Encryption device, encrypted text conversion device, encryption program, encrypted text conversion program, encryption method, and encrypted text conversion method
一种加密装置、密文转换的技术,应用在安全通信装置、同态加密通信、编码/译码装置等方向,能够解决无法检测到等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
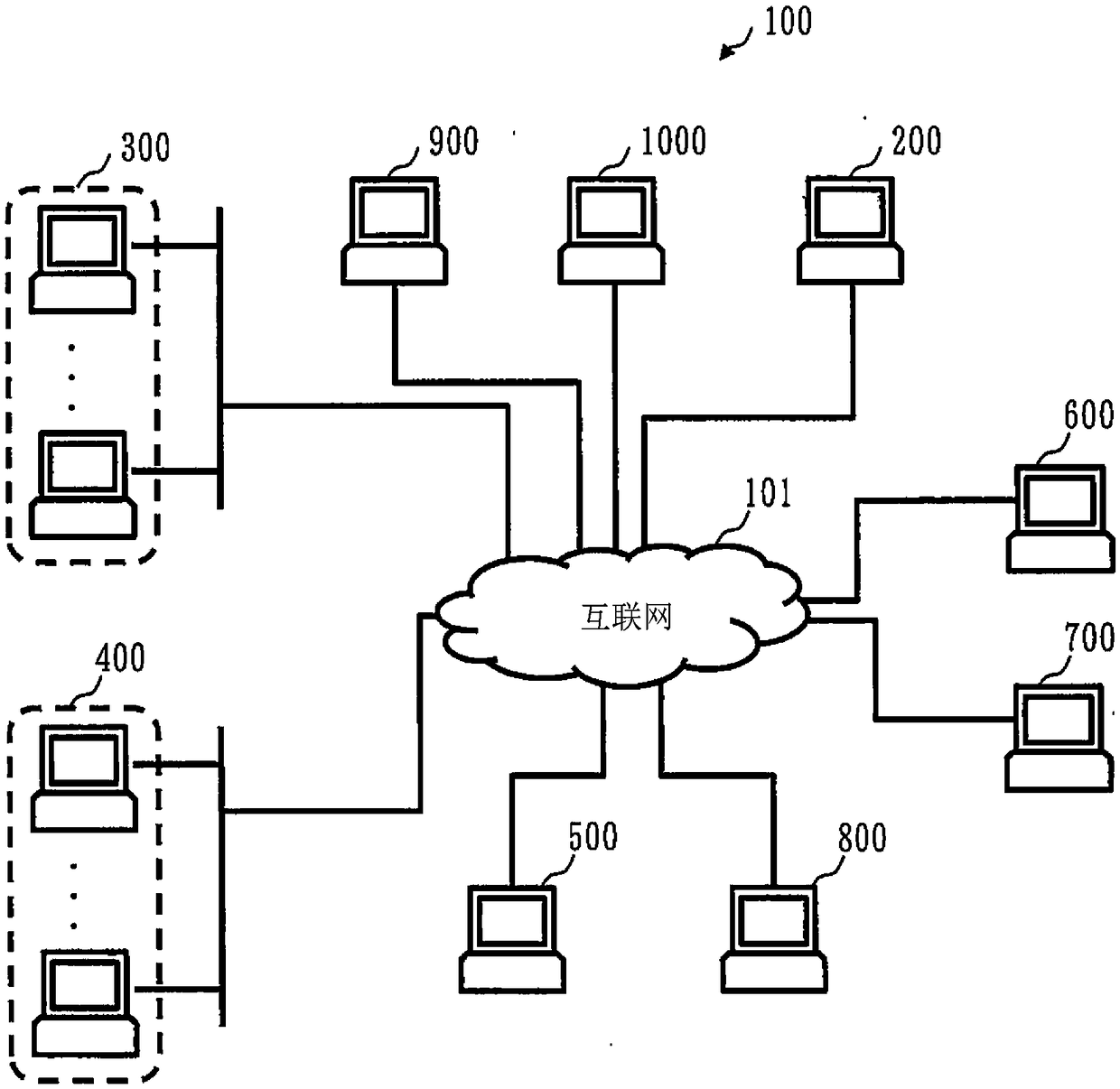
[0044] Next, the key generation device 300 and the like will be described as follows.
