A client-side image blurring and deduplication method that supports ownership authentication
An ownership authentication and client-side technology, applied in graphics and image conversion, image data processing, instruments, etc., can solve the problems that image quality evaluation methods cannot meet the requirements of high efficiency, accuracy, human perception, and does not involve image quality evaluation, etc., to achieve fast Efficient deduplication, saving storage resources and network bandwidth, and improving the effect of deduplication rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
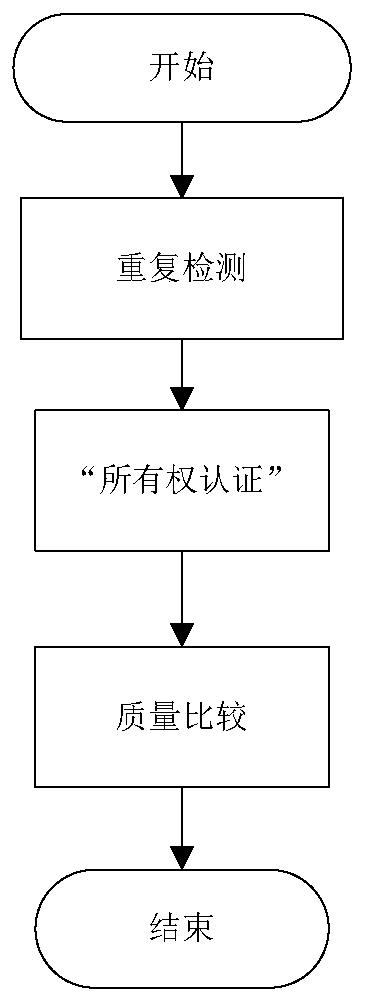
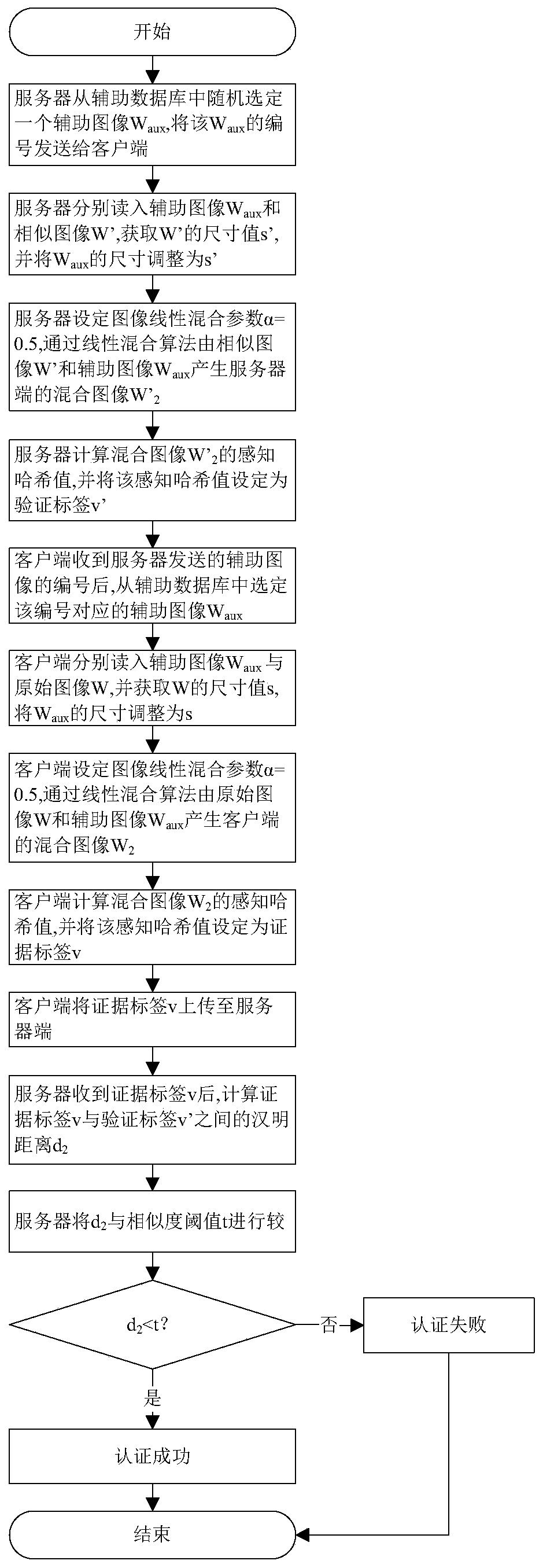
[0044] refer to figure 1 , the implementation steps of the present invention are as follows:
[0045] Step 1: Perform duplicate detection on the original image W to be deduplicated by the client.
