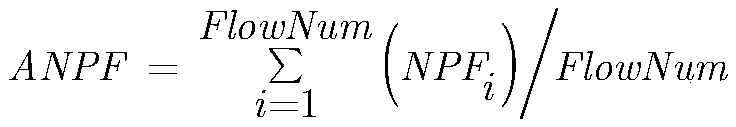DoS attack detection method oriented to software defined network
A software-defined network, software-oriented technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of slow convergence speed and long training time of SOM algorithm, and achieve the effect of real-time and accurate detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
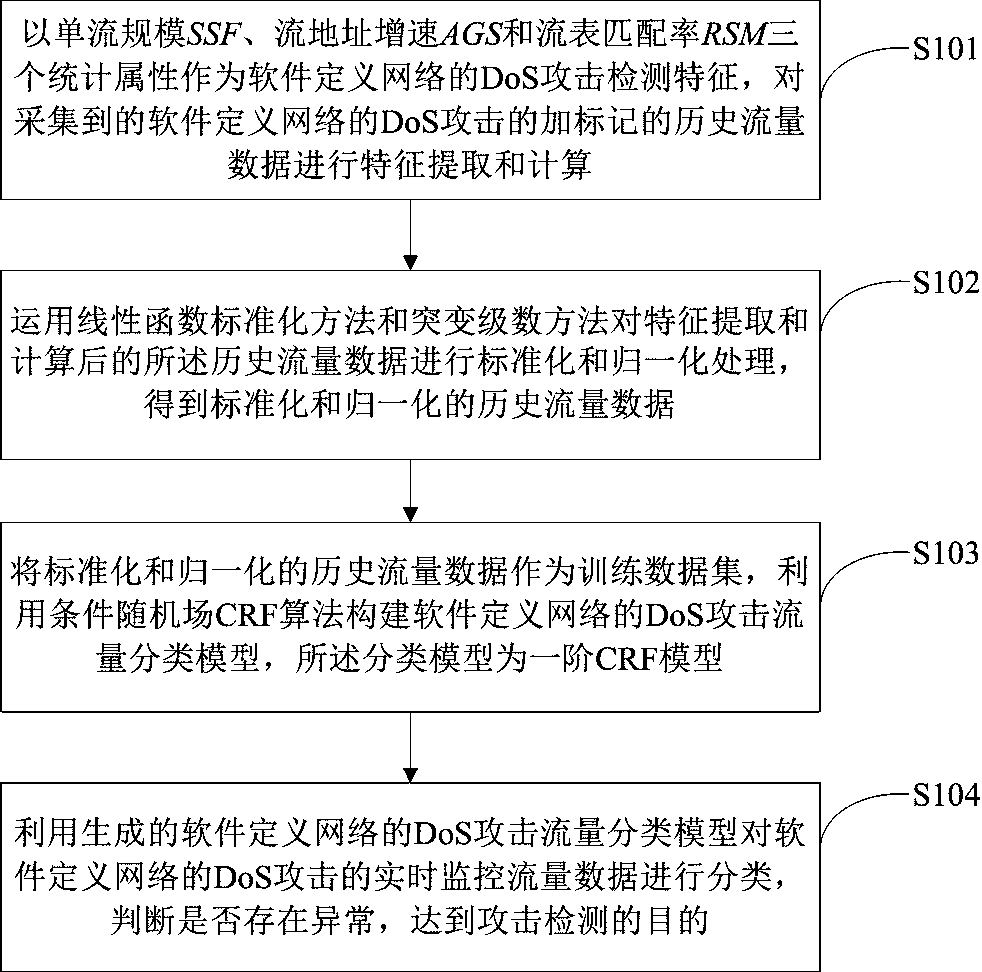
[0052] Such as figure 1 Shown, a kind of software-defined network-oriented DoS attack detection method of the present invention comprises the following steps:
[0053] Step S101: Taking the three statistical attributes of single-flow scale SSF, flow address growth rate AGS, and flow table matching rate RSM as the DoS attack detection characteristics of software-defined networks, the collected historical traffic of DoS attacks in software-defined networks is marked Data for feature extraction and calculation;
[0054] Step S102: Standardize and normalize the historical flow data after feature extraction and calculation by using the linear function standardization method and the mutation progression method to obtain standardized and normalized historical flow data;
[0055] Step S103: using the standardized and normalized historical traffic data as a training data set, and constructing a DoS attack traffic classification model for a software-defined network using a conditional ...
