Authentication method and system for item seal and storage in electronic shopping bag
A technology of electronic shopping and authentication method, applied in the field of information, can solve the problems such as the ineffectiveness of item storage and delivery process monitoring, and achieve the effect of improving the shopping experience and reducing the trouble of carrying items
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
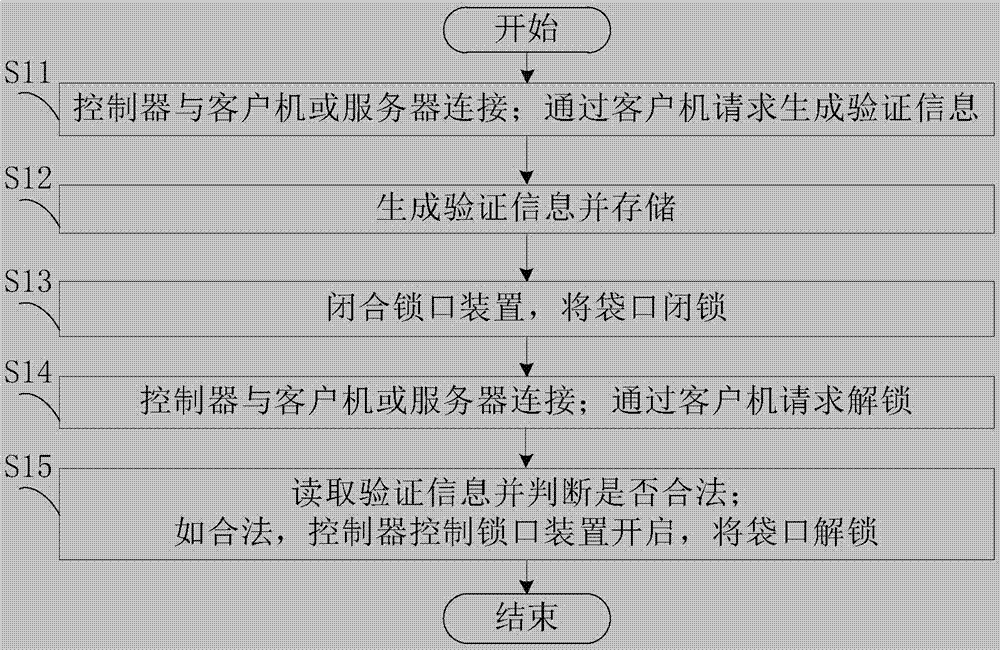
[0091] The method for authenticating sealed articles in the electronic shopping bag includes two steps of generating sealed records and authenticating.
[0092] The step of generating a sealed record in the method for authenticating sealed items in an electronic shopping bag includes the following contents:
[0093] Put the items into the electronic shopping bag; connect with the server through the client computer, and input the storage information.
[0094] Wherein, the electronic shopping bag includes a bag body, a controller and a locking device. The bag body is used for storing articles, and the bag body includes a lockable and unlockable pocket. The lock device includes two states: closed and open. When the lock device is closed, the bag mouth is locked, and when the lock device is opened, the bag mouth is unlocked. The controller is connected with the locking device to control the opening of the locking device.
[0095] The client computer can be a computer or a mobil...