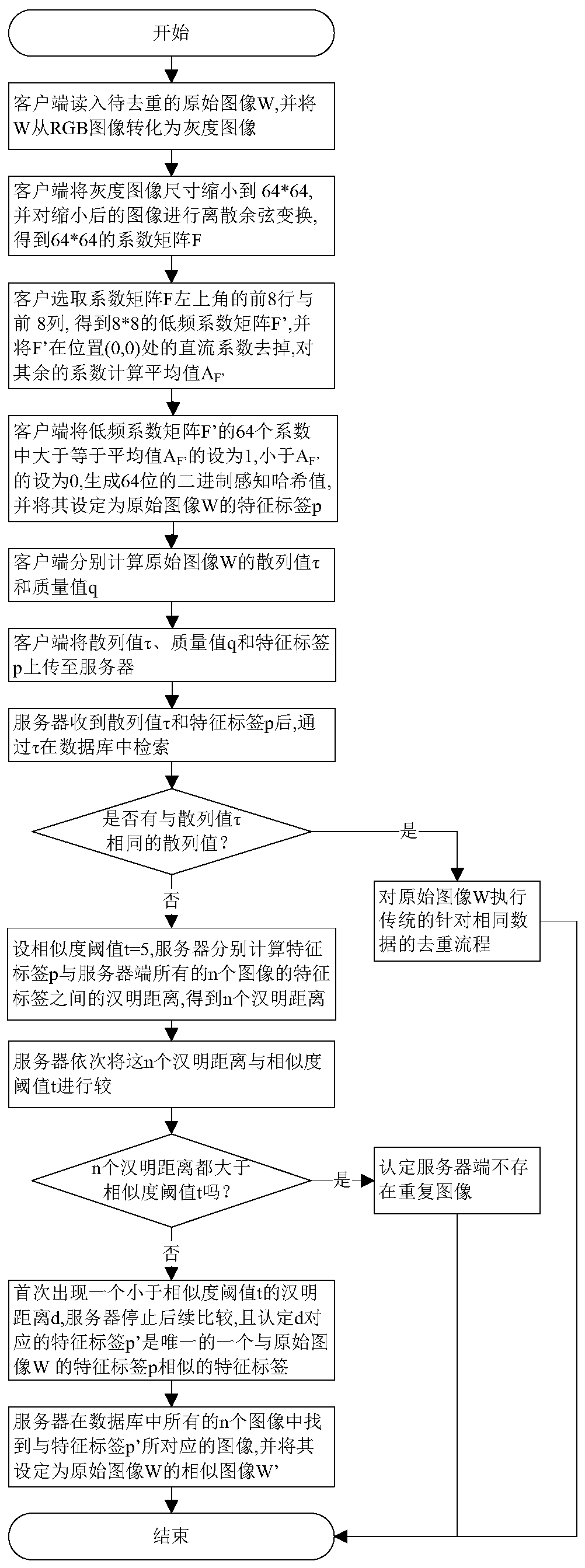
[0046] refer to figure 2 , the specific implementation of this step is as follows:
[0047] 1a) The client calls the imread function from the OpenCV function library to read in the original image W to be deduplicated, and calls the cvtColor function to convert W from an RGB image to a grayscale image, and then calls the resize function to reduce the size of the grayscale image to 64*64 , calling the dct function to perform discrete cosine transform on the reduced image to obtain a 64*64 coefficient matrix F;
[0048] 1b) The client selects the first 8 rows and the first 8 columns in the upper left corner of the coefficient matrix F to obtain an 8*8 low-frequency coefficient matrix F', which represents the low-frequency information of the original image W; then place F' in the po...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com