A method and device for accessing a network instance
A technology for accessing networks and networks, which is applied in the field of communication and can solve unsolved problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
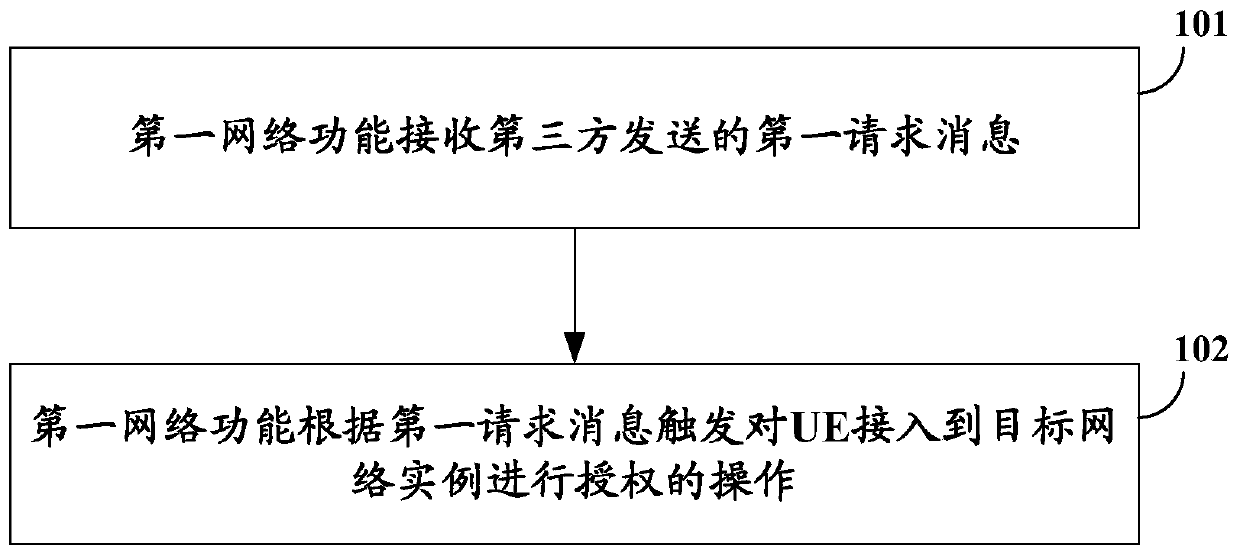
[0063] See figure 1 , The figure shows a method of accessing the network instance, the specific steps are as follows:
[0064] Step 101: The first network function receives a first request message sent by a third party;
[0065] The foregoing first network function may also be referred to as a first NF (Network Functions), or may also be referred to as a first network device, and its specific type is not specifically limited in this embodiment.
[0066] For example: the first network function may be a policy control function. The policy control function may formulate a policy based on the user’s subscription information or information provided by a third party, and then issue it to the policy enforcement entity. The policy enforcement entity will control the UE according to the policy. Flow rate is monitored and / or controlled.
[0067] For another example: the first network function may be a general control network function, which may be a network function commonly used by multiple di...
Embodiment 2
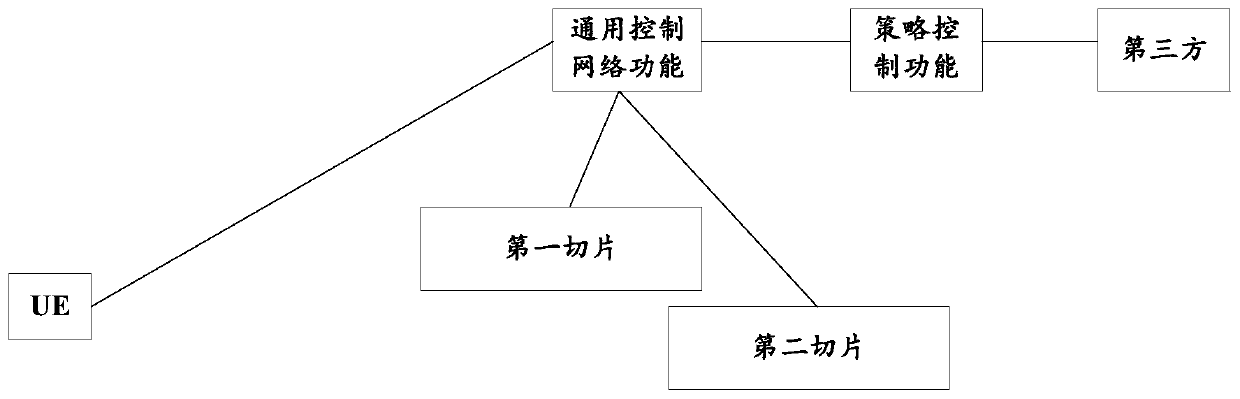
[0094] In this embodiment, the specific network architecture is as figure 2 Shown.
