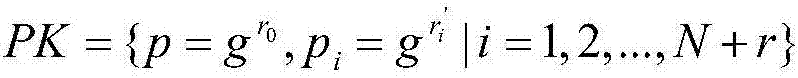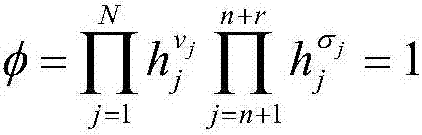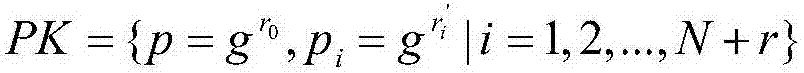Homomorphic signature method for intra-generation/inter-generation attack resistance
A homomorphic and message signature technology, applied in the field of network coding, can solve problems such as large amount of computation, reduce homomorphic signatures, and intergenerational pollution, and achieve high security performance and low computational overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0057] 1. Analyze the correctness of a homomorphic signature method against intra-generational / inter-generational attacks proposed by the present invention:
[0058] Assuming that the nodes are vulnerable to attack, the correctness of the present invention is proved below.
[0059] Proof: Let V=span{s 1 ,s 2 ,...s r }, Sign outputs the message and signature vector u i ={v i ,σ i }, It is easy to know u⊥V from formula (4.3), just prove that Verify(id,v,σ,PK)=1
[0060] because make
[0061] {v,σ}=Combine(id,α i ,v i ,σ i ), (i=1,2,...,l), from the formula (4.5) we can know
[0062]
[0063] Among them, v j and σ j represent the jth and n+j components of u respectively, v ij and σ ij represent u respectively i The jth, n+jth components,
[0064] It can be deduced from u⊥V roll out:
[0065]
[0066] Theorem proved.
[0067] Two, prove the security of the present invention:
[0068] The description of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com