A method and device for NAS message processing and cell list update
A message processing and cell list technology, applied in wireless communication, electrical components, etc., can solve problems that affect the normal use of UE, network equipment cannot provide services, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
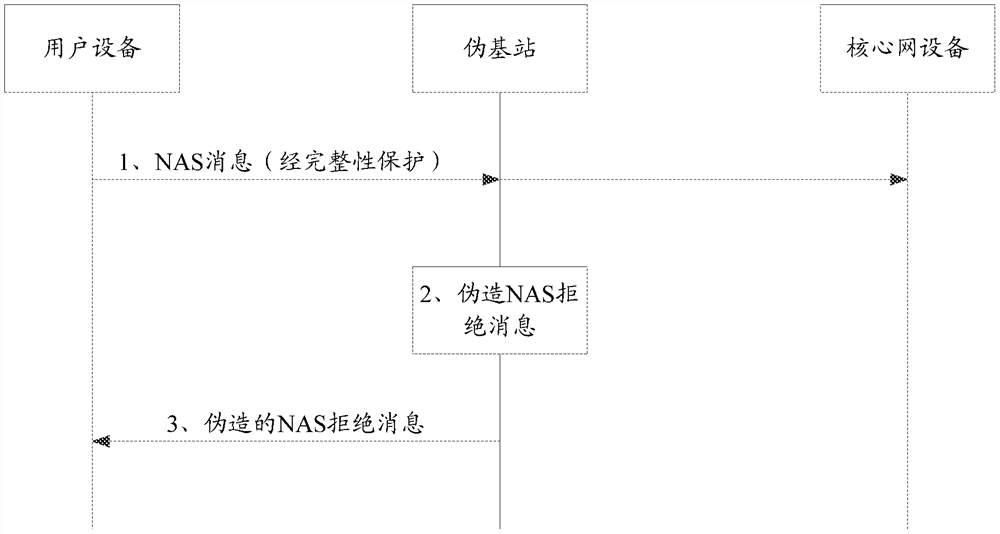
[0146] See Image 6 .
[0147] 1. The user equipment in the idle state initiates a radio resource control (Radio Resource Control, RRC) connection establishment process to the access network device of the serving cell (such as the base station of the serving cell) in the current serving cell. In this process, The user equipment sends an initial NAS request (Initial NAS request) message to the access network device, and the access network device forwards the initial NAS request message to the mobility management network element. The initial NAS request message may include, for example, an Attach Request (Attach Request) Message, location update request message, or service request (Service Request) message and other different messages.
[0148] Optionally, for a 2G or 3G circuit switching domain (Circuit Switching Domain, CS), the location update request message may include a location domain update request (Location Area Update Request) message, for a 2G or 3G packet switching ...
example 2
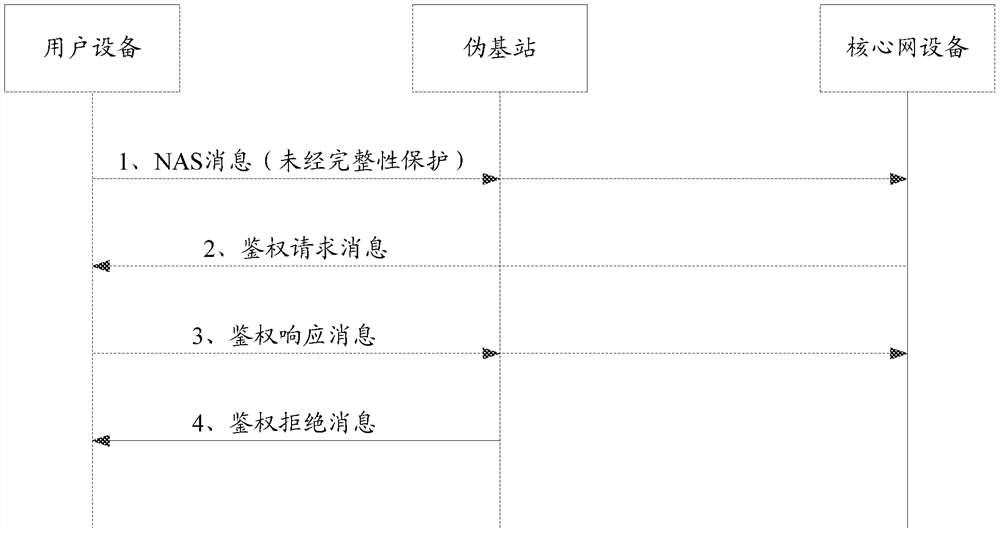
[0174] See Figure 7 .
