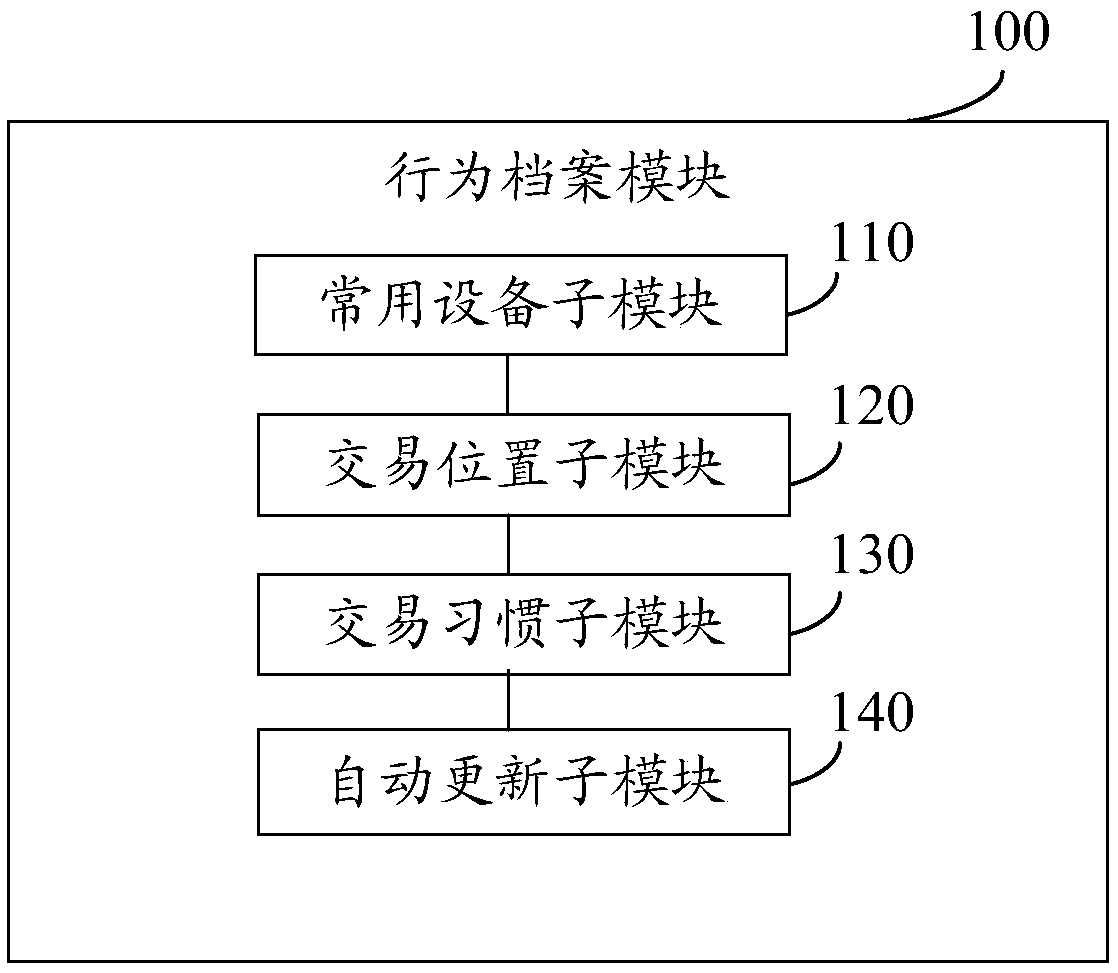
[0041] The behavior file module 100 is used to store a discrete set of data of user equipment information, geographic location information commonly used in transactions, and user transaction habits and behavior information;
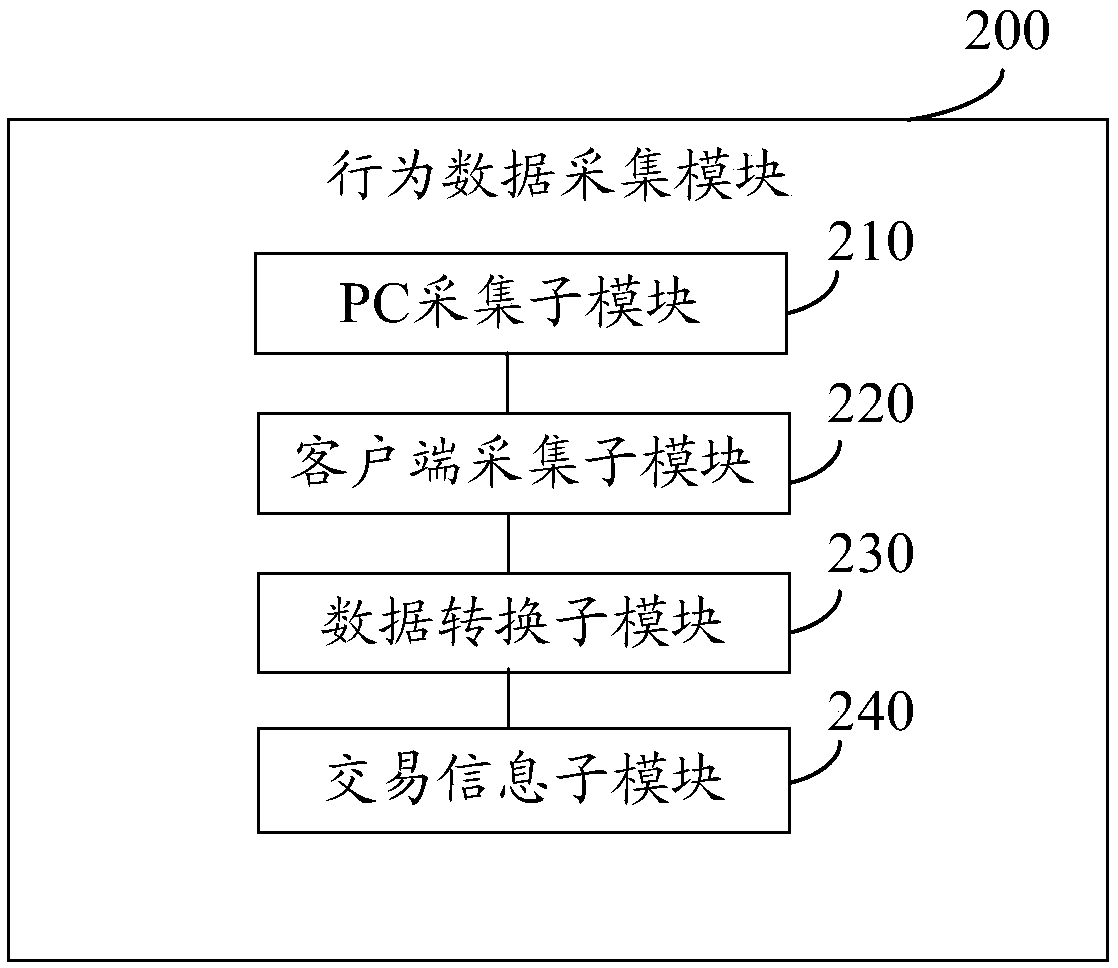
[0042] The behavior data collection module 200 is used to collect and monitor user behavior data in real time through a web page plug-in or an application client;
[0043] The behavior authentication arbitration module 300 is configured to arbitrate the data factors provided by the behavior archive module and the behavior data colle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com