Linkage response method for security monitoring system
A security monitoring and linkage technology, used in closed-circuit television systems, burglar alarms, electrical alarms, etc., can solve the problems of unstable signal, serious impact on analysis and judgment, blurring, etc., to improve the camera effect and avoid storage capacity. limited effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
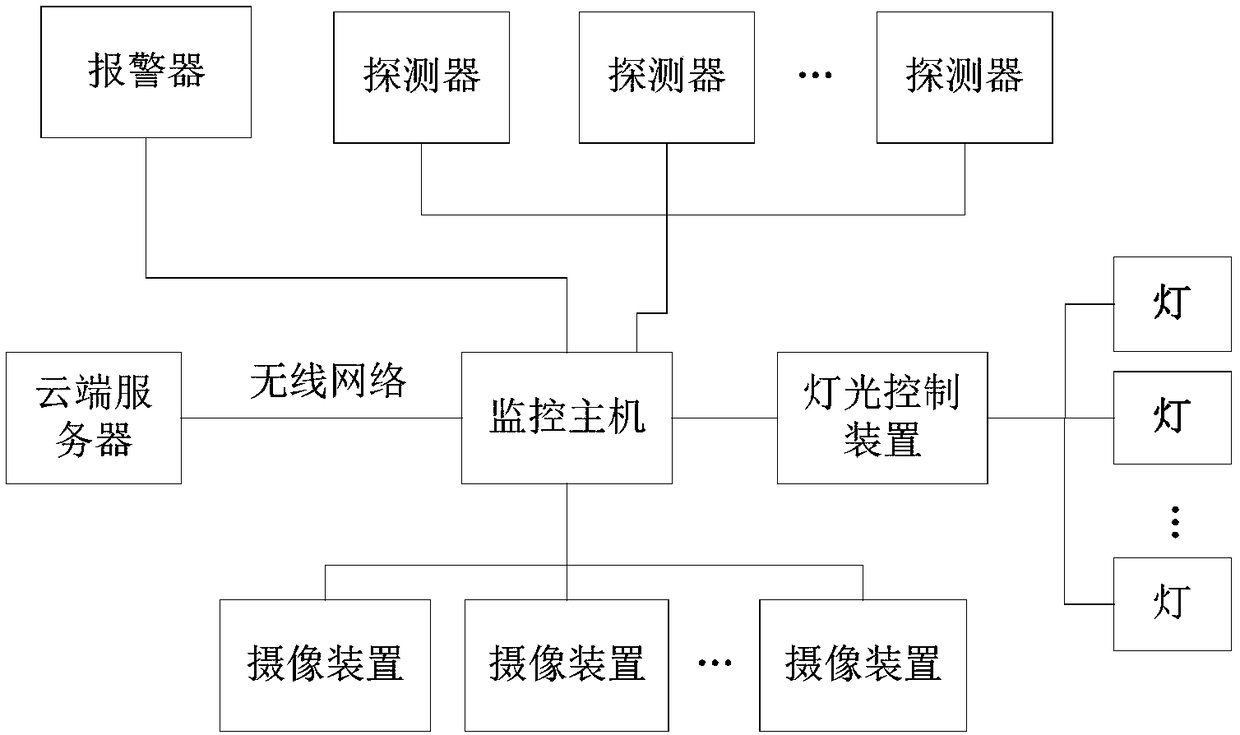
[0030] A linkage response method for a security monitoring system, the security monitoring system involved, as attached figure 1 It includes several detectors, light controllers and several lights connected thereto, at least one camera device, a monitoring host, and an alarm, and the monitoring host is respectively connected to the detectors, light controllers, camera devices, and alarms . The detector is used to monitor abnormal conditions in real time; the user of the camera device collects video signals and / or image signals, and the alarm device is used to generate alarm information; the light controller is used to control the working status of several lights.
[0031] It also includes a cloud server, the cloud server is connected to the monitoring host through a wireless network, and the monitoring host uploads the monitoring video to the cloud server.
[0032] Preferably, the detector in the method of the present invention is an infrared detector, and the infrared detect...
