Anti-reinforcement fast detection method of Android platform cloning application program
A technology of application programs and detection methods, which is applied in the field of clone software detection and mobile security, can solve the problems of detection method failure, high time consumption, and inability to be widely used, and achieve the effect of improving detection speed and avoiding impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
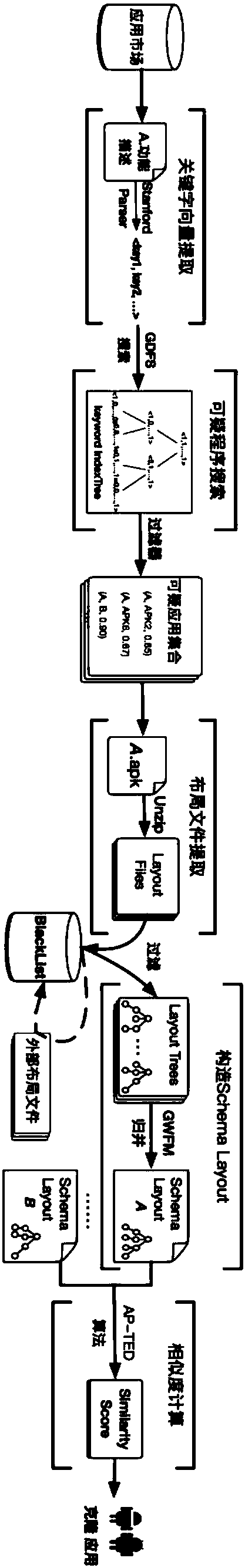
[0041] like figure 1 Shown, the present invention comprises the following steps:
[0042] 1. Initialization: Construct a balanced binary tree index based on key vectors;
[0043] 2. Input the functional description of the target application, and use Stanford Parser to extract the keyword vector of the dynamic dimension;
[0044] 3. Use the greedy-based depth-first search algorithm to quickly search for similar applications in the index tree and add them to the candidate set;
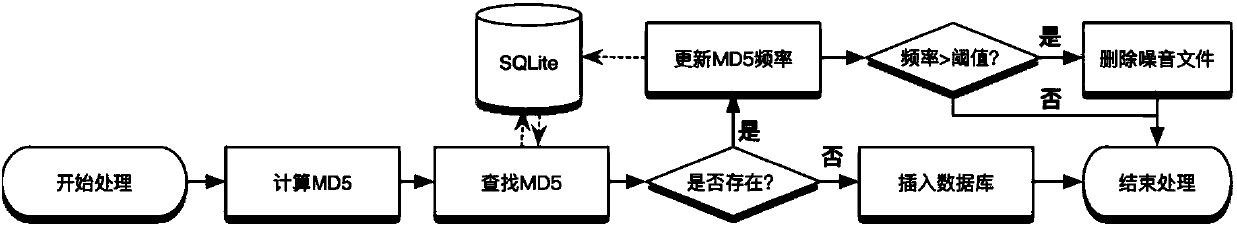
[0045] 4. Perform decompression and various conversion operations on the applications in the obtained suspicious clone application collection, and obtain all XML format layout files in the / res / layout directory;
[0046] 5. Filter the layout files, and use a statistical method to filter out external layout files introduced by third-party libraries;
[0047] 6. Convert the filtered layout file into a layout tree of the corresponding structure, and load it into the memory;
[0048] 7. Perform merging o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com