Encryption and decryption method and equipment for user resource
A technology of user resources and encryption methods, applied in transmission systems, electrical components, etc., can solve problems such as user information leakage in application platforms, reduce the risk of being leaked, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
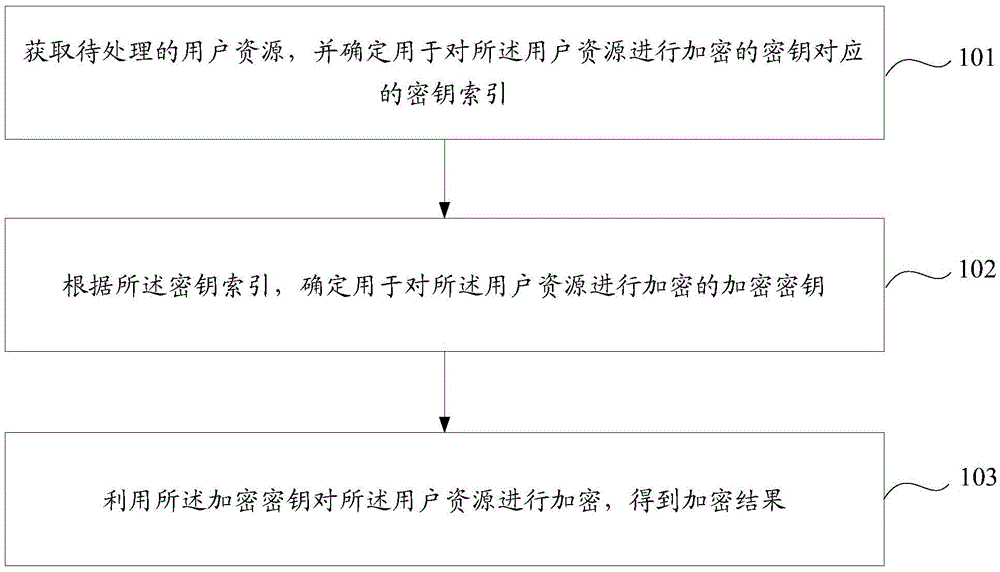
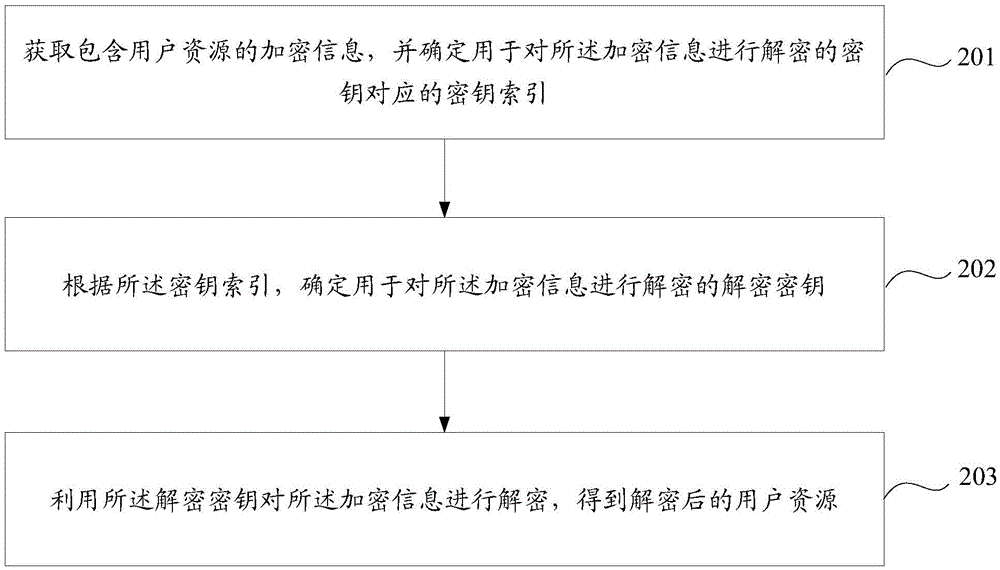
[0030] In order to achieve the purpose of this application, an encryption method and device for user resources are provided in the embodiment of this application, which acquires user resources to be processed and determines the encryption key corresponding to the key used to encrypt the user resources. key index; determine an encryption key used to encrypt the user resource according to the key index; use the encryption key to encrypt the user resource to obtain an encryption result. By determining the key index for the user resource, and determining the encryption key for encrypting the user resource according to the key corresponding to the key index, in this way, for different user resources, the probability that the encryption key determined by the system is different increase, which can effectively avoid the relatively fixed encryption method used to transmit user information between application platforms that have established a cooperative relationship in the prior art, r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com