Embodiment 2
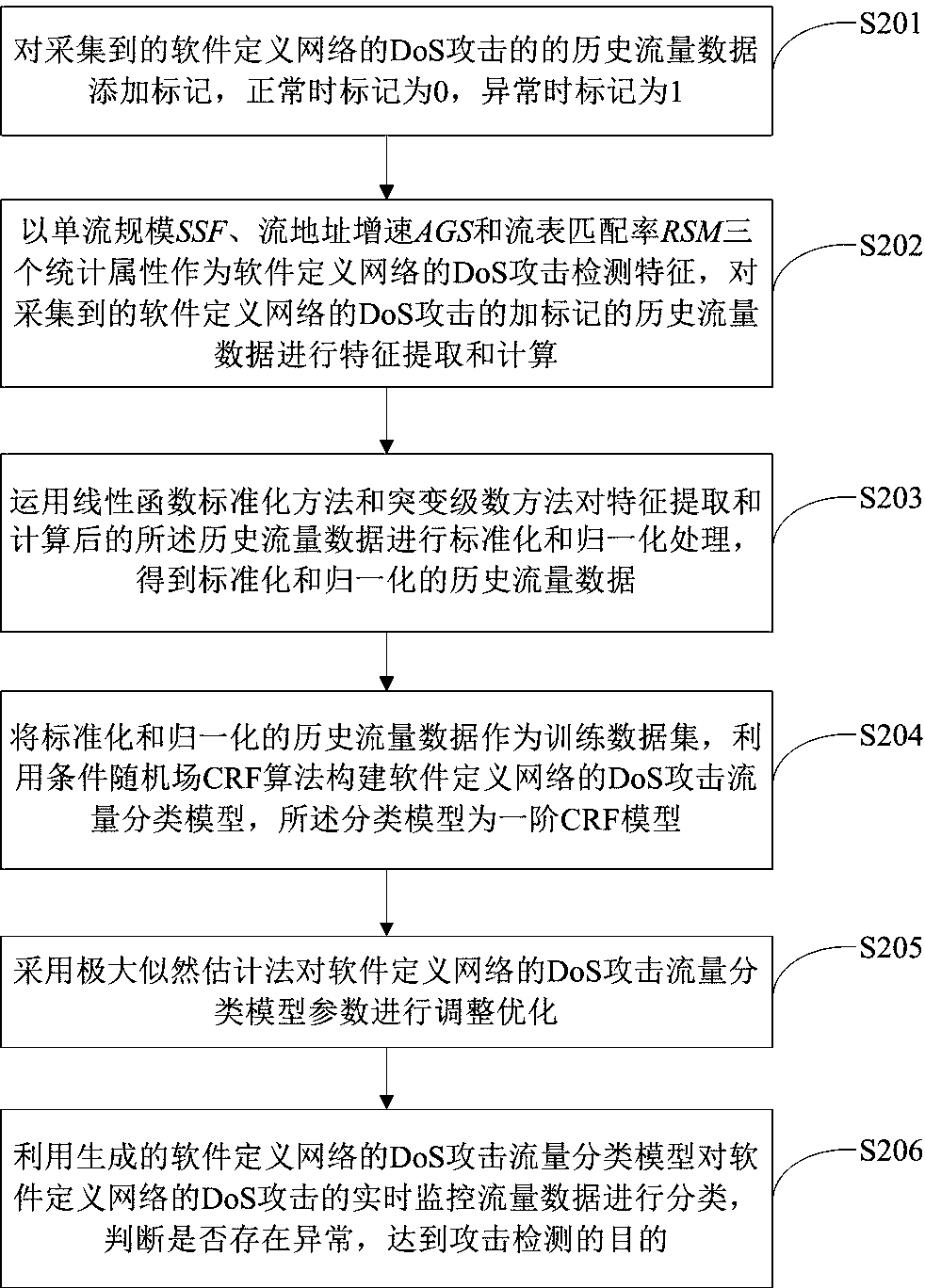
[0058] Such as figure 2 As shown, another DoS attack detection method for software-defined network of the present invention comprises the following steps:
[0059] Step S201: Add a mark to the collected historical traffic data of the DoS attack of the software-defined network, mark it as 0 when it is normal, and mark it as 1 when it is abnormal.
[0060] Step S202: Using the three strongly representative statistical attributes of single-flow scale SSF, flow address growth rate AGS, and flow table matching rate RSM as the DoS attack detection features of the software-defined network, the collected DoS attacks of the software-defined network Marked historical traffic data for feature extraction and calculation;
[0061] The single-flow scale SSF (Size of a Single Flow) describes the size of each data flow entering the SDN network, including two attribute parameters of the number of flow packets and the number of flow bytes, the average value of the number of flow packets ANPF ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com