On-demand password service method, apparatus and device
A technology of cryptographic services and cryptographic equipment, applied in the field of cryptographic on-demand services, can solve the problems of online concurrent random crossing, cryptographic computing resources cannot be dynamically configured, managed and scheduled, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] refer to figure 1 As shown in FIG. 1 , it is a schematic flowchart of the password on-demand service method in Embodiment 1 of the present invention. In this embodiment, the password on-demand service method includes:
[0045] Step 101: Analyze cryptographic service requirements and generate cryptographic computing resource configuration requirements or cryptographic job scheduling policies according to cryptographic service requirements;
[0046] Step 102: Cryptographic service configuration management generates cryptographic computing resource configuration instructions according to cryptographic computing resource configuration requirements;
[0047] Step 103: The flexible reconstruction of cryptographic computing resources generates cryptographic reconstruction instructions according to the cryptographic computing resource configuration instructions and / or sends cryptographic reconstruction resources to the cryptographic computing pool, and the cryptographic comput...
Embodiment 2
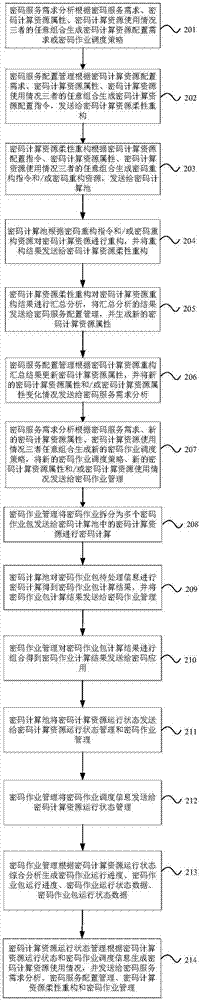
[0058] refer to figure 2As shown, it is a flow chart of the password on-demand service method in Embodiment 2 of the present invention. In this embodiment, the password on-demand service method includes:
[0059] Step 201: Analyze cryptographic service requirements Receive cryptographic service requirements, and generate cryptographic jobs when it is determined that existing cryptographic computing resources meet cryptographic service requirements based on any combination of cryptographic service requirements, cryptographic computing resource attributes, and cryptographic computing resource usage The scheduling policy is sent to the password job management, and the configuration and management of the password resources required by the password service are completed, and the process is directly transferred to step 208 to perform password job management and scheduling;
[0060] Optionally, when it is determined that the existing cryptographic computing resources do not meet th...
Embodiment 3
[0130] This embodiment is used to illustrate a process of cryptographic service requirement analysis, cryptographic service configuration management, and cryptographic computing resource flexible reconstruction to realize cryptographic service requirement analysis and cryptographic computing resource configuration. refer to Figure 4 As shown, the password on-demand service method of this embodiment includes:
[0131] Step 301: Analyze cryptographic service requirements and receive cryptographic service requirements from upper layer cryptographic applications;
[0132] Step 302: Analysis of cryptographic service requirements According to any combination of cryptographic service requirements, cryptographic computing resource attributes, and cryptographic computing resource usage, analyze whether the existing cryptographic computing resources meet the cryptographic service requirements. If they meet, go to step 303; otherwise, go to Step 304;
[0133] Step 303: The cryptograph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com