A kind of otp memory and its data writing and reading method, security chip
A data writing and memory technology, applied in the field of memory and information security, can solve the problem that the key data is easily obtained illegally, and achieve the effect of increasing the difficulty of identification, increasing the difficulty, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
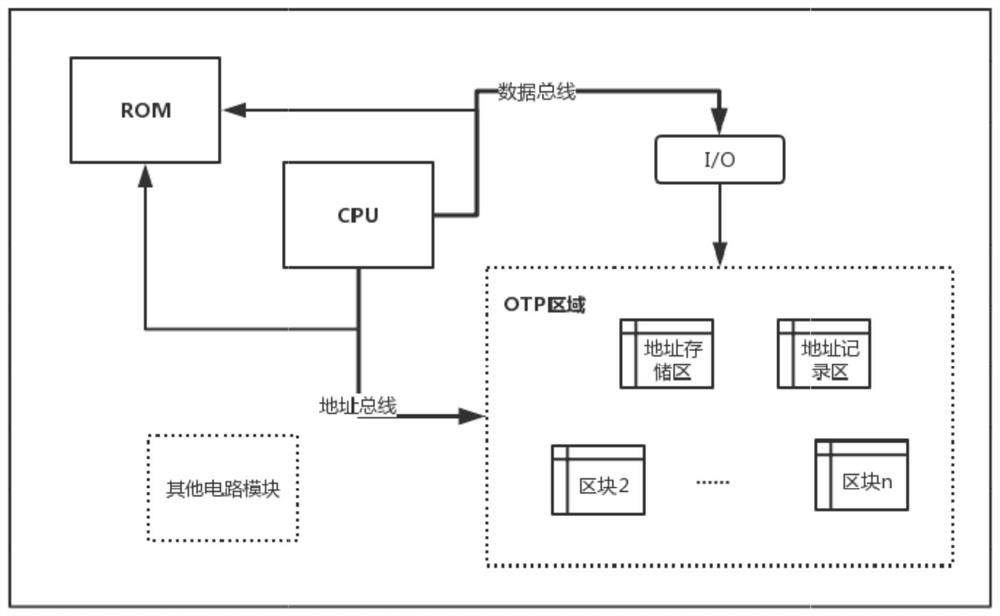
[0040] Generally, a security chip at least includes an on-chip CPU, ROM, a key storage area (usually an OTP array), and related processing circuit modules. The ROM usually stores the processing code and data for the on-chip CPU to operate the logic of the chip, such as logical processing such as analyzing and extracting the key. The key storage area, that is, the OTP memory generally stores key data. The process of improving the security protection of the key data in the security chip proposed by the present invention includes the segmentation and isolation of the OTP storage area, and the randomization of reading and writing of the storage area.
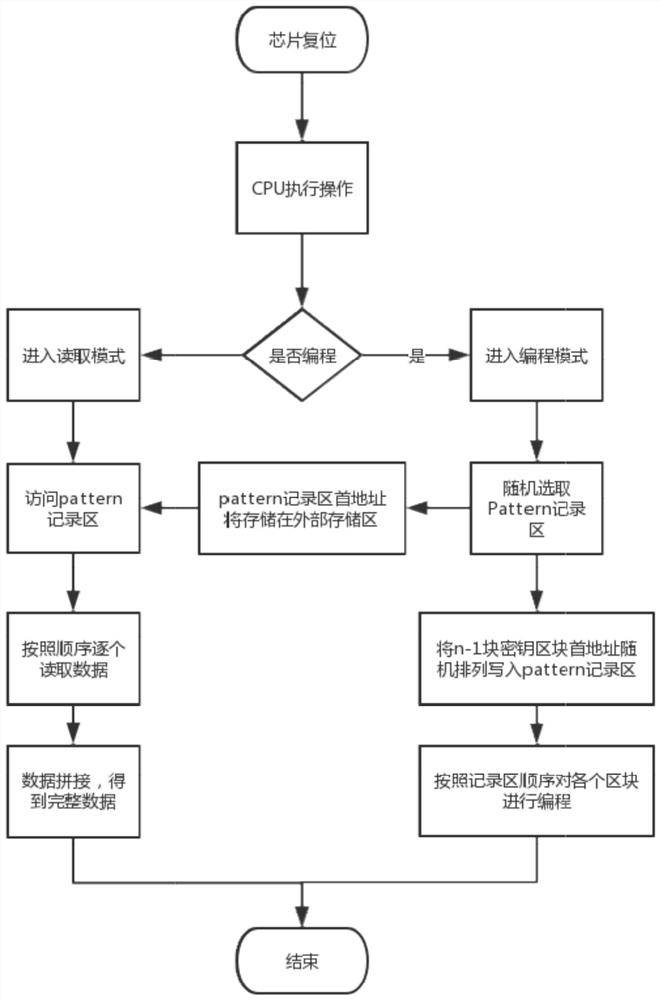
[0041] The writing of key data is realized through chip programming. When programming, the anti-fuse structure is broken down by a high-voltage signal, and the state of the OTP bit is changed to write data 0 or 1. Once the data is written into the bit, it will not be able to be programmed, otherwise the bit will be damaged. . Whe...
specific Embodiment approach 2
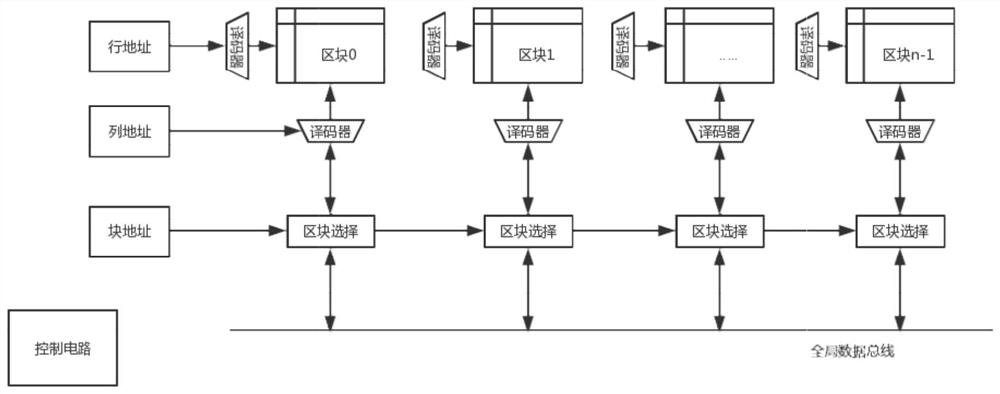
[0053] The difference between this specific embodiment and the first embodiment is that: when writing data in each OTP small block, it is further restricted to write in a segmented and encapsulated manner, thereby further improving the security of data storage.
[0054] In this embodiment, when writing data, a complete piece of input data is decomposed and randomly stored in each address segment in a small block. The traditional data storage method is to directly write all the data into a continuous segment starting with a certain address. Although this method is more convenient in reading and writing data, illegal personnel can easily obtain the key data through methods such as bus detection, and the storage security is not high. In this specific embodiment, any segment of input data is decomposed and stored in a random address segment, and the same data as that at the time of storage is returned when read. For the user, the processing logic is completely closed, and this da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com