Double-factor authentication security supervisor login system and method
A technology of login system and login method, which is applied in the field of two-factor authentication security management machine login system, can solve problems such as system paralysis, malicious operation, and security management machine damage, and achieve the effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
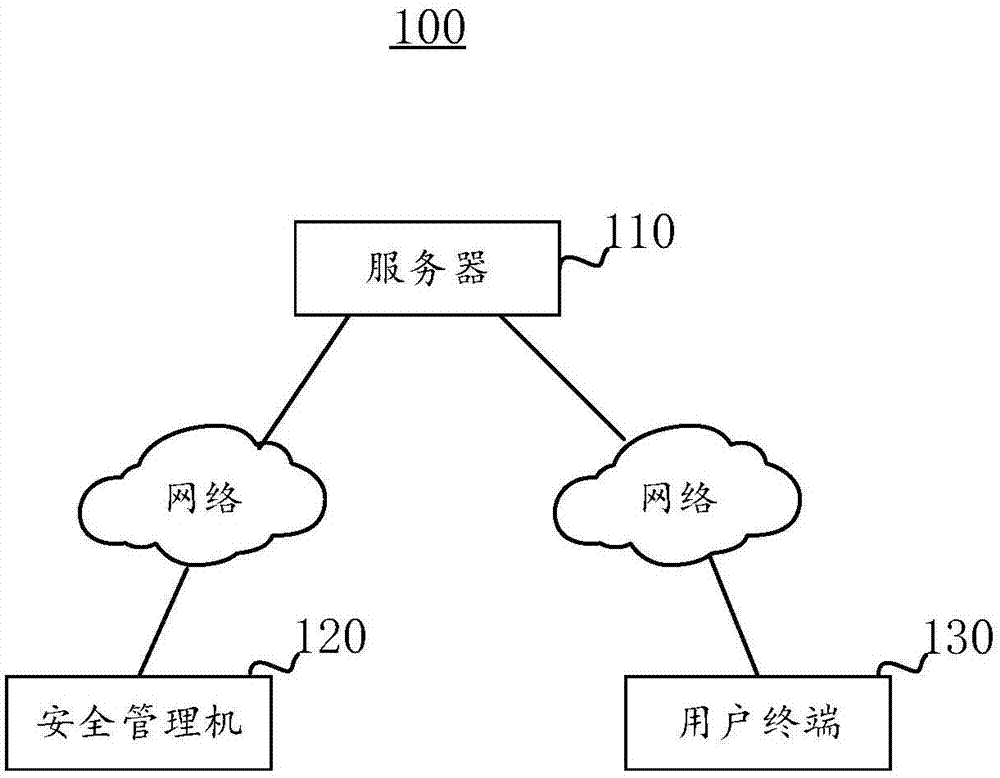
[0033] The embodiment of the present invention provides a two-factor authentication security management machine login system 100, please refer to figure 1 , figure 1 A schematic diagram of functional modules of the two-factor authentication security management machine login system 100 provided by the embodiment of the present invention is shown.
[0034] The two-factor authentication security management machine login system 100 includes a server 110 , a user terminal 130 and a security management machine 120 . Wherein, both the user terminal 130 and the security management machine 120 are communicatively connected to the server 110 through a network.
[0035] It should be noted that the server 110 has simple functions such as registering an account, storing the account, storing the unique identification information of the security management machine 120, and the management relationship between them. At the same time, the server 110 also provides functions such as retrieving ...
no. 2 example
[0050] This embodiment provides a two-factor authentication security management machine login method. The two-factor authentication security management machine login method can be applied to the two-factor authentication security management machine login system 100 provided in the first embodiment.
[0051] It should be noted that the basic principles and technical effects of the two-factor authentication security management machine login method provided by this embodiment are the same as those of the above-mentioned embodiments. Corresponding content in the above-mentioned embodiment.
[0052] see Figure 4 , the two-factor authentication safety management machine login method includes the following steps:
[0053] Step S10: The security management machine 120 verifies the account number and password input by the user.
[0054] First, verify the account number and password input by the user. In particular, in the scenario where the security management machine 120 is logged...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap