Security implementation method of fingerprint module in alarm controller
An implementation method and controller technology, applied in the direction of acquiring/arranging fingerprints/palmprints, instruments, characters and pattern recognition, etc., can solve the problems that the host is vulnerable to attacks and the security of the alarm system is reduced, and achieve high usability and Practicality, avoiding less secure, preventing replacement effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further described below in conjunction with the accompanying drawings.
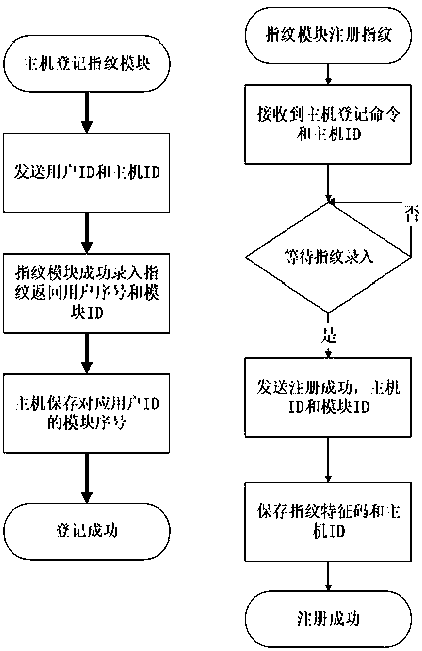
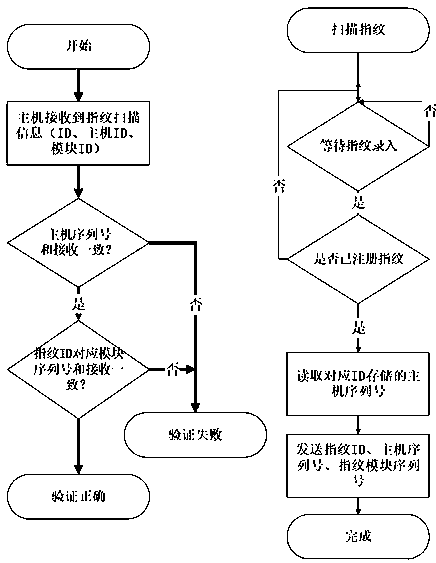
[0017] A method for implementing security of a fingerprint module in an alarm controller, characterized in that: comprising: the fingerprint module collects fingerprint information and extracts a fingerprint ID generated by a fingerprint feature code in the fingerprint information, and combines the extracted fingerprint ID with an associated alarm host ID information is sent to the alarm host at the same time. After receiving the fingerprint ID information and the alarm host ID information, the alarm host judges whether the received fingerprint ID matches the pre-stored fingerprint information, and if so, determines that the fingerprint verification is successful.
[0018] Further, the alarm host is associated with at least one fingerprint module; the associated fingerprint module ID is stored in the alarm host.
[0019] Further, it also includes registering the user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com