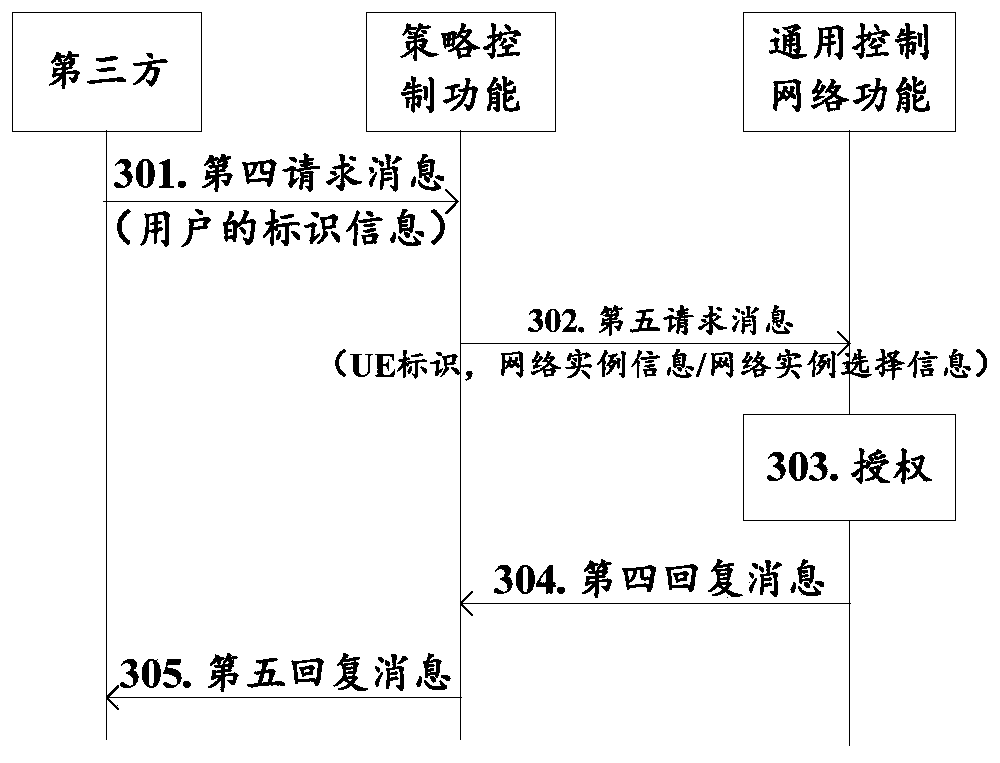
[0095] The UE has already connected to the third party through the first network instance (or referred to as the first network slice), and the UE wants to obtain better services, so it subscribes to the third party. In order to provide better services to the UE, the third party decides to trigger the network to redirect the UE to a specific network instance (for example, a second network instance, or called a second network slice). Based on the above network architecture, the interaction process between the third party and the network is as follows image 3 As shown, the following takes the first network function as the policy control function as an example.
[0096] Specific steps are as follows:
[0097] Step 301: The third party sends a fourth request message to the policy control function. The fourth request message carries at least user identification information (such as user name, UE IP addr...
Embodiment 3
[0108] This embodiment describes the operation after the authorization is successful based on the second embodiment. In this embodiment, the third party triggers the UE to establish a connection in a specific network instance. The specific process is as Figure 4 As shown, the specific steps are as follows:
[0109] Step 401: The third party notifies the UE to connect to the target network instance;
[0110] Step 402: The UE sends a connection establishment request to the general control network function, and the connection establishment request message carries information of the target network instance, such as the network instance identifier or service information;
[0111] The aforementioned general control network function is equivalent to the second network function in the first embodiment.
[0112] Step 403: The general control network function selects the target network instance according to the information of the target network instance, and sends the connection establishment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com