Data decryption method based on quantum shared key
A shared key and data encryption technology, which is applied in the field of secure communication, can solve the problems of cumbersome data encryption process, reduce encryption and decryption, etc., and achieve the effect of improving encryption efficiency and simple process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
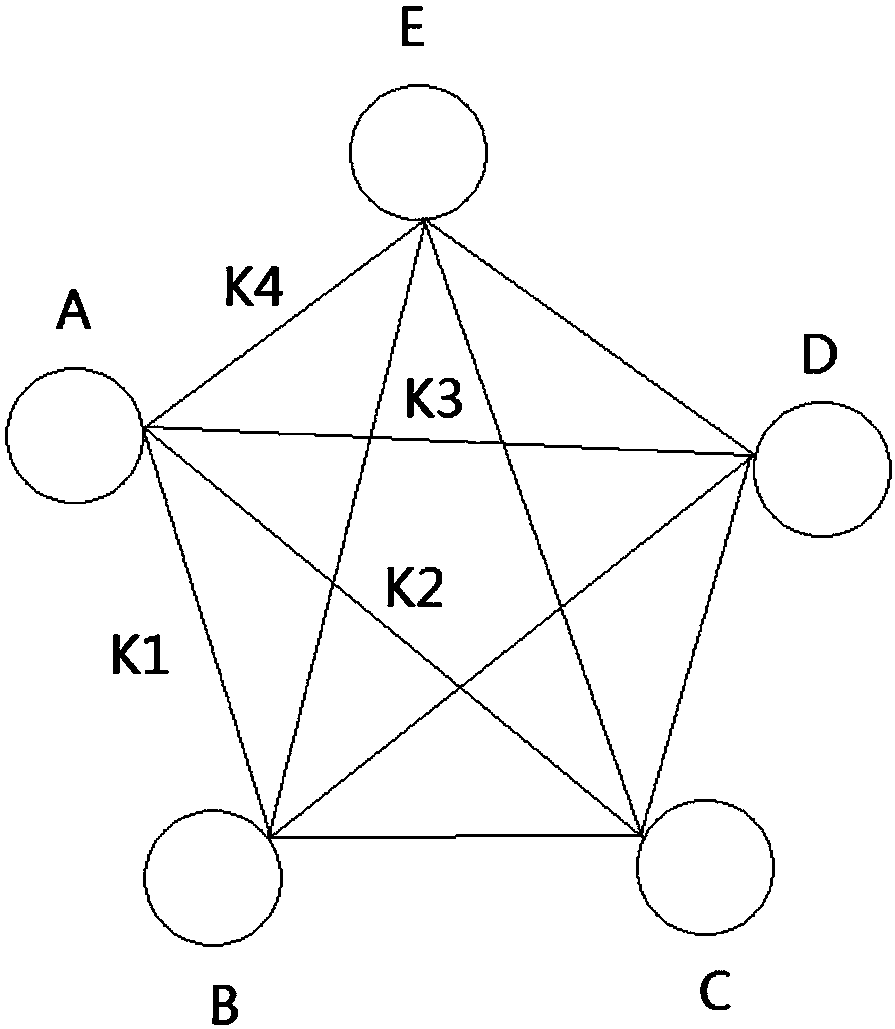
[0037] In the quantum key network, there is a shared quantum key (symmetric key) between any two points, and the network can carry out point-to-point and multi-point information transmission.
