DPDK-based HTTP bypass blocking method
A technology of data packets and rules, applied in the field of communication networks, can solve problems such as failure, long DPI time-consuming, high failure rate, etc., and achieve the effects of rapid identification, improved processing performance, and quick response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
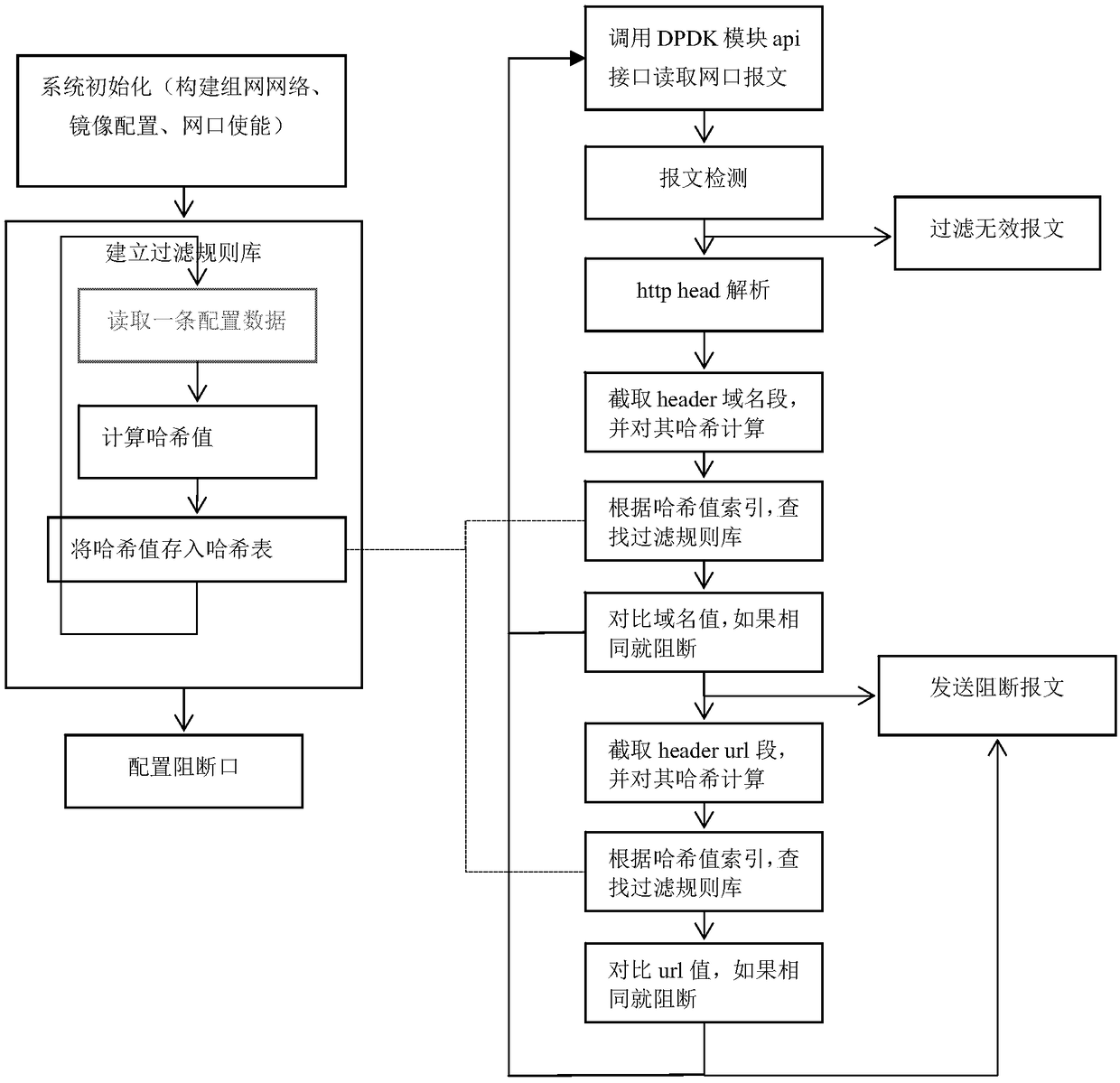
[0026] refer to figure 1 , the HTTP bypass blocking method based on DPDK, also includes the following steps:
[0027] S1: Deploy the DPDK system operating environment on the switch, including building a networking network for network communication; performing mirror configuration for capturing network data packets and performing monitoring and analysis; performing network port enabling configuration; installing the DPDK compilation module, It is used to compile the DPDK operating environment; install the driver loading module to load the DPDK driver; allocate huge page memory to realize the huge page memory configuration; through the above configuration, realize system initialization, DPDK system initialization, memory initialization and each module initialization.
[0028] S2: Establish a filtering rule library, create an http filtering library on the switch, enter f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com