Information Service Entity Identity Quick Revocation Method
An information service and identity identification technology, applied in the field of information security, can solve the problems of management systems that have not used identity identification, complex calculations, and lack of real-time performance, so as to improve manageability, fast revocation speed, and efficient unified management and the effect of certification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
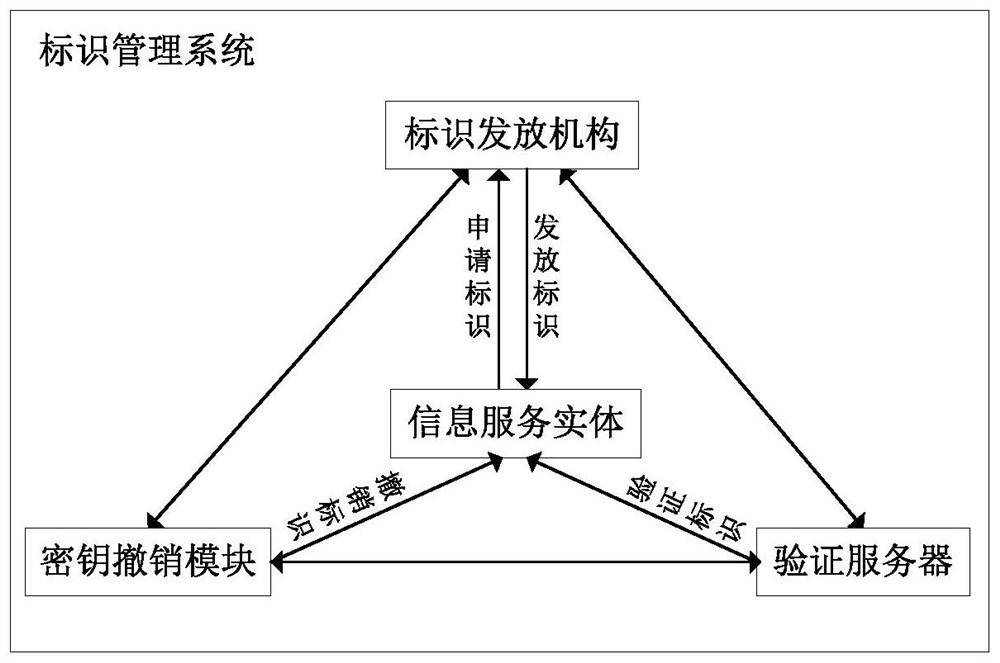
[0027]At present, information service has penetrated into every field of society and is playing an increasingly important role. While abundant network information service resources bring great convenience to people, security problems are also increasing day by day. In view of the lack of management and verification mechanisms for information services in the current Internet environment, poor behavior supervision and traceability, etc., the identity management system of information service entities and the rapid revocation method of identity marks are important technologies to realize the credibility of information services in the network Assure. However, the current existing identity management system cannot quickly revoke invalid or illegal identities. The commonly used revocation technology is to attach the validity period of the identity to the public key of the entity, which not only needs to know the expiry date of the validity period in advance, but also Not real-time. ...