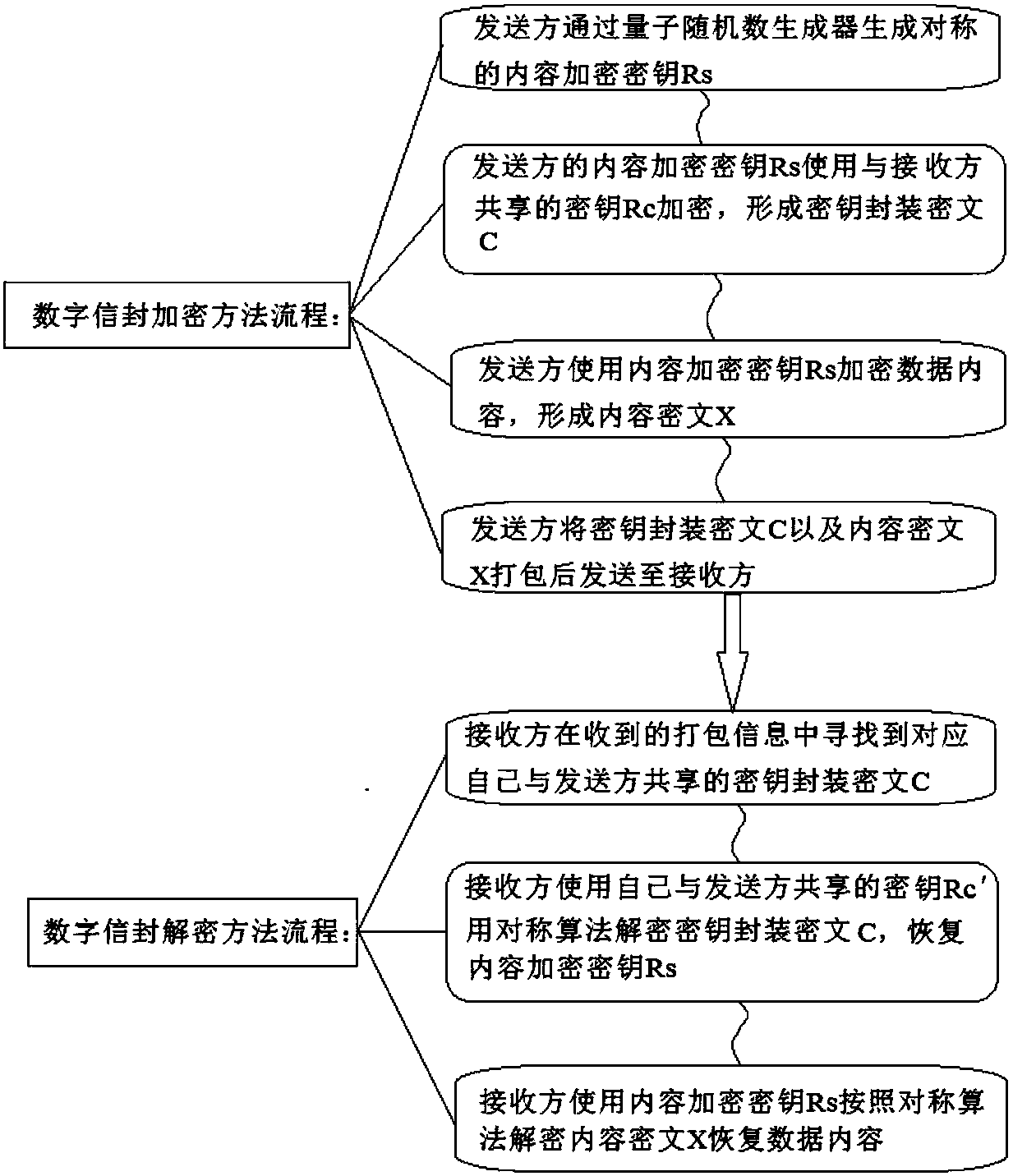
[0038] Such as figure 1 As shown, user A wants to send an email to four users B, C, D, and E. The sender can use the quantum random number generator to generate the encryption key R for encrypting the email content, and use the key R to encrypt the email to form the email ciphertext X. Then the sender uses the quantum keys (symmetric keys) K1, K2, K3, and K4 shared with B, C, D, and E to encrypt the mail encryption key R respectively to form key ciphertexts C1, C2, C3, C4, sender A then organizes C1, C2, C3, C4, X according to a certain format and sends them to each receiver B, C, D, E, receivers B, C, D, E respectively according to their own and sending Party A’s shared quantum keys K1, K2, K3, and K4 decrypt key ciphertexts C1, C2, C3, and C4, decrypt the email encryption key R, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com