Application monitoring method, development platform, client and information system
A technology that applies information and clients. It is applied in the information field and can solve problems such as time lag and timeliness dependence on time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0202] Such as Figure 9 As shown, this embodiment provides an information processing method including:
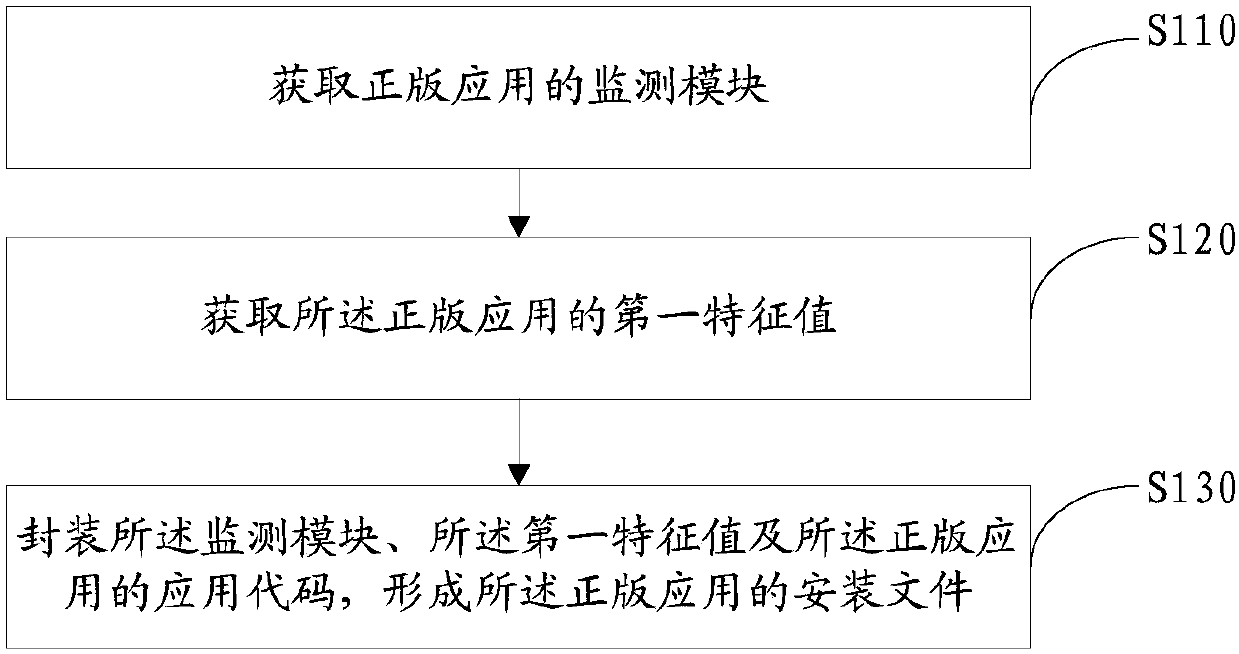
[0203] Step A: Add a monitoring module to the application code and package it to generate an APK file. The APK file here is the installation file.
[0204] Step B: After the APK file is installed, the monitoring module is called to obtain monitoring information during runtime, and it is determined whether the current application is a pirated application.
[0205] Said step A may comprise:
[0206] In the APP development stage, the monitoring module is added to the code project, and an APK file containing the monitoring module is packaged and released as a genuine application on the application channel. Specifically, to package the monitoring module into a library file, add the calling code of the library file in the startup code segment of the APP, obtain the SHA1-Digest values of all files contained in the APK after decompression, and encrypt them, store them in the ...
example 2
[0253] Such as Figure 12 As shown, this example provides a system applicable to the aforementioned information processing method: the system includes two parts: a monitoring software development kit SDK and a server.
[0254] The monitoring SDK is included in the application to be monitored as a library file, including a server-side interaction module 100 , a file difference comparison module 200 , and an APK feature extraction module 300 . As the cloud, the server side can interact with all applications to be monitored, issue instructions to them, and manage all application data, including monitoring SDK interaction module 400, risk score calculation module 500, pirated application monitoring management module 600, and monitoring SDK library files A module 700 is generated.
[0255] The function of the server-side interaction module 100 is mainly to interact with the server side. When the file difference comparison module finds that it is a pirated application, it sends pir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com