Design method and system for anti-hardware Trojan horse chip
A chip design, hardware Trojan technology, applied in CAD circuit design, computing, special data processing applications, etc., can solve problems such as chip hardware Trojan attacks, and achieve the effect of increasing the conversion probability, increasing the probability of being activated, and improving the conversion probability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
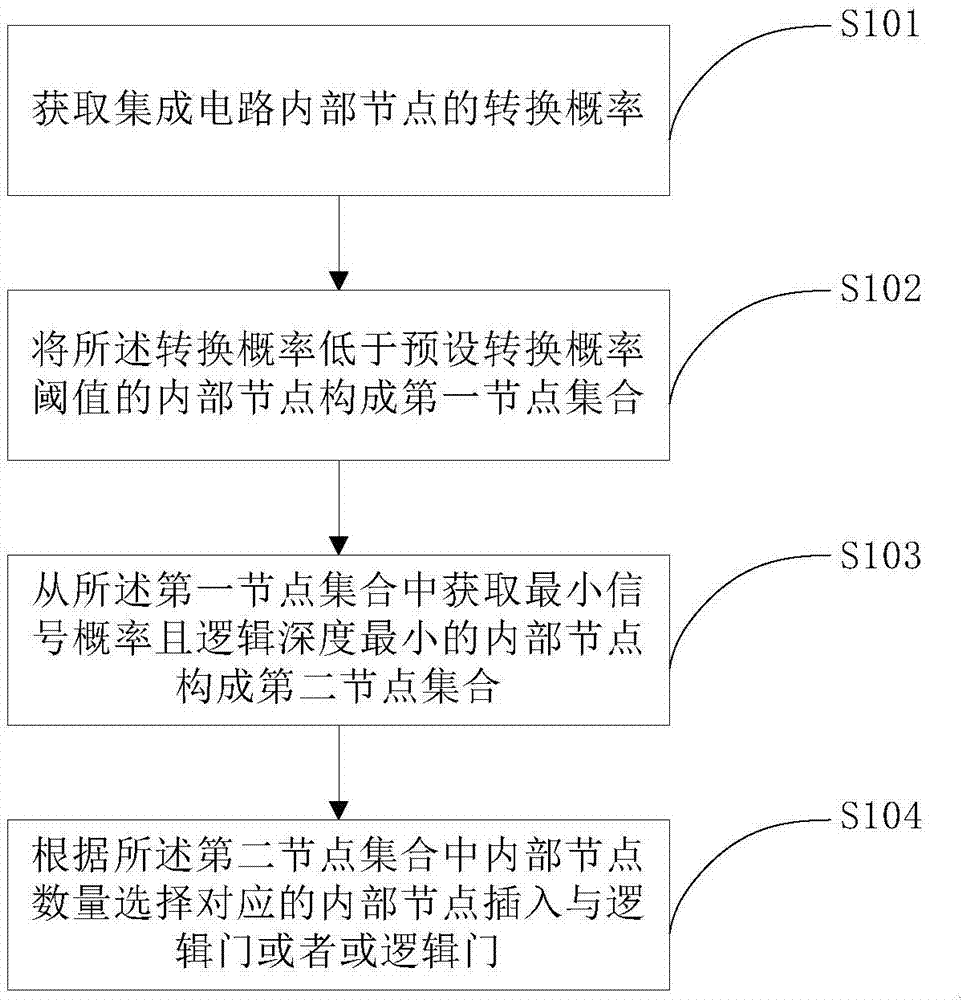
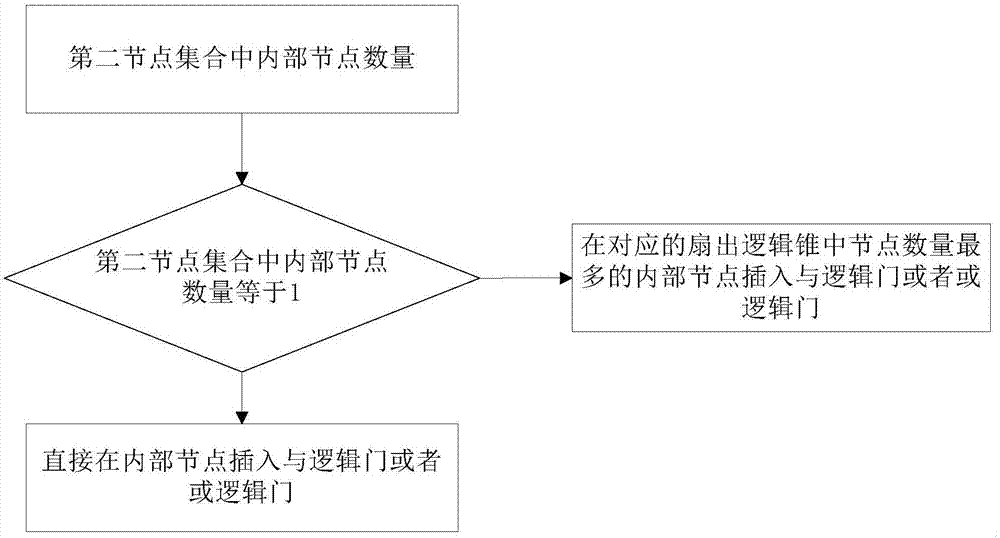
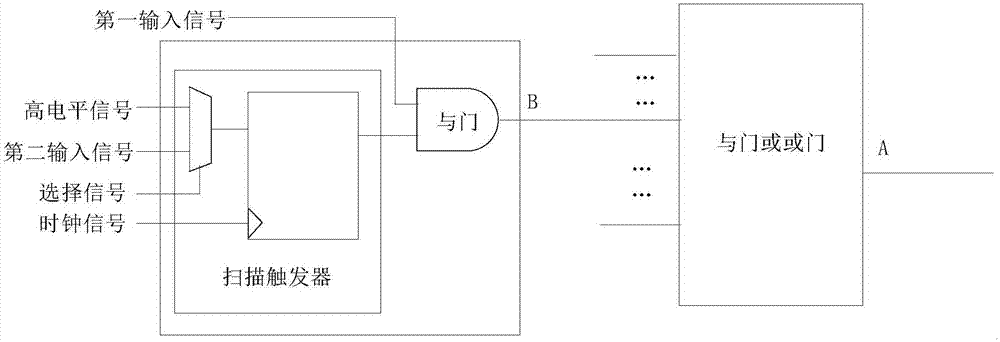
[0022] see figure 1 , is a flow chart of an embodiment of the anti-hardware Trojan chip design method provided by the present application. Such as figure 1 As shown, the method includes:
[0023] S101. Obtain transition probabilities of internal nodes of the integrated circuit.
[0024] The integrated circuit contains many internal nodes, and the signal probability of each internal node is calculated, and the signal probability includes the input signal probability and the output signal probability. For a logic gate in an integrated circuit, the input probability of the initial internal node is generally known, and the output probability of the corresponding logic gate can be calculated through the input probability. For example, the signals of the two input internal nodes of a 2-input AND gate are known, and the probability of a high-level signal is 0.5, then the signal probability of a high-level signal output at the output is 0.5*0.5=0.25, then the output signal The pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com