Embodiment 2
[0048] A linkage response method for a security monitoring system. The security monitoring system includes several detectors, a lighting controller and several lights connected thereto, at least one camera device, a monitoring host, and an alarm. Detectors, light controllers, camera devices, and alarms are connected; the linkage response method of the security monitoring system includes the following steps:
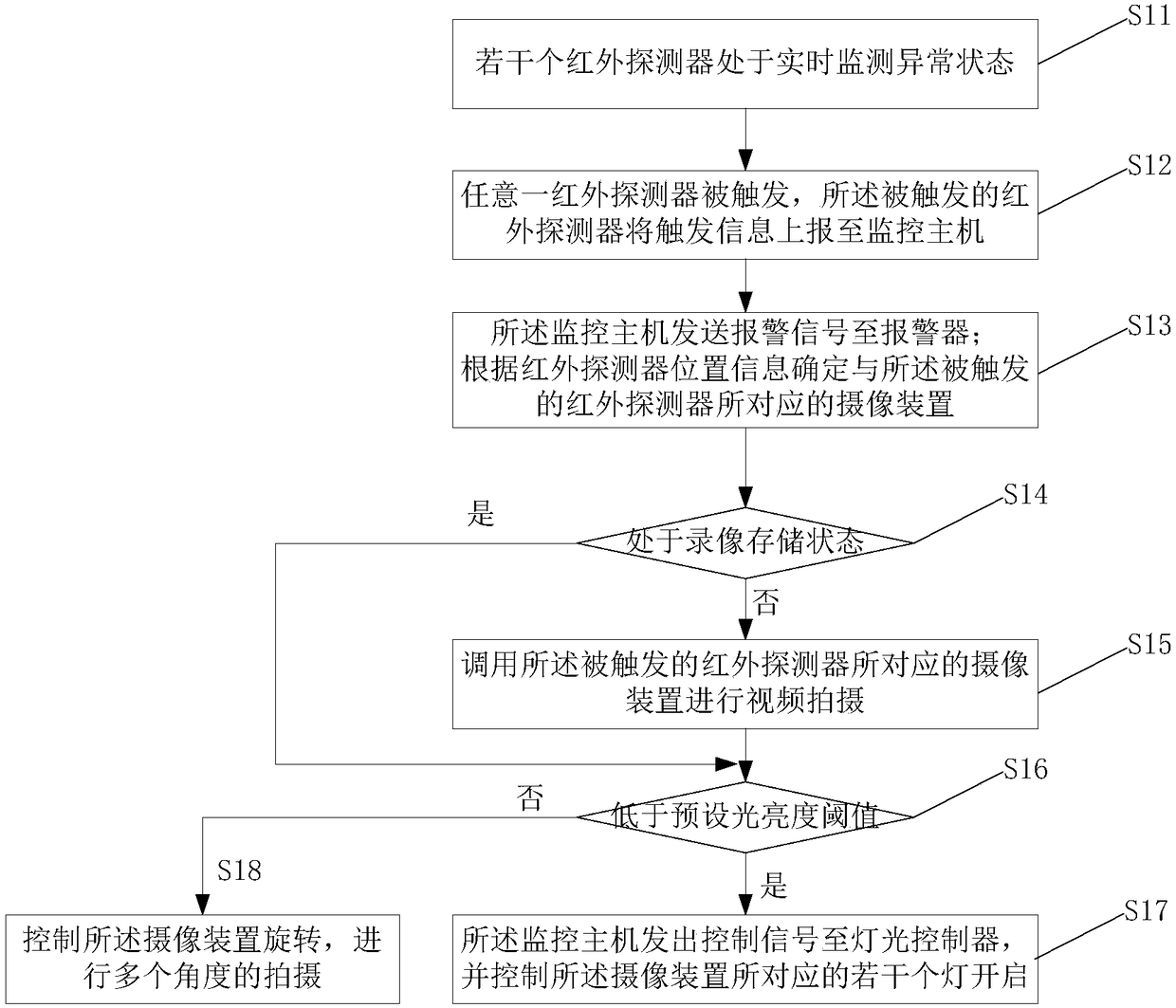
[0049] Step S21, several detectors are in real-time monitoring abnormal state;
[0050] Step S22, any detector is triggered, and the triggered detector reports the trigger information to the monitoring host;
[0051] Step S23, the monitoring host sends an alarm signal to the alarm after receiving the trigger information of the detector, and determines the position information of the detector according to the port information of the triggered detector, and determines the location information of the detector according to the position information of the detector. The camera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com