Smart terminal authentication management method
A smart terminal and authentication management technology, which is applied in the field of authentication and anti-counterfeiting based on blockchain technology, can solve problems such as non-standard use, inability to realize dynamic information authentication management, ownership of intelligent processes, and difficulty in appraising and trading the right to use, etc. To achieve the effect of enhancing reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Embodiment 1: intelligent fire protection
[0035] At present, fire protection facilities mainly use anti-counterfeiting labels or various certification certificates (such as CCCF certification in China, UL certification in the United States, etc.).
[0036] Add a block chain interface module to the equipment, integrate the interface module with the original circuit system, and use it to collect the required data from the original equipment (such as the water pressure and water flow speed of the fire water system) to realize the Internet of Things interface. At the same time, an asymmetric key pair EK (EKpub, EKpri) is generated, in which the key EKpri is only stored locally for system authentication, and the public key EKpub can be directly accessed.
[0037] 1) Certification: There are two ways, one is manufacturer certification; the other is blockchain certification.
[0038] i) Manufacturer certification
[0039] It is realized by the two signature methods of manu...
Embodiment 2
[0049] Embodiment 2: smart camera
[0050]The block chain interface module (which can be in the form of software) is placed in the original circuit, and the data generated by the smart camera (such as face recognition results, behavior recognition results, etc.) can be obtained. At the same time, an asymmetric key pair EK (EKpub, EKpri) is generated, in which the key EKpri is only stored locally for system authentication, and the public key EKpub can be directly accessed.
[0051] 1) Certification: There are two ways, one is manufacturer certification; the other is blockchain certification.
[0052] i) Manufacturer certification
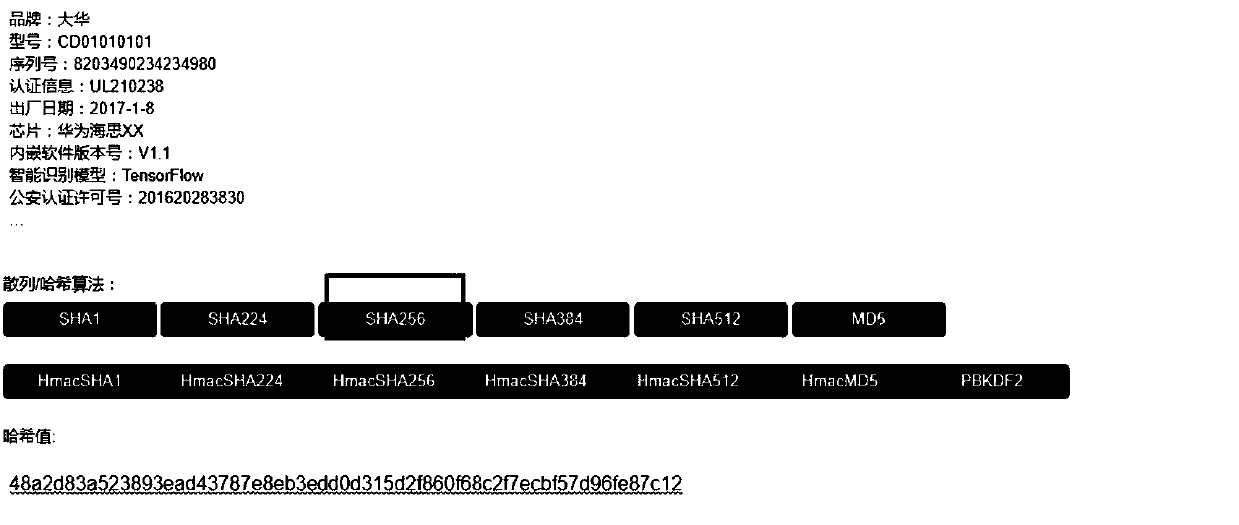
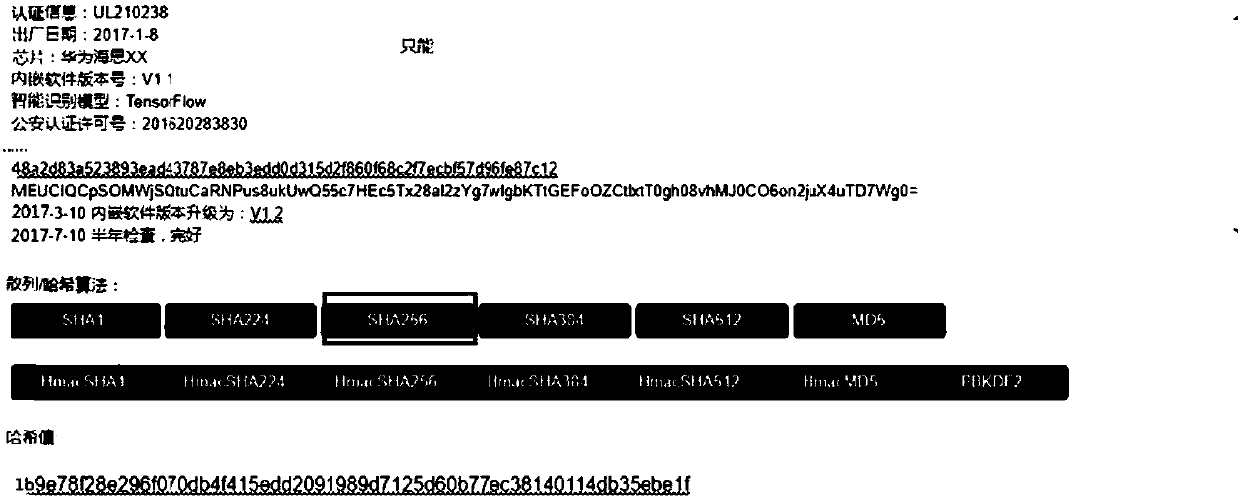
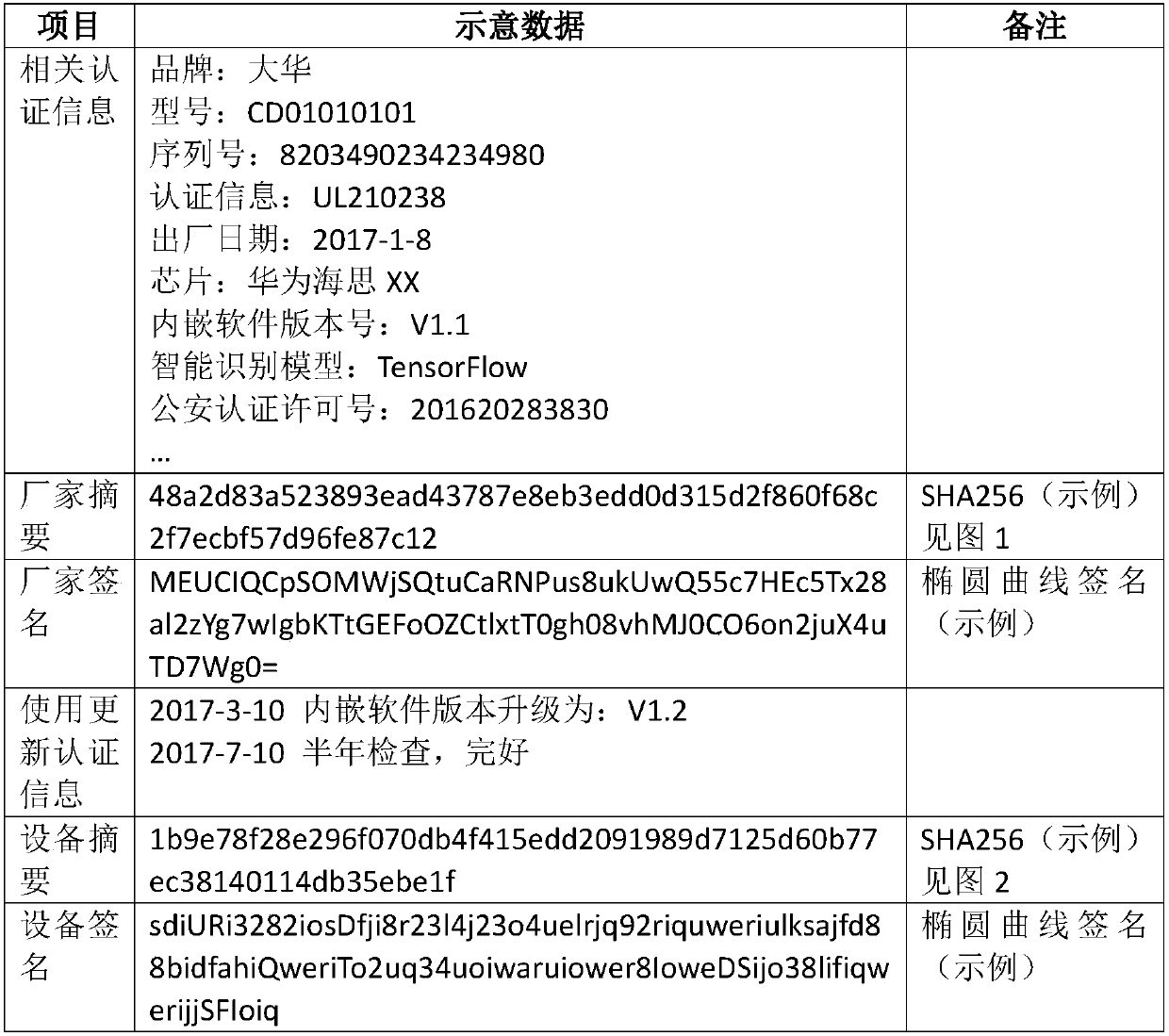
[0053] It is realized by the two signature methods of manufacturer's signature + device signature: the manufacturer's own MK (MKpub, MKpri) will pass relevant certification information (including product model, serial number, certification information, date of manufacture, etc., and can also include photos, etc.) ) using MD5 256 to generate a summa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com