Hash table building method based on cuckoo hash and Bloom filter
A Bloom filter and filter table technology, applied in database indexing, structured data retrieval, etc., to reduce selection restrictions, improve space utilization, and high flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
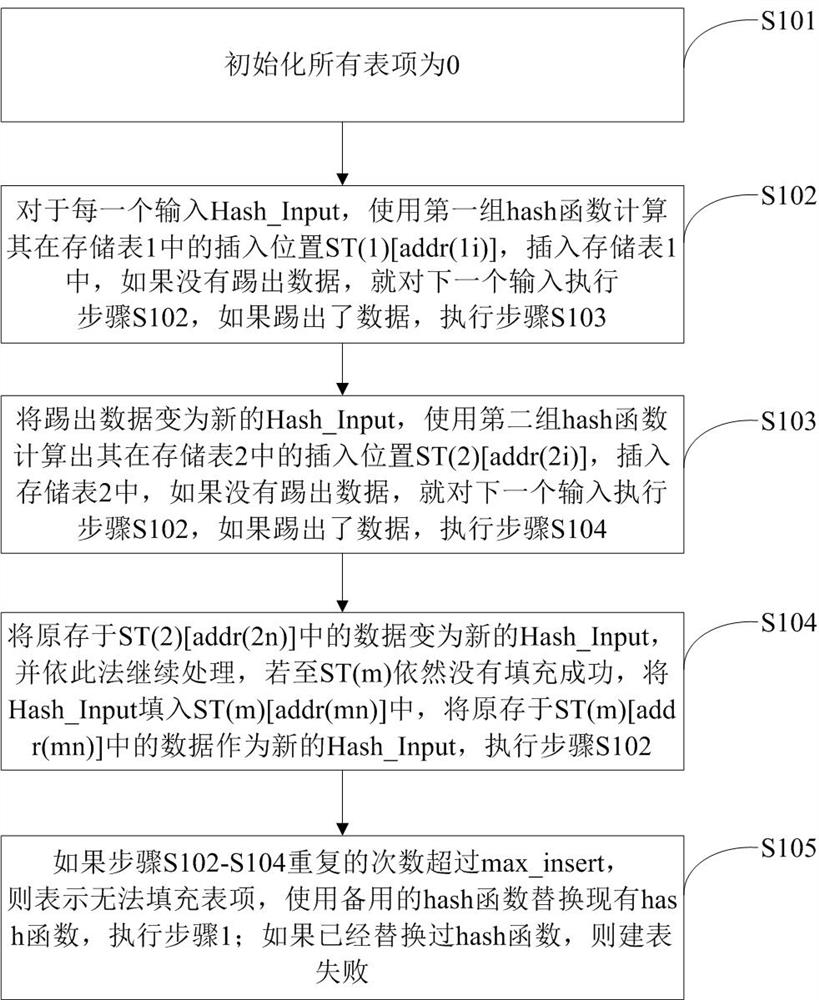
[0032] Such as figure 1 As shown, a Hash table building method based on cuckoo hash and Bloom filter of the present invention, the method divides the storage space into m groups, each group includes a storage table and n filter tables, that is, there are m Storage table, corresponding to ST(1), ST(2)...storage table ST(m), that is, corresponding to storage table 1, storage table 2...storage table m; there are m*n filter tables, corresponding to FT(11 ), FT(12)...FT(1n), FT(21), FT(22)...FT(2n),..., FT(m1), FT(m2)...FT(mn), which correspond to the first group The 1st filter table, the 1st group 2nd filter table... the 1st group nth filter table, the 2nd group 1st filter table, the 2nd group 2nd filter table... the 2nd group nth filter table , ..., the first filter table of the mth group, the second filter table of the mth group ... the nth filter table of the mth group; the length of the storage table is 2 k , the width is k bits; the length of the filtering table is 2 k , t...
