A Jump Covert Communication Method Based on DNA Encryption
A covert communication and transition technology, applied in transmission systems, electrical components, etc., can solve problems such as powerlessness, achieve the effects of avoiding congestion, ensuring concealment, improving message transmission efficiency and system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in further detail below with reference to the accompanying drawings.
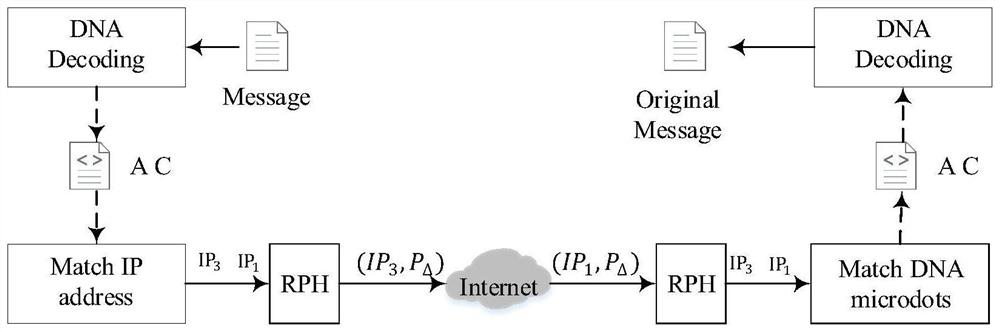
[0057] like image 3 As shown, the DNA encryption-based hopping concealment communication method of the present invention, the steps are:
[0058] (1) Deploy the message receiving server and the message sending client;
[0059] (2) The client inputs and transmits the text content, and then encrypts the text content into a text sequence of letters A-P;
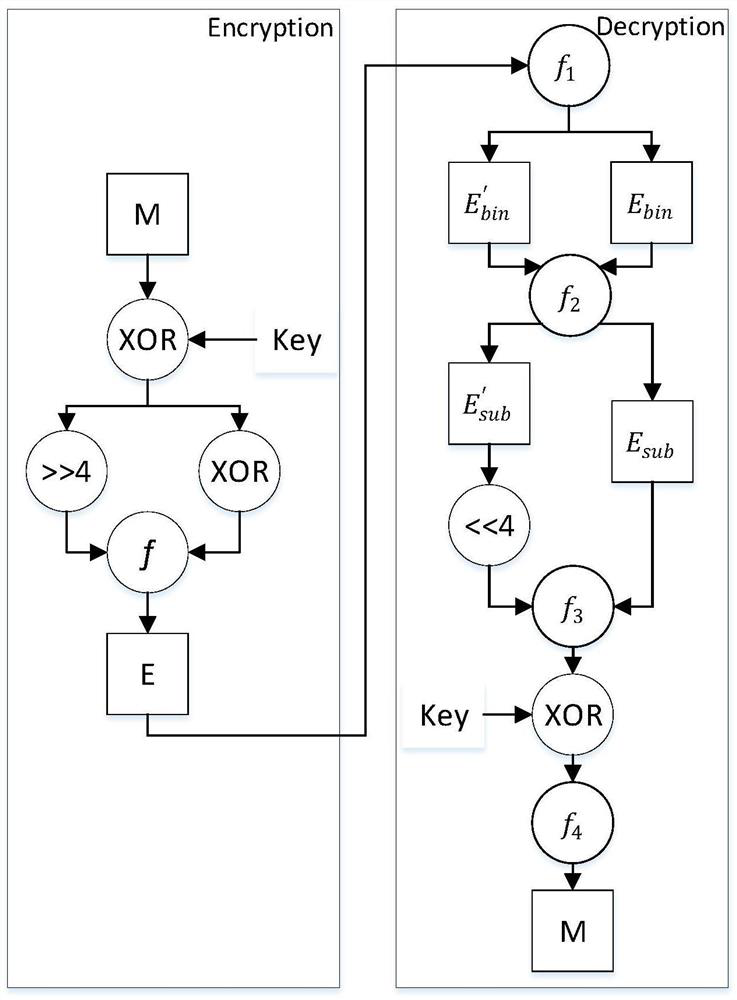
[0060] (3) The client performs DNA encryption on the text sequence whose ciphertext is the letters A-P, that is, converts it into a base sequence consisting of A (adenine), T (thymine), G (guanine), and C (cytosine);
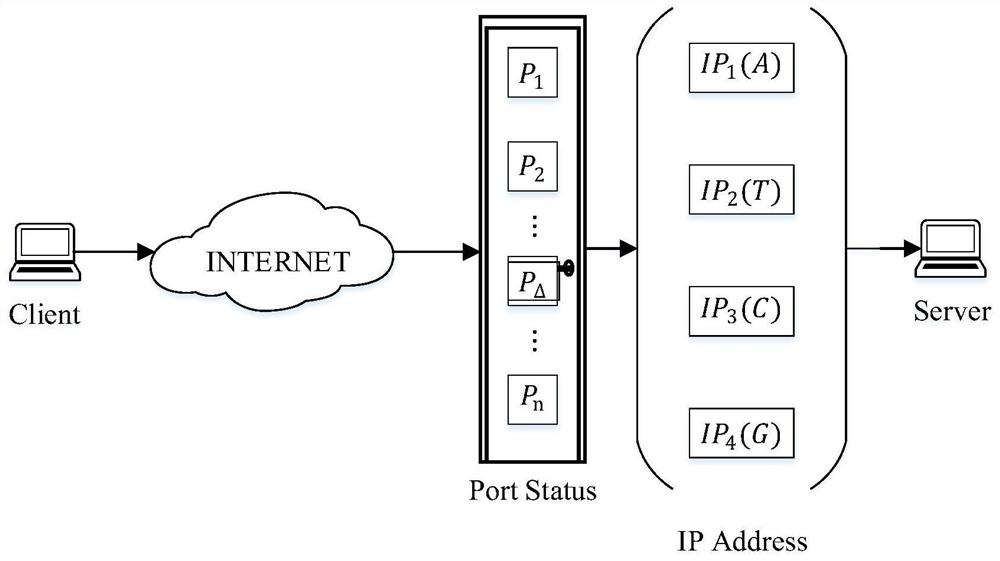
[0061] (4) Four IP addresses are configured on the server side IP={ip 1 , ip 2 , ip 3 , ip 4 } Corresponding to the four bases of DNA respectively, the client sequentially accesses the corresponding IP of the server according to the encrypted DNA sequence to send the DNA encrypted sequence; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com