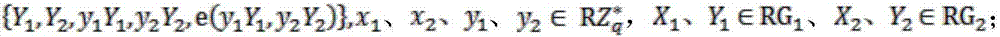Security outsourcing method for two bilinear pairings based on dual cloud servers
A bilinear pairing and secure outsourcing technology, applied in the field of cloud computing, can solve the problems of high computing cost, high estimated complexity, and unsatisfactory computing efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
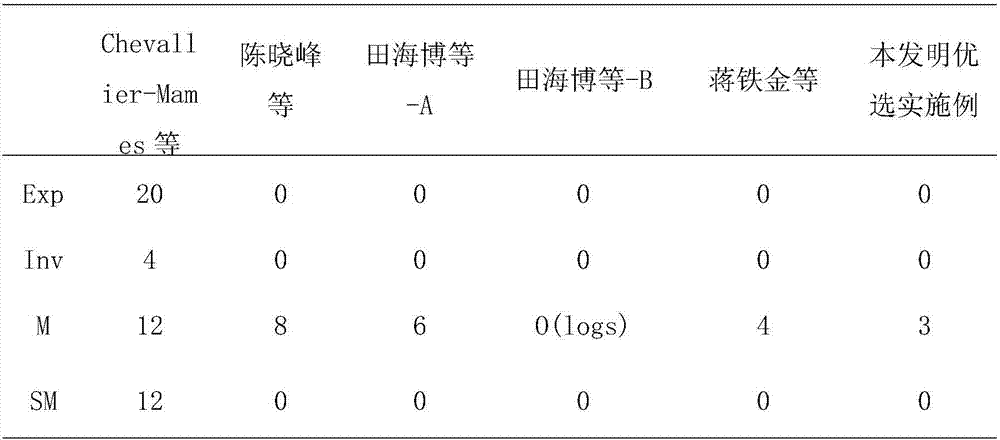
Method used
Image
Examples
Embodiment Construction
[0049] Preferred embodiments of the present invention are described in detail as follows:
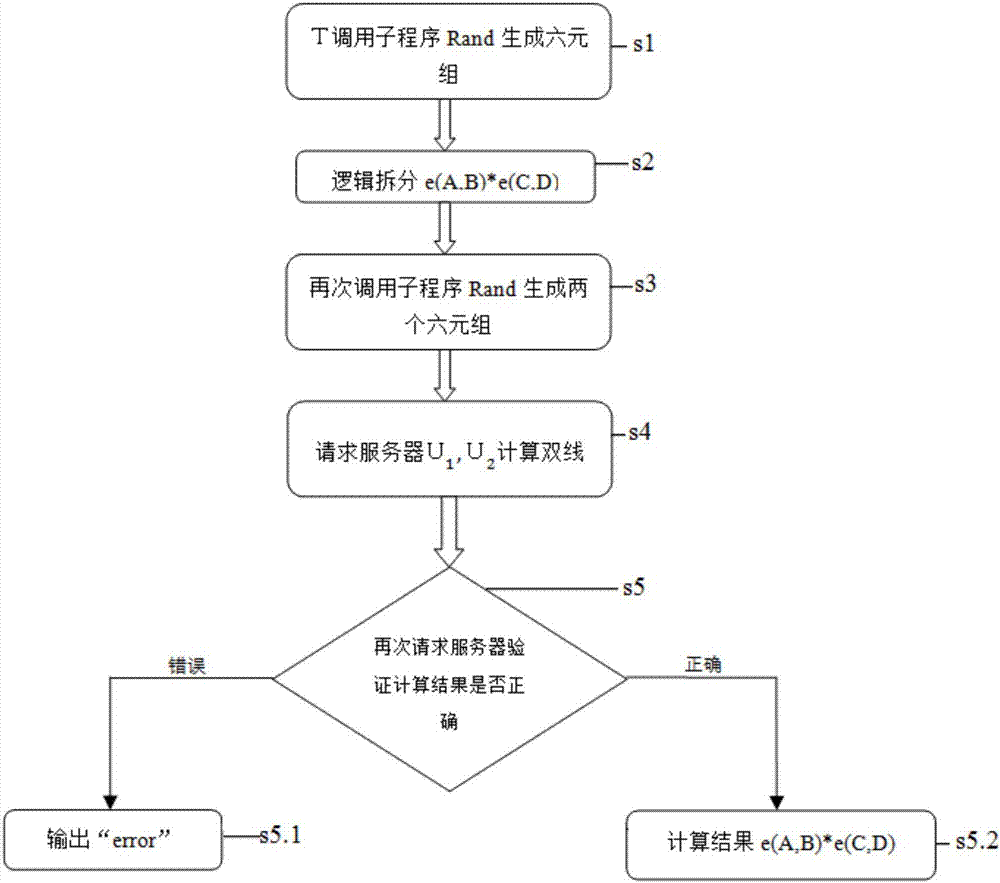
[0050] In this example, see figure 1 , a security outsourcing method for two bilinear pairings based on two servers, comprising the following steps:
[0051] Step 1: The outsourced user T calls the program Rand to generate a six-tuple, where Rand is a subroutine used to improve the calculation speed, and is used to pass the server U 1 with U 2 To realize the outsourced method M-Pair of bilinear pairing, specifically: the outsourced user T first needs to call the program Rand, input G 1 , G 2 , a bilinear pairing and other random numbers, generate and output a six-tuple {V 1 , V 2 , v 1 V 1 , v 2 V 2 , e(v 1 V 1 , v 2 V 2 )}, {V 1 , V 2 , v 1 V 1 , v 2 V 2 , e(v 1 V 1 , v 2 V 2 )} results can be pre-calculated, where v 1 , V 1 ∈RG 1 , V 2 ∈RG 2 , is a random number in the remainder class modulo q with zero elements removed, RG 1 is G 1 A random point in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com