Blockchain privacy protection method based on asymmetric encryption
An asymmetric encryption and privacy protection technology, which is applied in user identity/authorization verification, digital transmission systems, electrical components, etc., can solve the problems of few third-party institutions and untrustworthiness, and achieve the effect of flexible user authorization data access mode
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
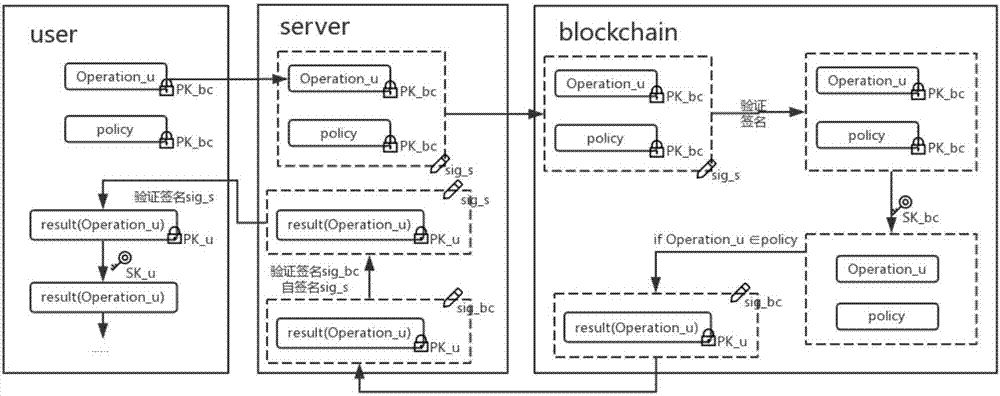
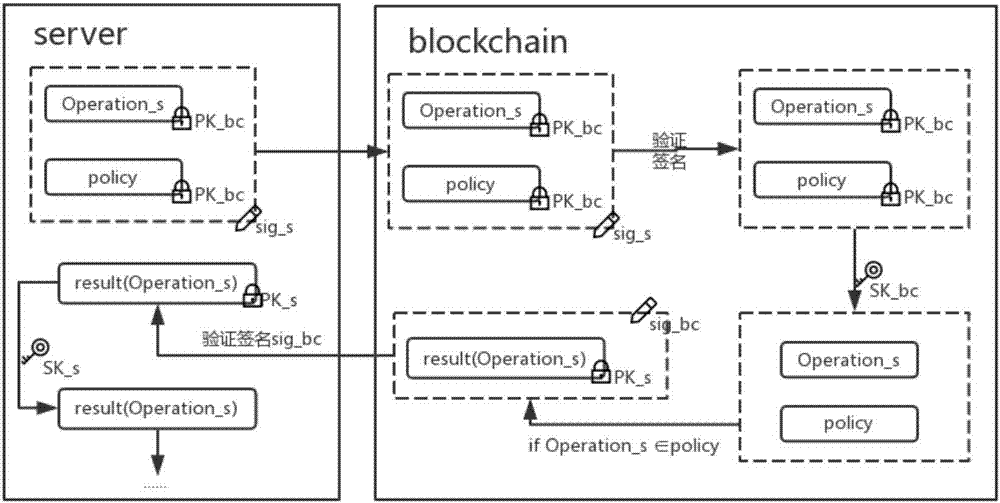
[0027] In order to describe the present invention more specifically, the technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0028] In this embodiment, for each encryption process, an encryption module is established. The encryption module involves the user object user, the untrusted object server providing data operation services, and the data storage object blockchain, so as to realize the authorization management mechanism when the server accesses user data.
[0029] In this embodiment, when the data operation service is provided by an untrusted third-party organization, a highly flexible user-authorized data access mode is established. The specific execution steps are as follows:
[0030] (1) Creation and cancellation of authorized operations.
[0031] 1-1. Generate corresponding public keys and private keys (PK_u, SK_u, PK_s, SK_s, PK_bc, SK_bc) for user, server and blockc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com