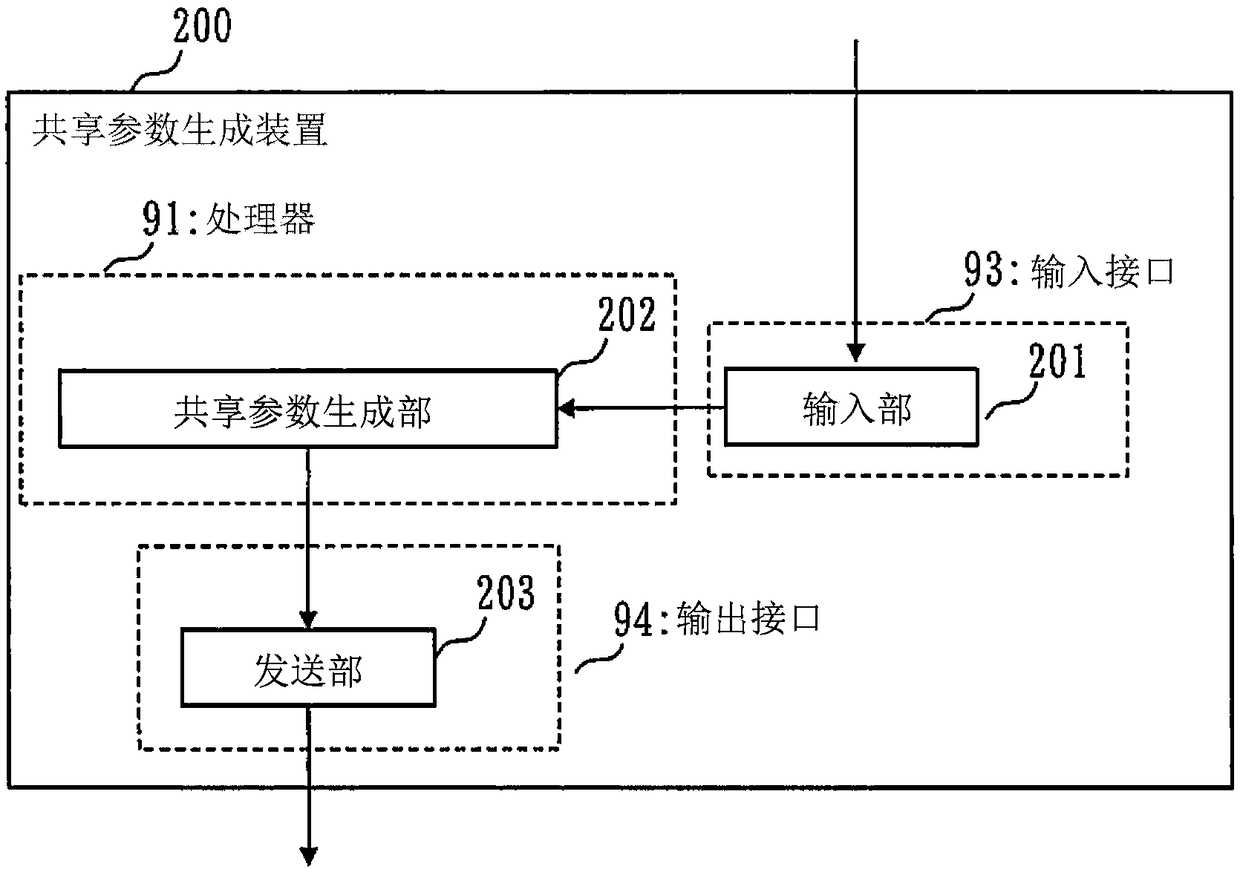
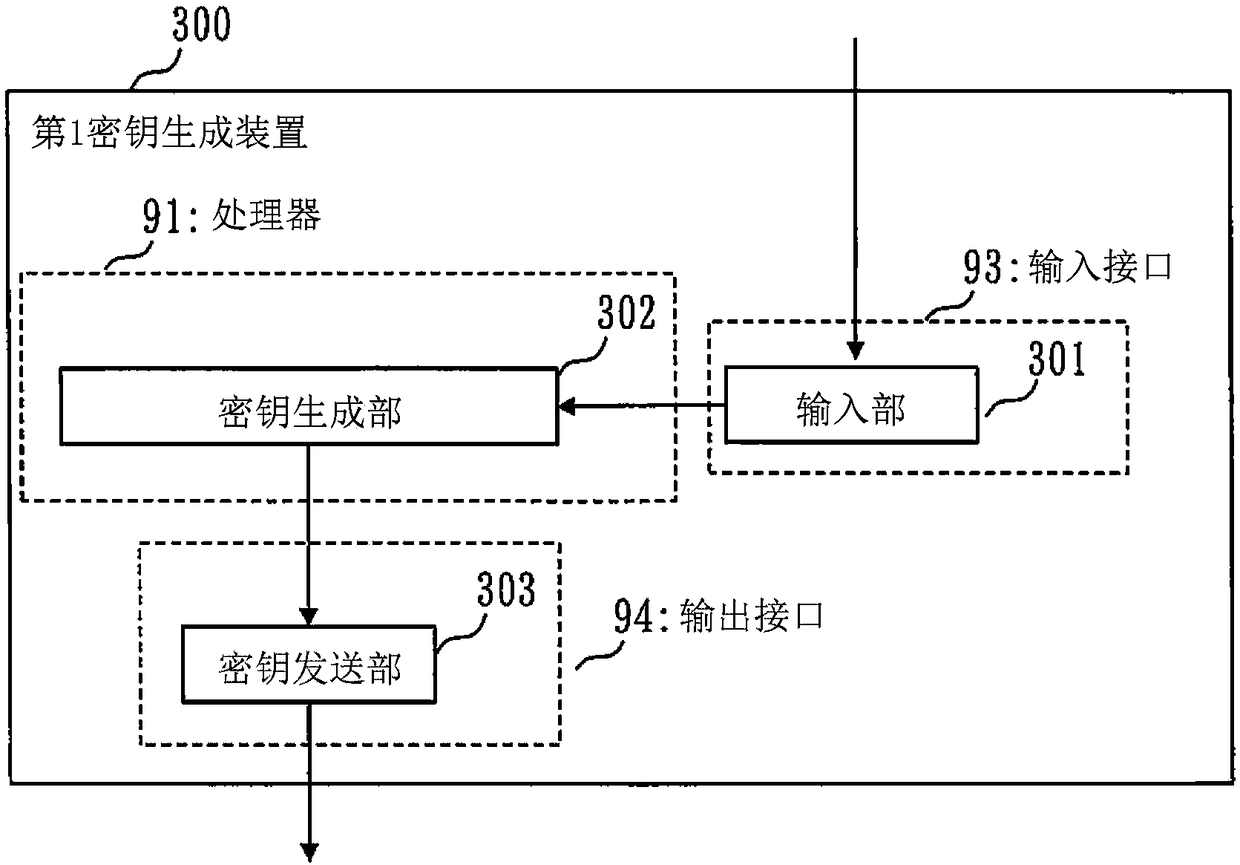
[0045] (1) In Embodiment 1, there is a key generation device 300 that generates a pair of a public key pk and a decryption key sk (secret key). This key generation device 300 is referred to as the first key generation device 300 .
[0046] (2) The public key pk and the decryption key sk generated by the first key generation device 300 are referred to as the first public key pk and the first decryption key sk. In addition, it may also be described as a public key pk and a decryption key sk.
[0047] (3) In Embodiment 1, there is a post-homomorphic key generation device 400 that generates a pair of public key epk and decryption key esk (secret key). This homomorphic key generation device 400 is referred to as a second key generation device.
[0048] (4) The public key epk and the decryption key esk generated by the second key generation device are described as the second public key epk and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com