Embodiment 2
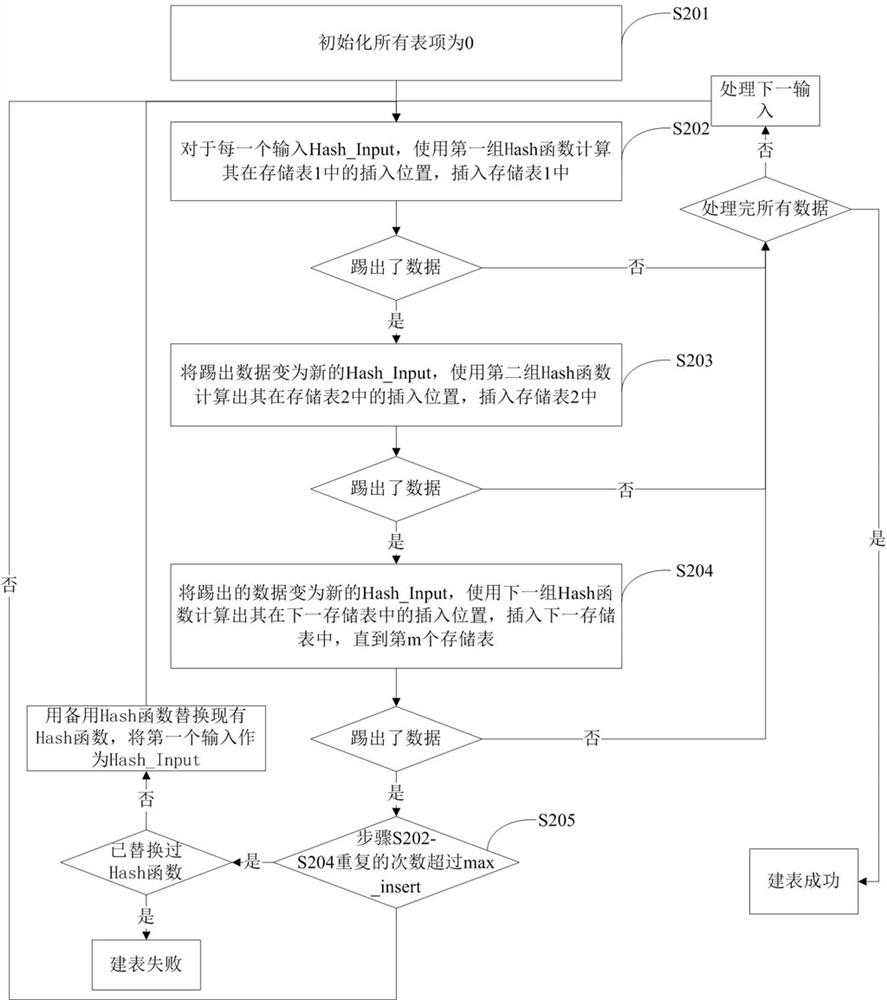
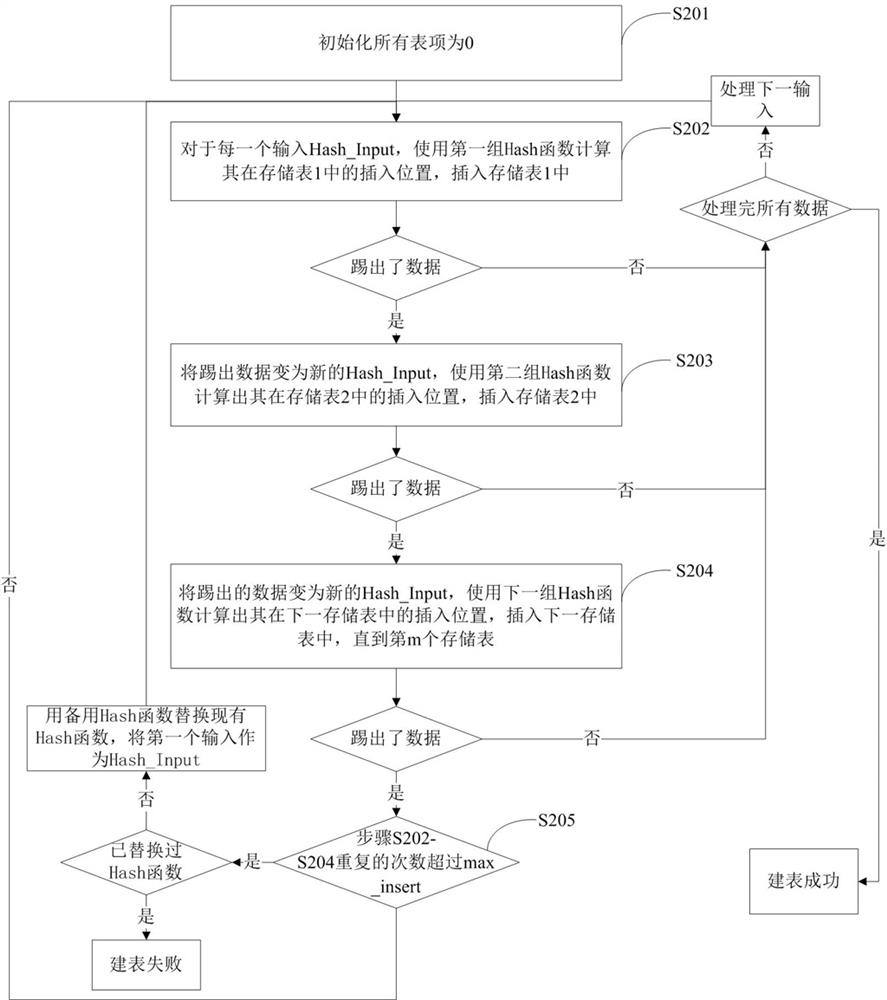
[0040] Such as figure 2 As shown, another Hash table building method based on cuckoo hash and Bloom filter of the present invention.
[0041] The method divides the storage space into m groups, each group includes a storage table and n filter tables, there are integers i∈[1,m], integers j∈[1,n], and the expression of the storage table is ST (i), the representation of the filter table is FT(ij); that is, there are m storage tables, corresponding to ST(1), ST(2) ... storage table ST(m), that is, corresponding to storage table 1 and storage table 2 ...storage table m; there are m*n filter tables, corresponding to FT(11), FT(12)...FT(1n), FT(21), FT(22)...FT(2n),...,FT(m1 ), FT(m2)...FT(mn), corresponding to the first filter table of the first group, the second filter table of the first group...the nth filter table of the first group, and the first filter table of the second group , the 2nd filter table of the 2nd group...the n-th filter table of the 2nd group, ..., the 1st fil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com