GCC-based hijack attack defense method for fine-grained virtual function table
A virtual function table and virtual function technology, which is applied in the field of fine-grained virtual function table hijacking attack defense based on GCC, can solve the problems of security to be improved, compatibility and overhead affecting the execution efficiency of defense methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments.
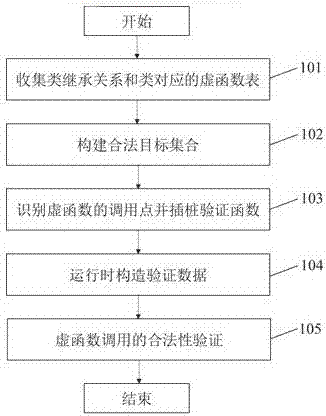
[0079] Such as figure 1 As shown, a GCC-based fine-grained virtual function table hijacking attack defense method, the overall structure and working principles include:
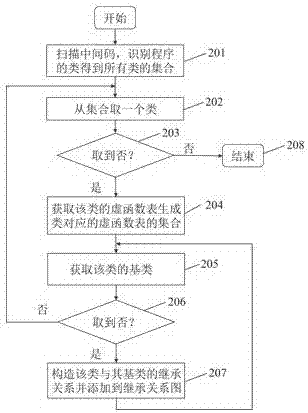
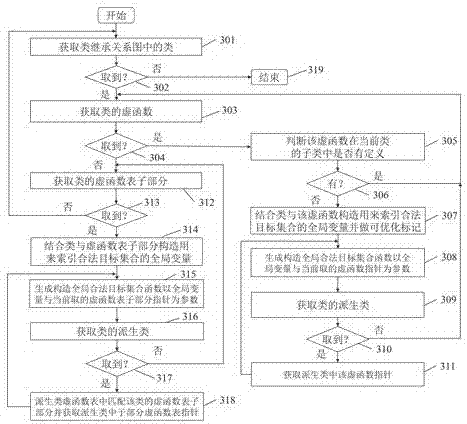
[0080] 101: Collect the class inheritance relationship and the virtual function table corresponding to the class. The syntax analysis stage in the GCC compilation process generates intermediate language, analyzes the intermediate language to identify the classes in the program, builds the class inheritance diagram, and records its virtual function table set for each class as the basis for constructing a legal target set. In GCC, the macro RECORD_TYPE indicates the type declared by struct or class, which can identify the class in the program. Each class has a macro BINFO to associate the parent class and subclass, and the parent class and virtual function table info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com