Attack test system and method for wireless router
A technology for wireless routers and attack testing, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as inability to accurately simulate attack scenarios and difficulty in setting up test environments, and achieve flexible attack testing, high testing efficiency, and comprehensive testing Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] refer to Figure 4 , a kind of attack test method for wireless router comprises:
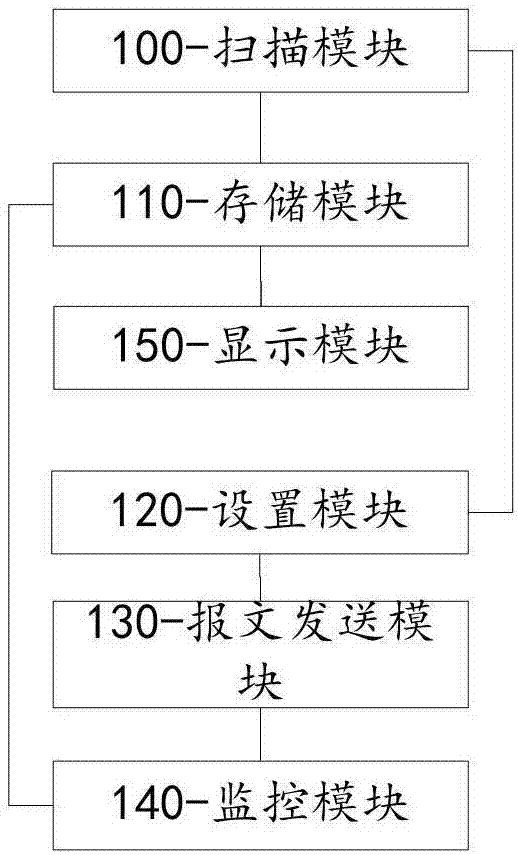
[0086] Step S100 scans wireless signals in the environment, and selects a target router according to the scanning result;
[0087] Step S200 When other terminals are associated with the target router, the test system also monitors the message interaction between the two;
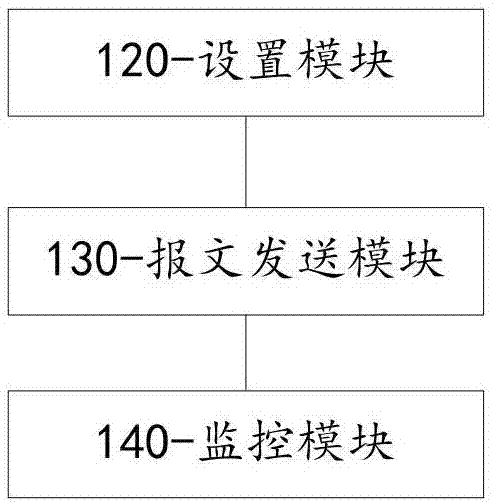
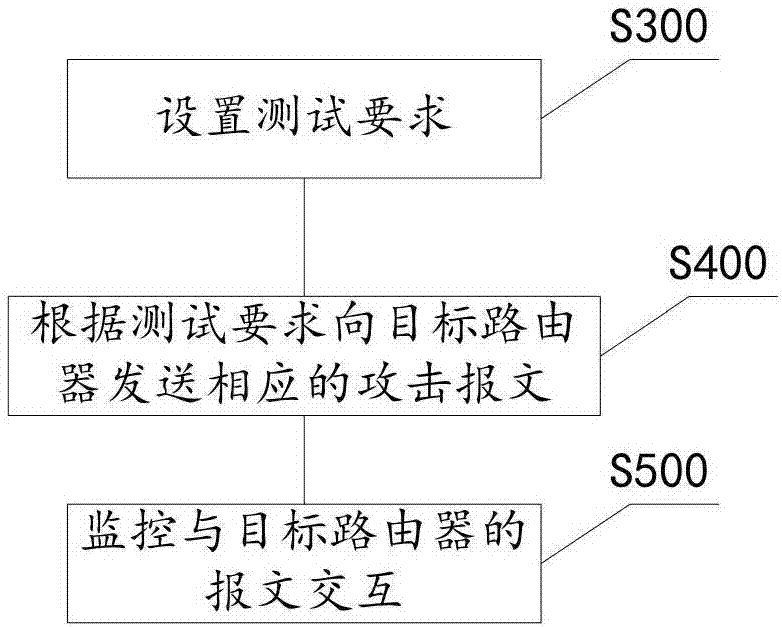
[0088] Step S300 sets test requirements;
[0089] Step S400 sends a corresponding attack message to the target router according to the test requirements;
[0090] Step S500 monitors message interaction with the target router;
[0091] The test requirement includes at least one of test type, packet quantity, and packet frequency.
[0092] Compared with the aforementioned basic flow, this embodiment specifically adds step S100, which can set the test object more conveniently. By scanning the wireless signals in the environment, the test system can obtain all wireless routers in the test environment, which is similar ...
Embodiment 2
[0097] refer to Figure 5 , a kind of attack test method for wireless router comprises:
[0098] Step S110 scans the wireless signals in the environment, displays the scan results, and selects the target router;
[0099] Step S210 When other terminals are associated with the target router, the test system also monitors the message interaction between the two, and displays;
[0100] Step S300 sets test requirements;
[0101] Step S400 sends a corresponding attack message to the target router according to the test requirements;
[0102] Step S510 monitors and displays message interaction with the target router;
[0103] The test requirement includes at least one of target router information, test type, packet quantity, and packet frequency; and / or, the test requirement further includes multiple target router information and / or multiple test types and / or multiple message quantities and / or multiple message frequencies.
[0104] Compared with Embodiment 1, this embodiment adds ...
Embodiment 3
[0106] refer to Figure 5 , a kind of attack test method for wireless router comprises:
[0107] Step S110 scans the wireless signals in the environment, displays the scan results, and selects the target router;
[0108] Step S210 When other terminals are associated with the target router, the test system also monitors the message interaction between the two, and displays;
[0109] Step S300 sets test requirements;
[0110] Step S400 sends a corresponding attack message to the target router according to the test requirements;
[0111] Step S510 monitors and displays message interaction with the target router;
[0112] The test requirements include at least one of test type, message quantity, and message frequency;
[0113] There are multiple target routers, there are multiple test requirements, and the multiple target routers match the multiple test requirements one by one; and / or, the tests of the multiple target routers are independent of each other.
[0114] The flow c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com