[0175] Wherein, the content of steps 1, 3, 4, and 6-9 in Example 2 can refer to the description of the corresponding steps in Example 1. To avoid repetition, only the steps different from those in Example 1 are introduced below.
[0176] 2. After sending the initial NAS request message, the user equipment resets the current pseudo-network probability value, for example, it can be reset to 0.
[0177] Optionally, this step may also occur before step 1, that is, before the current serving cell performs step 1 for the first time, the user equipment resets the pseudo-network probability value to 0.
[0178] Typically, the pseudo-network probability value can be applied to a serving cell, and if the user equipment initiates a new initial NAS request message in a new serving cell, the user equipment can also reset the pseudo-network probability value first.
[0179] 5. After receiving the non-integrity-protected NAS rejection message, the user equipment up...
example 3
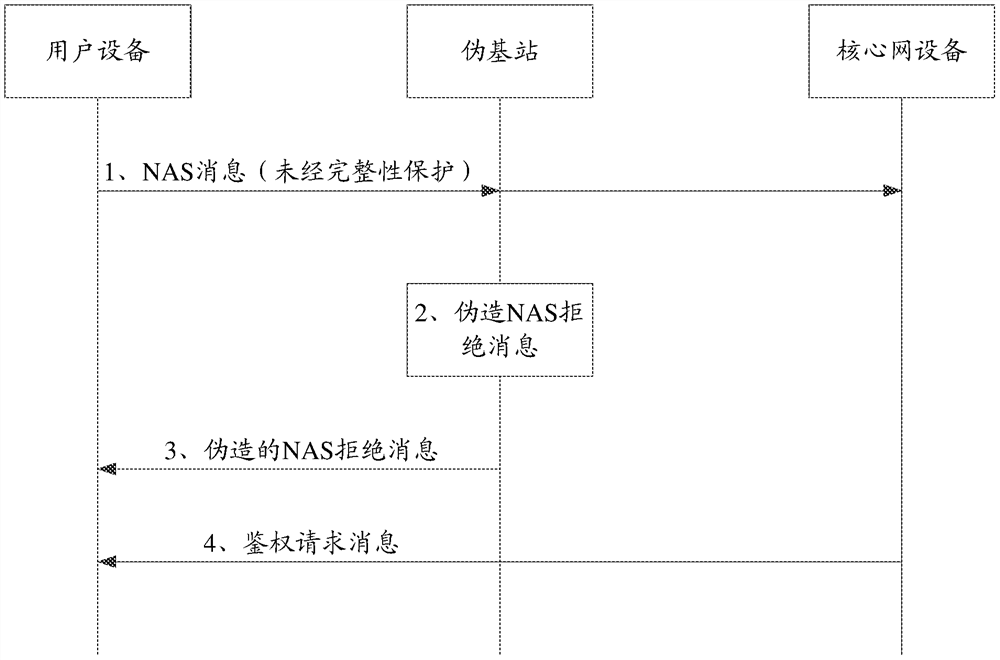
[0185] See Figure 8 .
[0186] Wherein, the content of steps 1-9 in Example 3 can refer to the description of the corresponding steps in Example 1. To avoid repetition, only the steps different from those in Example 1 are introduced below. in addition, Figure 8 Only the steps mentioned below are shown, as for steps 1-9, refer to Image 6 Description of the corresponding steps.
[0187] 10. If the value of the pseudo-network counter reaches the pre-configured value N, the user equipment may consider the current serving network device as a pseudo-network device, that is, determine that the current serving cell is a cell provided by the pseudo-network device. The user equipment saves the identity of the current serving cell, and may try to reselect another suitable cell for access in the current location area or a new location area. The user equipment does not perform the action indicated by the rejection reason value carried in the NAS rejection message.
[0188] 11. The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com