Hardware implementation system for SM2 elliptic curve public key encryption algorithm under pixel field Fp
A public-key encryption algorithm and elliptic curve technology, which is applied in the field of message encryption and decryption, hardware implementation system of SM2 elliptic curve public-key encryption algorithm, and can solve problems such as large consumption of hardware resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
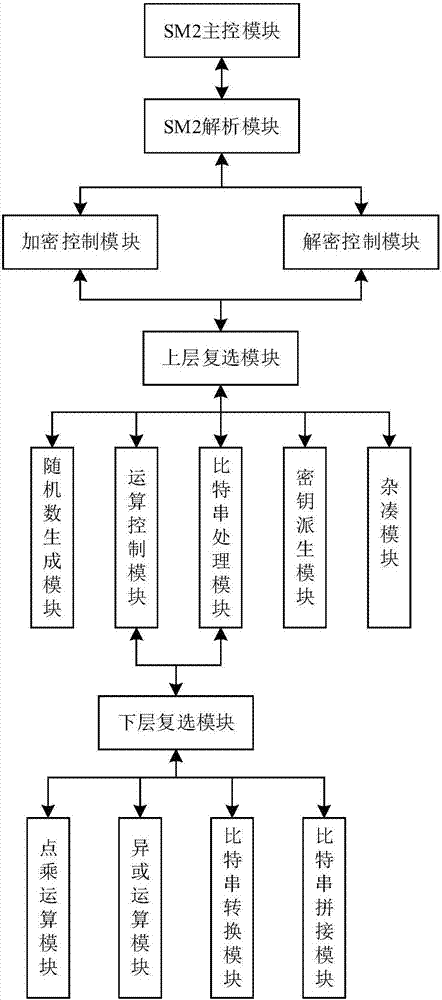
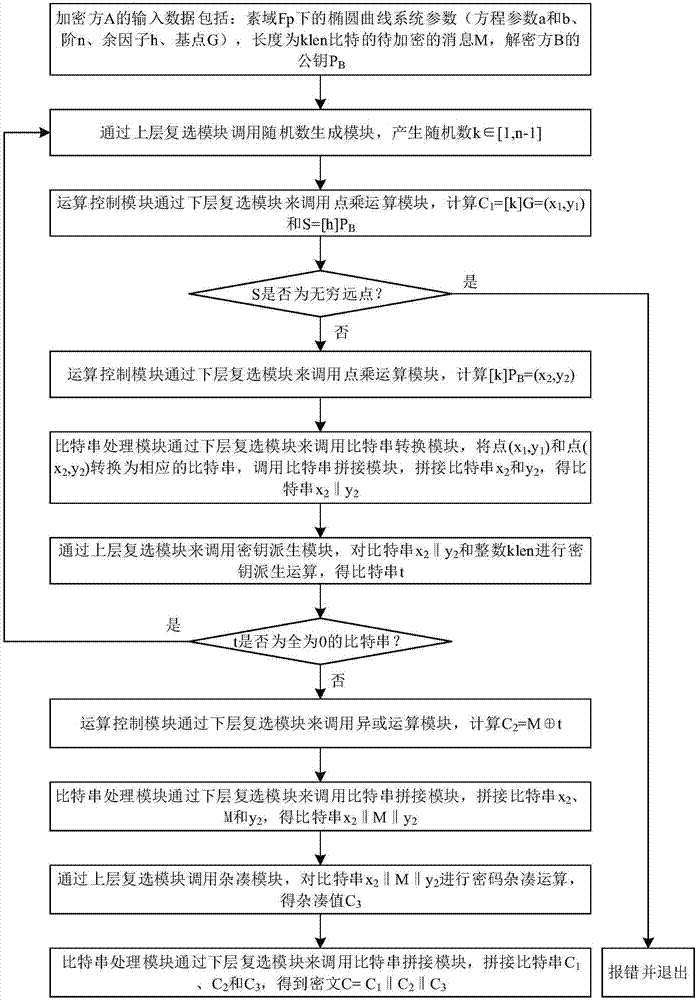
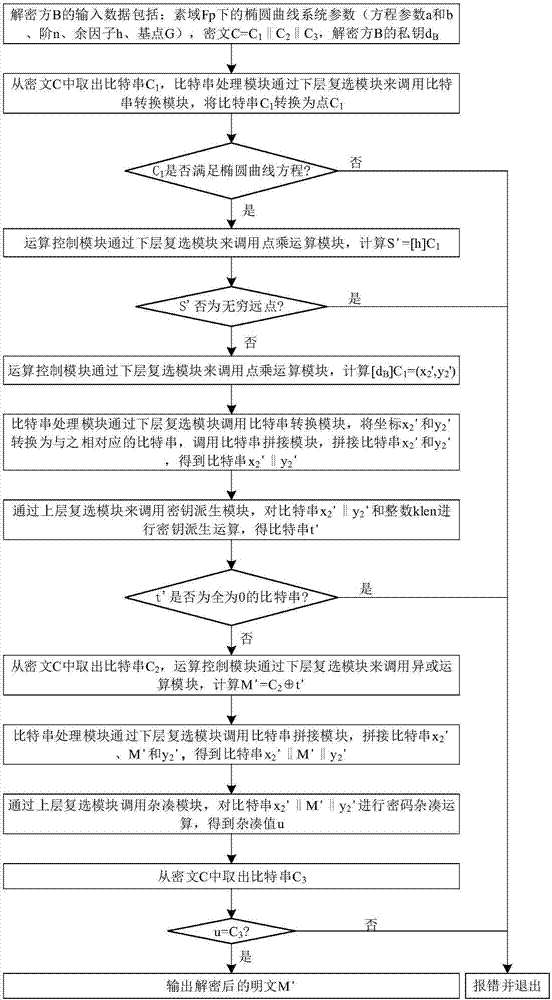
[0062] The present invention provides a hardware implementation system of the SM2 elliptic curve public key encryption algorithm under the prime field Fp. The SM2 elliptic curve and algorithm involved in the present invention are all defined on the prime field Fp, where p is greater than 3 Prime number. The elliptic curve equation on the prime field Fp is y 2 x 3 +ax+b, where a, b∈Fp, and (4a 3 +27b 2 ) mod p ≠ 0.
[0063] figure 1 The overall structural diagram of the hardware implementation system of the SM2 elliptic curve public key encryption algorithm under a kind of prime field Fp provided by the present invention, this system can realize the encryption and decryption to the message from the hardware, guarantee the security of the message, prevent the message Attacked during transmission, thus being intercepted or destroyed by criminals. The modules used in the system include: SM2 main control module, SM2 analysis module, encryption control module, decryption contr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com