User authority identification method and system and computer device
A technology of user authority and identification method, which is applied in the field of computer-readable storage media and user authority identification, can solve problems such as easy tampering, large authority information, and untrustworthiness, and avoid single-point problems caused by centralized session management. The Effects of Performance Issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
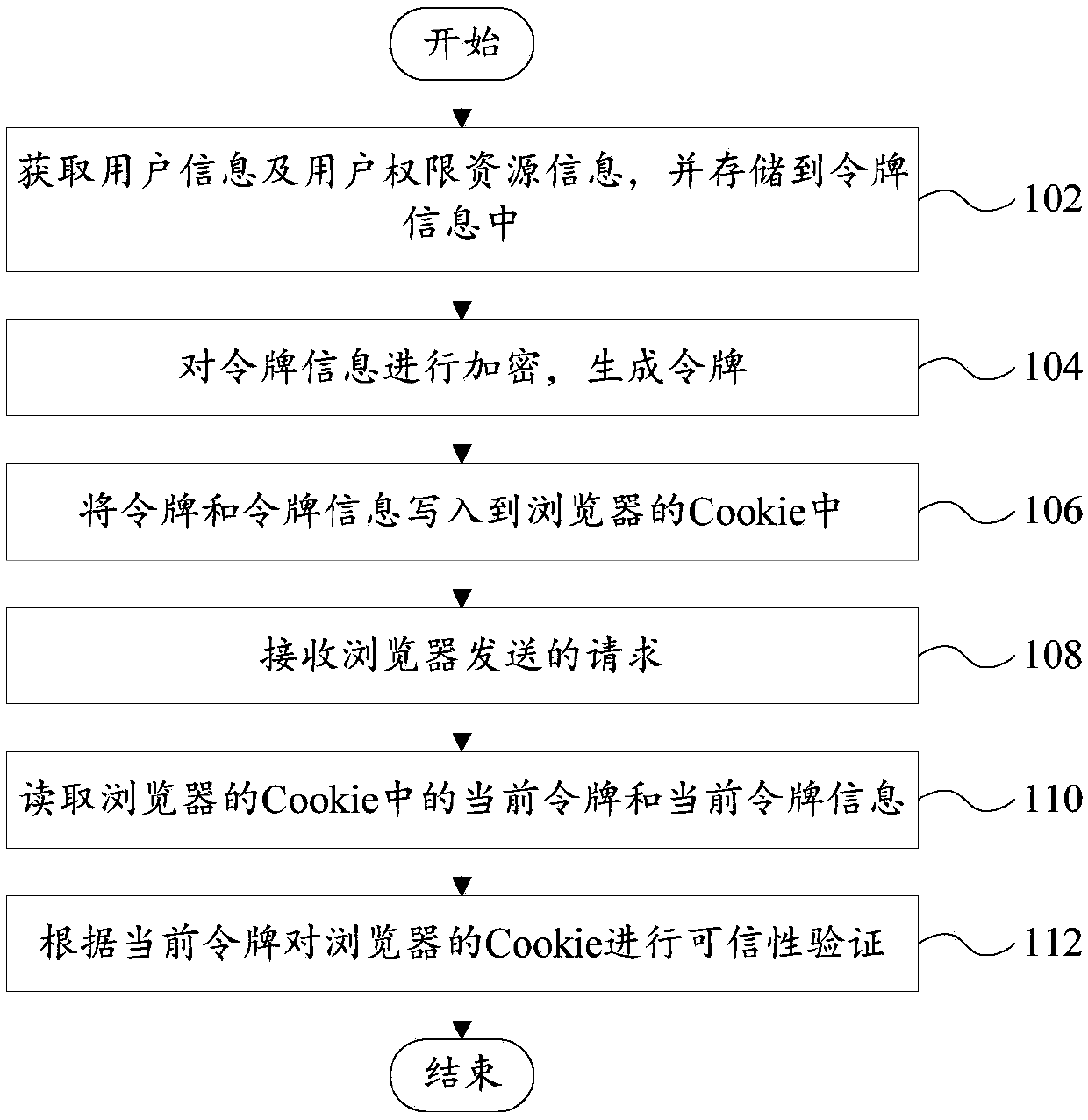
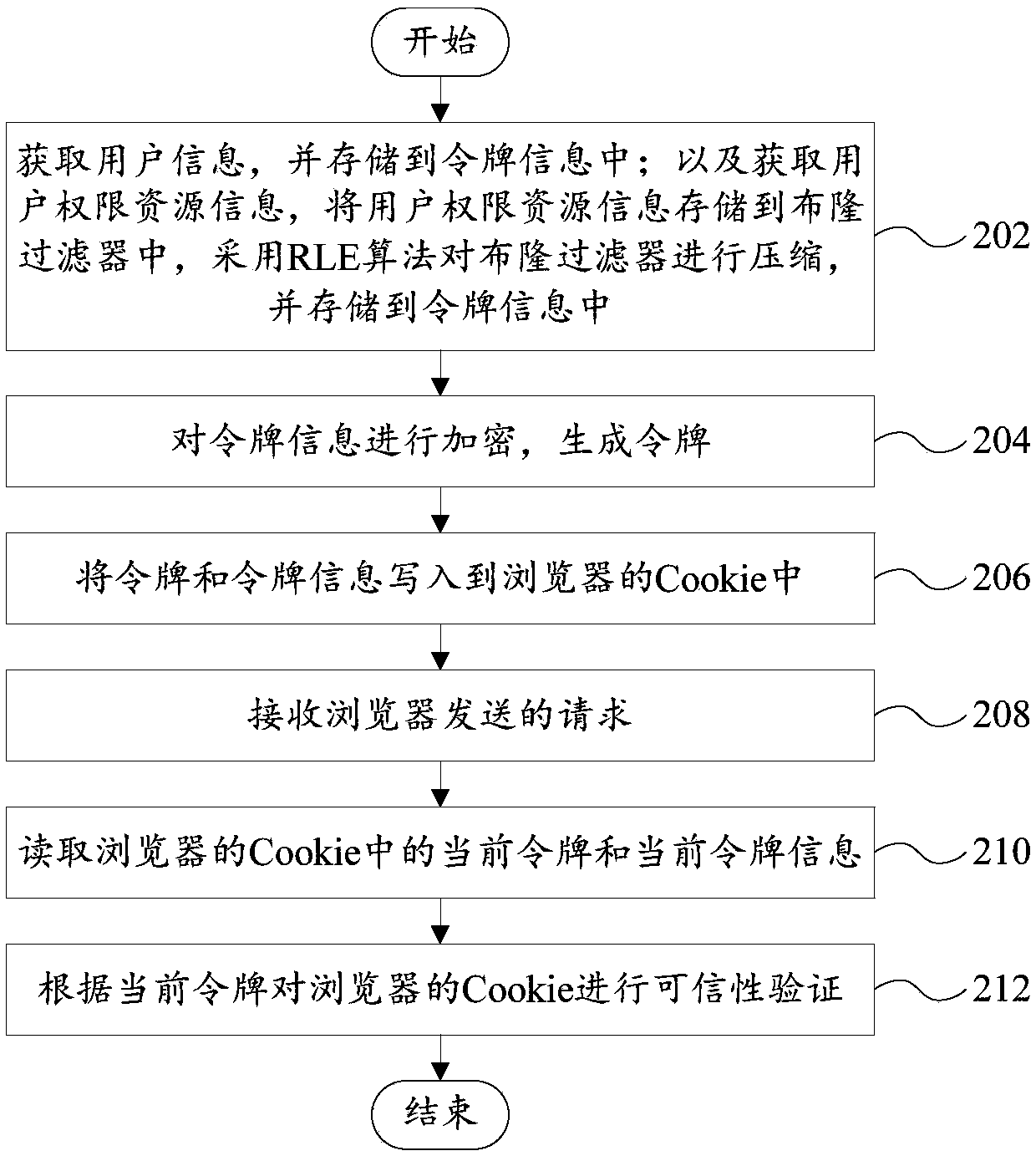