Embodiment 2
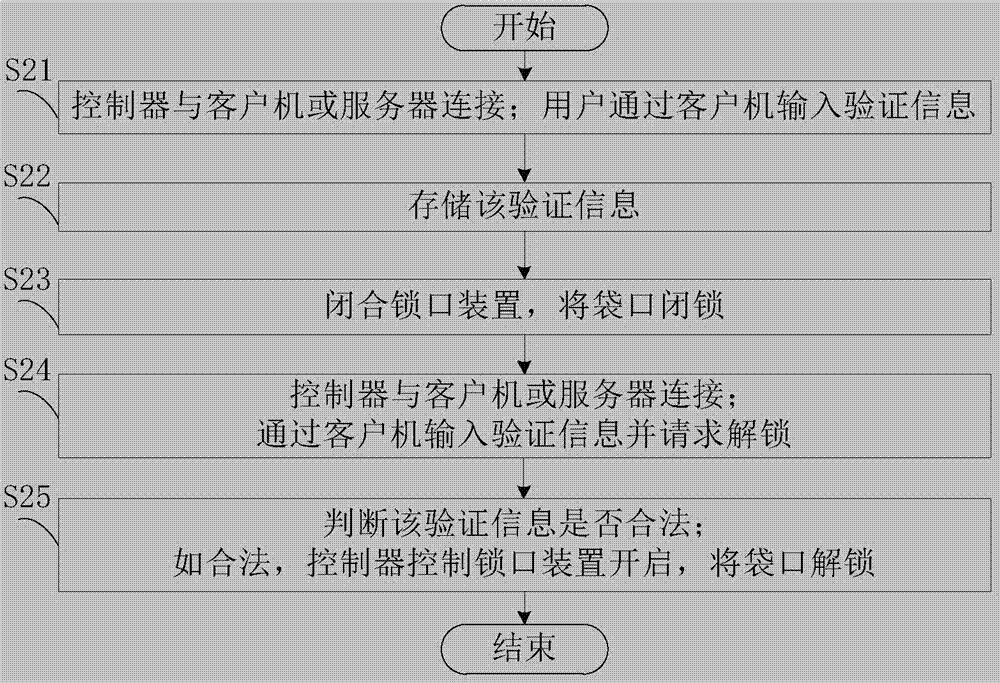
[0130] The difference between this embodiment and Embodiment 1 is that the flow process of the authentication step in the electronic shopping bag sealed item authentication method is different, such as figure 2 shown, including the following steps:
[0131] In S21, the controller is connected with the client or the server; the user inputs verification information through the client.
[0132] In this step, the connection between the controller and the client or server is similar to step S11.
[0133] After the controller communicates with the client computer or the server, the user inputs authentication information through the client computer. In this embodiment, the user can only input verification information through the client computer, and the verification information is the basis for unlocking the lock device in the future, which is equivalent to the key for unlocking. The verification information input by the user may be in the form of a password, a graphic code, or th...
Embodiment 3
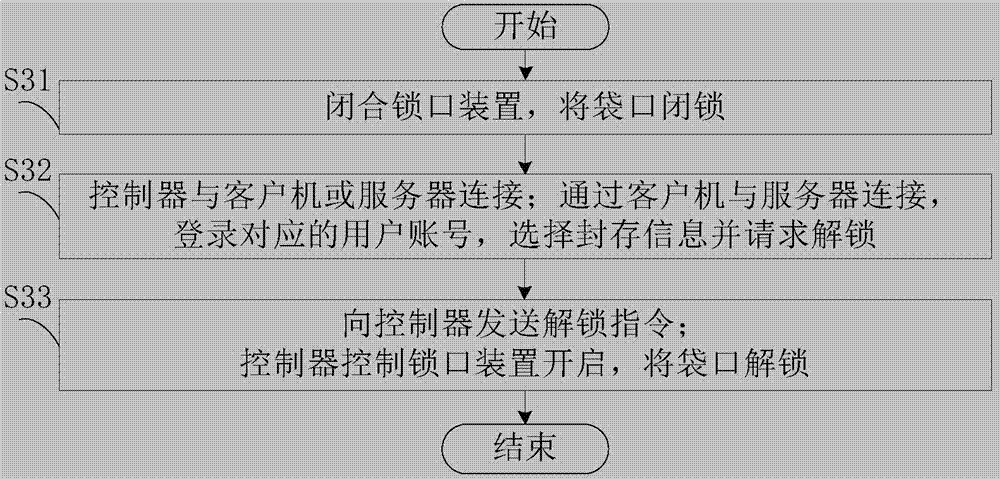
[0147] The difference between this embodiment and Embodiment 1 is that the flow process of the authentication step in the electronic shopping bag sealed item authentication method is different, such as image 3 shown, including the following steps:
[0148] In S31, the locking device is closed to lock the opening of the bag.
[0149] This step is similar to step S13, except that if the lock device is controlled by the controller to close, the controller needs to be connected to the client in advance, and the client sends a lock request to the controller.
[0150] In S32, the controller is connected to the client or the server; the client is connected to the server, the corresponding user account is logged in, and the information is selected to be archived and requested to be unlocked.
[0151] In this step, the connection between the controller and the client or server is similar to step S11.
[0152] After the controller is connected to the client or server, connect to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com