Identity authentication method and system based on body shapes and movements
A body shape, identity authentication technology, applied in the field of wireless networks, can solve the problem of cumbersome authentication process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
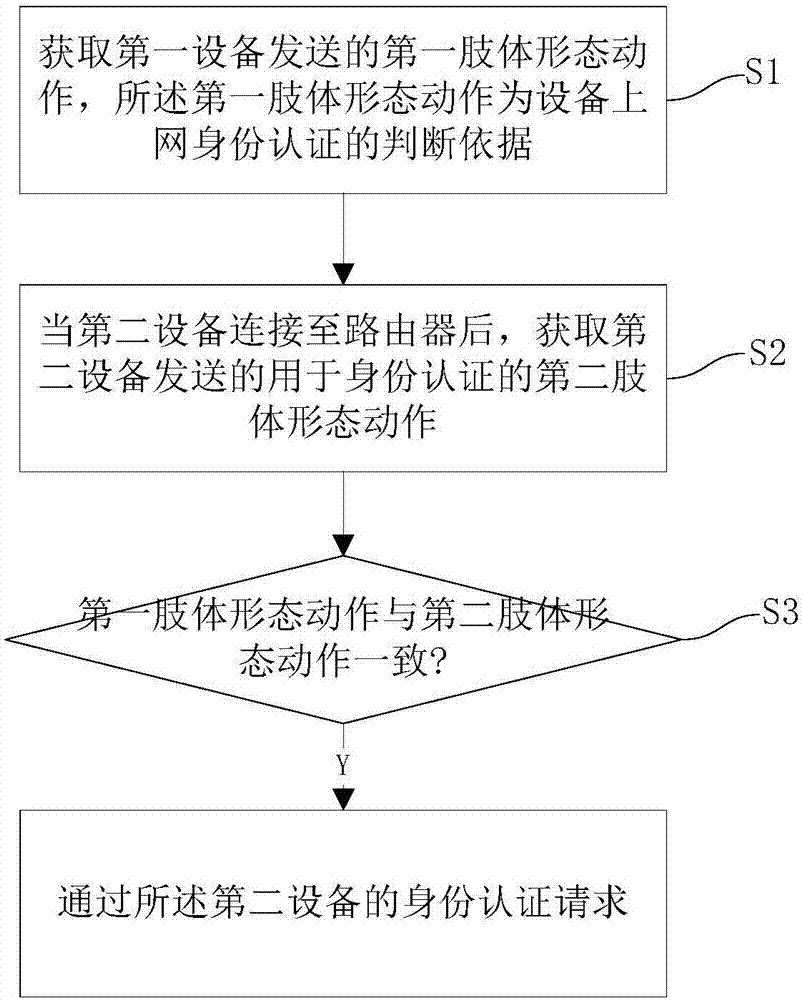
[0062] figure 1 It is a flow chart of an identity authentication method based on body shape actions in this embodiment, such as figure 1 As shown, a kind of identity authentication method based on body shape action in the present embodiment comprises steps:
[0063] S1. Obtain the first body shape action sent by the first device, and the first body shape action is the basis for judging the device's online identity authentication;
[0064] This step is mainly the body shape action preset to be used as the router authentication password, that is, the first body shape action.
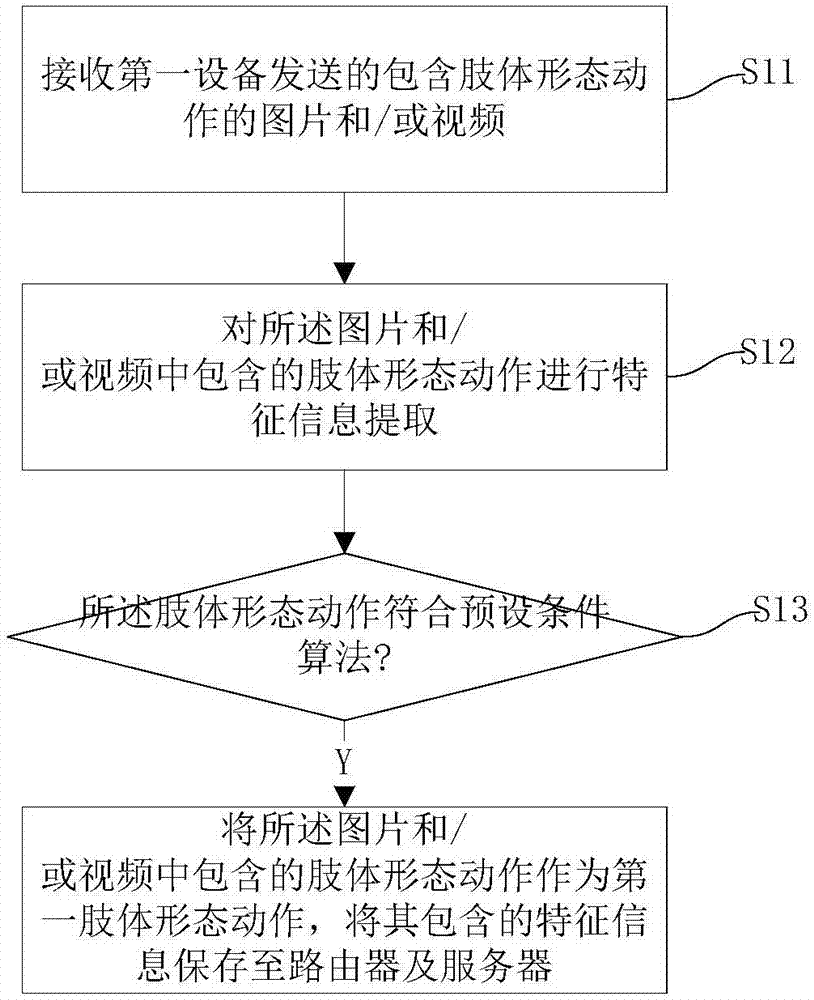
[0065] figure 2 Obtain the specific flow chart of the first body shape action for the router, such as figure 2 As shown, the router obtains the first body shape action sent by the first device as follows:
[0066] S11. Receive pictures and / or videos containing body movements sent by the first device;
[0067] In this step, the first device is a terminal device that has established a network connecti...