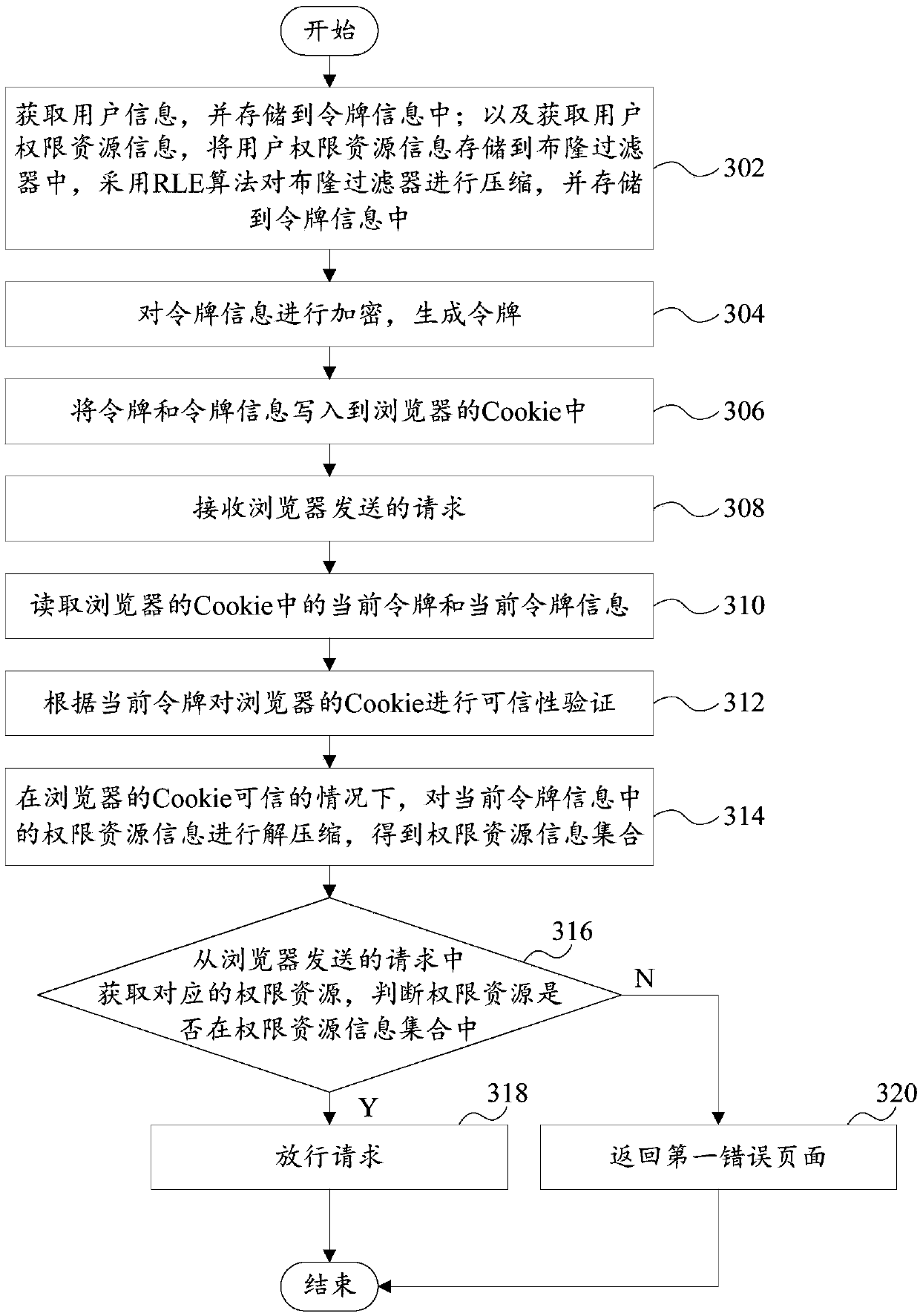
[0128] A stateless and session-free device for authenticating login user authority is proposed. Including: Bloom Filter (Bloom Filter): Bloom Filter is a random data structure with high space efficiency. It uses a bit array to represent a collection concisely, and can determine whether an element belongs to this collection. Bloom Filter stores 1w Only 5k space is required for different permissions;
[0129] The secret key is stored on the application server side, and the information is converted into the input parameters in the ciphertext process through the HMAC algorithm;
[0130] The rights manager implements the creation, distribution and authentication of tokens, and its components include:
[0131] Token (Token) means token (temporary) in computer identity authentication, representing the object of the right to perform certain operations;
[0132]Token information (TokenParameter) is used to identify the information contained in the Token, such as user ID, timestamp wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com