Embodiment 2
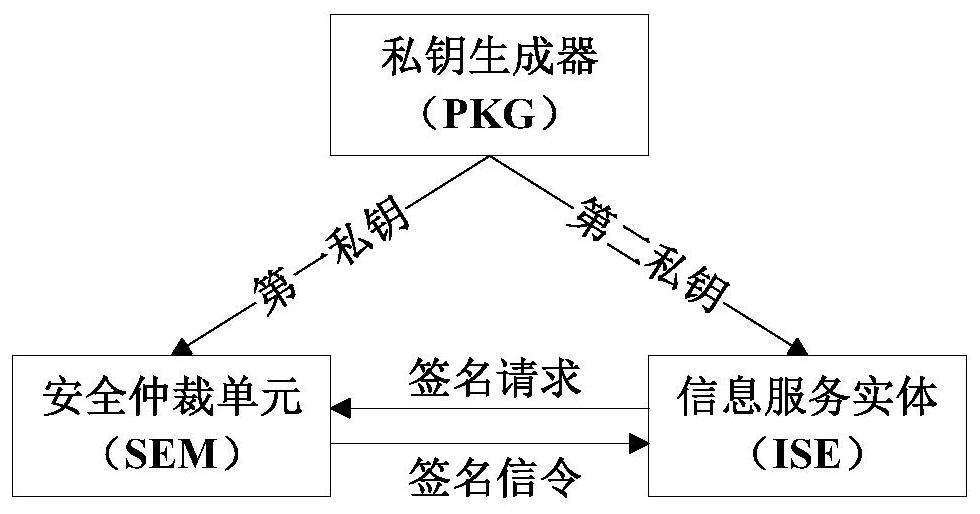
[0032] The identity management system of the information service entity is the same as that in Embodiment 1, see figure 2 , in the present invention, the private key generator PKG located in the identification issuing organization divides the private key of the information service entity ISE into two parts, and sends the first private key to the security arbitration unit SEM in the key revocation module for safekeeping, The second private key is sent to the information service entity ISE for storage. The information service entity ISE sends a signature request to the security arbitration unit SEM, and the security arbitration unit SEM returns a signature signaling to the information service entity ISE, and revokes the information service entity by ordering the security arbitration unit SEM to stop sending signature signaling to the information service entity ISE The signature capability of the ISE revokes the identity of the information service entity ISE.
[0033] In the pr...
Embodiment 3
[0035] The present invention is also a method for quickly revoking the identity of an information service entity, which can be realized on the above-mentioned identity management system of the information service entity, and can also be realized by adding a security arbitration unit to other identity management systems. If the identity management system of the information service entity is implemented, the identity management system of the information service entity is the same as Embodiment 1-2.
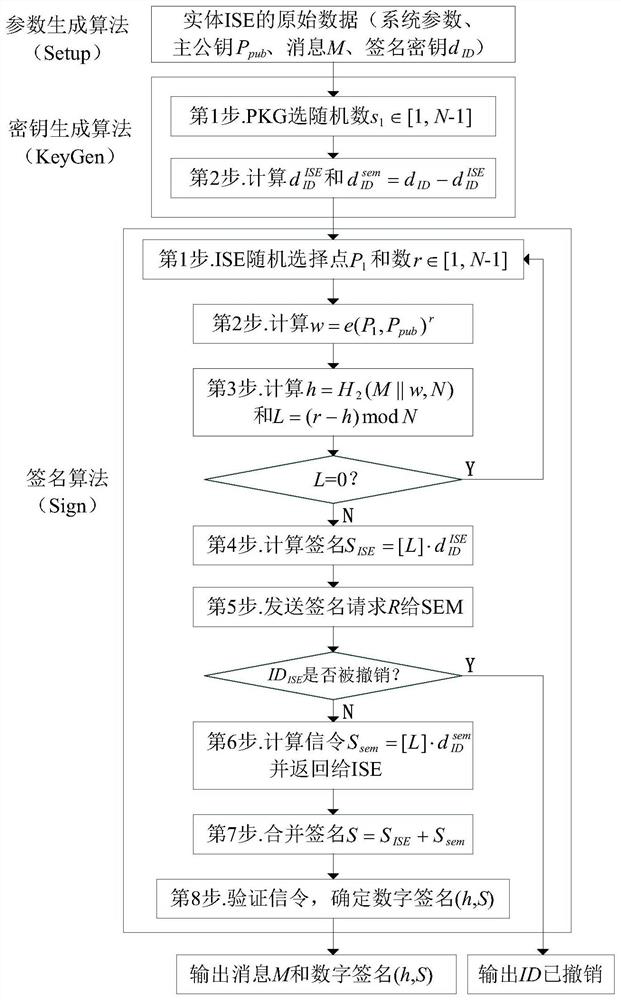
[0036] see image 3 and Figure 4 , the method for quickly revoking the identity of the information service entity of the present invention includes the following steps:
[0037] Step 1: System initialization: use the parameter generation algorithm (Setup) to realize system initialization, see image 3
[0038] The private key generator PKG generates a random number s∈[1,N-1] as the system master key, and substitutes the system master key s into the system public key generation f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com