Embodiment 2
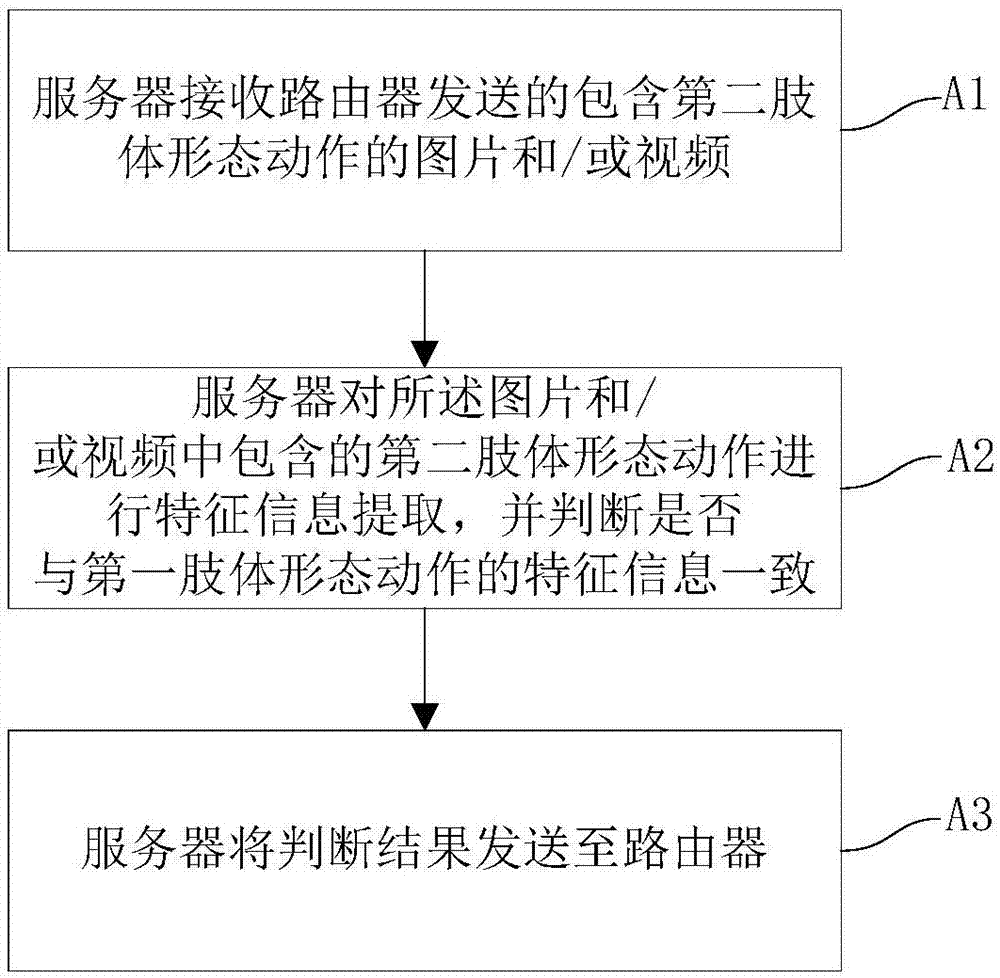
[0108] Figure 5 It is a structural diagram of an identity authentication system based on body shape and action in this embodiment, such as Figure 5 As shown, a kind of identity authentication system based on body shape action in the present embodiment comprises:
[0109] Device 10, configured to send pictures and / or videos containing body movements to the router;
[0110] The router 20 is configured to acquire the first body shape action and the second body shape action according to the picture and / or video containing the body shape action sent by the device. The first body shape action is the basis for judging the identity authentication of the device online, so The second body shape action is used for identity authentication; when the router is not connected to the Internet, it is used to judge whether the first body shape action is consistent with the second body shape action, and pass or reject the identity of the device according to the judgment result authentication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com