Quantum identity authentication method and application method of quantum identity authentication method in quantum key distribution process
An identity authentication and quantum technology, applied in key distribution, can solve problems such as security difficulties, and achieve the effect of clear principle, high security, and high security identity authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
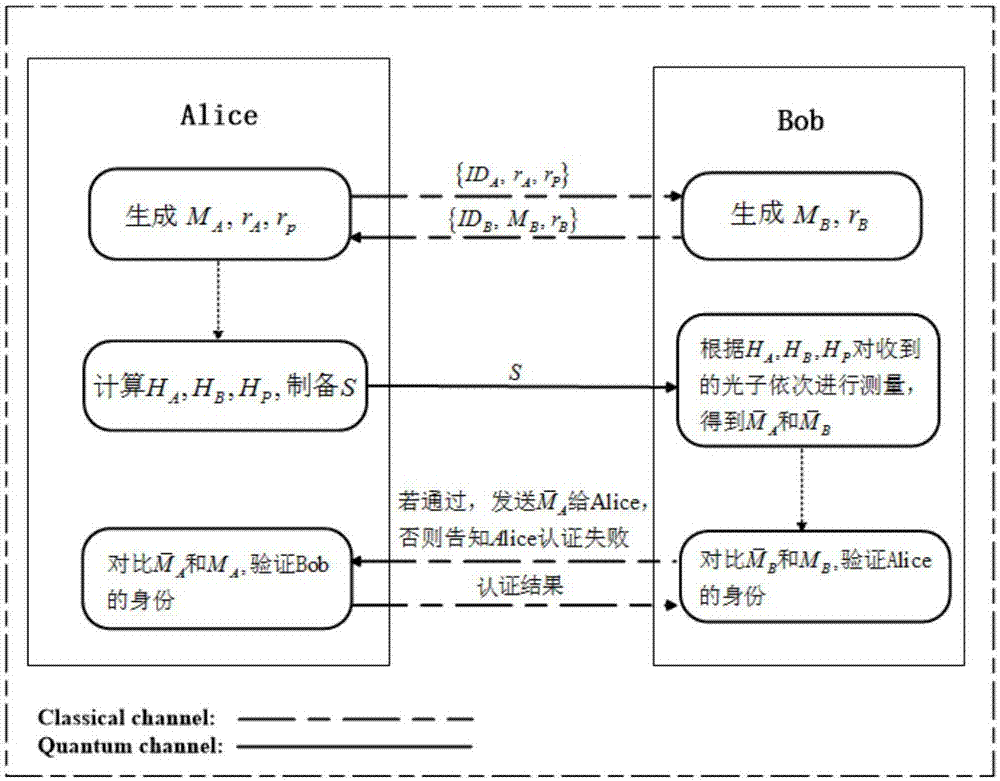
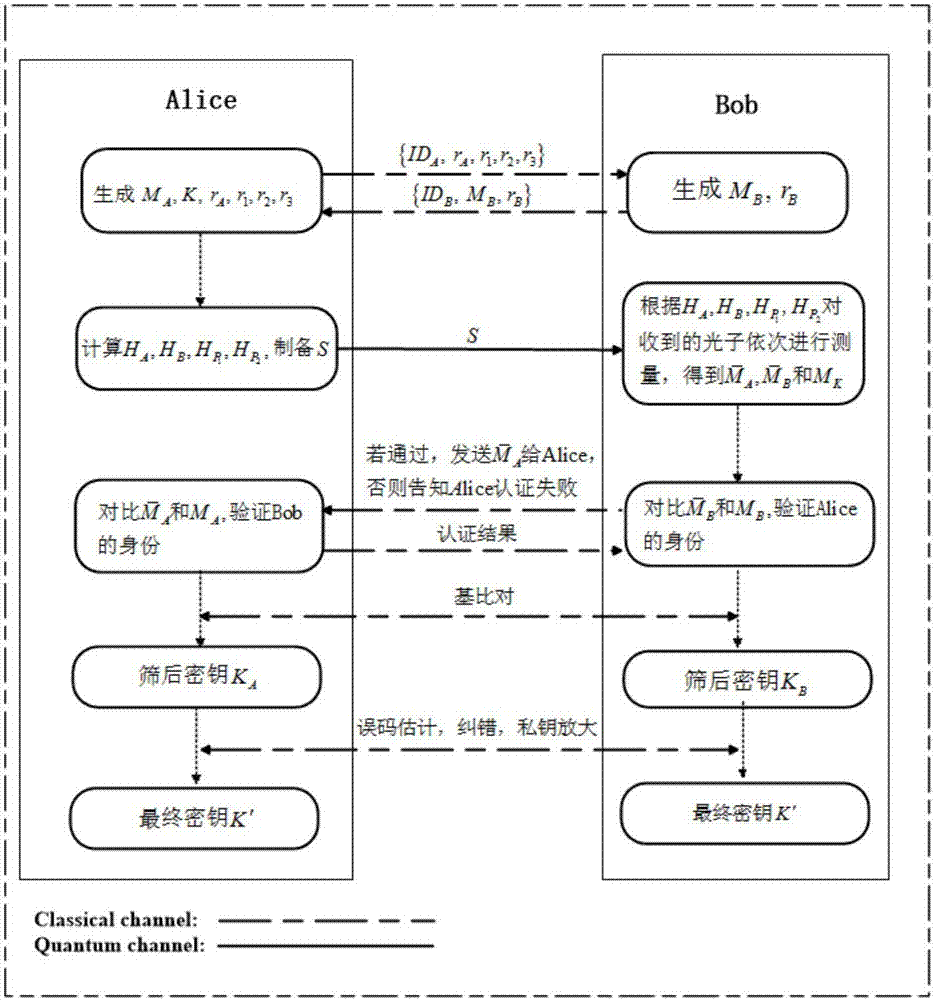
[0017] Authentication scheme:
[0018] Such as figure 1 As shown, suppose Alice and Bob are two parties that need mutual identity authentication, and they have shared two strings of s-long secret bit sequence K in advance P and K AB (Here Alice and Bob can be two ordinary users who need to exchange information; one can also be an ordinary user and the other an authentication center). The identity sequence of Alice and Bob is divided into ID A and ID B , and they negotiated a one-way Hash function h:{0,1} in advance * →{0,1} m (The function h can also be selected from a Hash function library shared by both parties through an agreed algorithm). Among the above parameters, K P and K AB is confidential, ID A 、ID B and h is public. The steps for Alice and Bob to authenticate each other are as follows:
[0019] 1. When Alice and Bob need to perform mutual identity authentication, Alice first generates a series of m-bit long messages M A and two random numbers r A and r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com