Method and device for user identification
A user identification and user technology, applied in the security field, can solve problems such as unfriendly user experience and poor restriction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
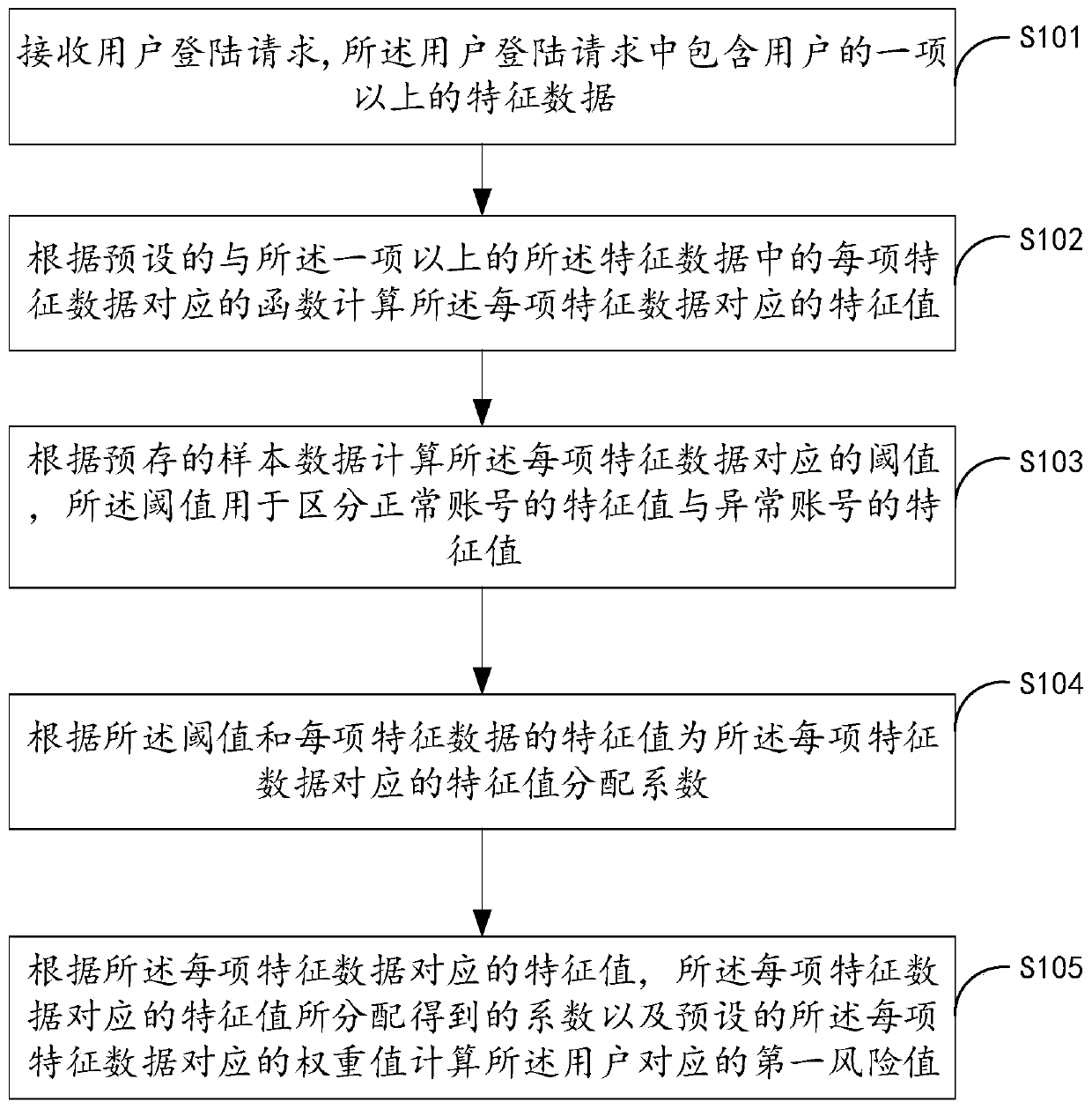
[0030] figure 1 It is a schematic flowchart of the user identification method provided by Embodiment 1 of the present invention. The user identification method is applied to electronic equipment, such as figure 1 As shown, the user identification method includes the following steps S101-S105.
[0031] Step S101, receiving a user login request, wherein the user login request is generated by an electronic device in response to a user's login operation.
[0032] Specifically, the user login request includes more than one characteristic data of the user. Wherein, the one or more items of characteristic data include, but are not limited to, registration time, last login time, current login time, registration information, completeness of registration information, similarity of registration information, user identity certificate UID ( Unique Identification) and request IP, etc. Wherein, the similarity of the registration information refers to the similarity between multiple piece...
Embodiment 2
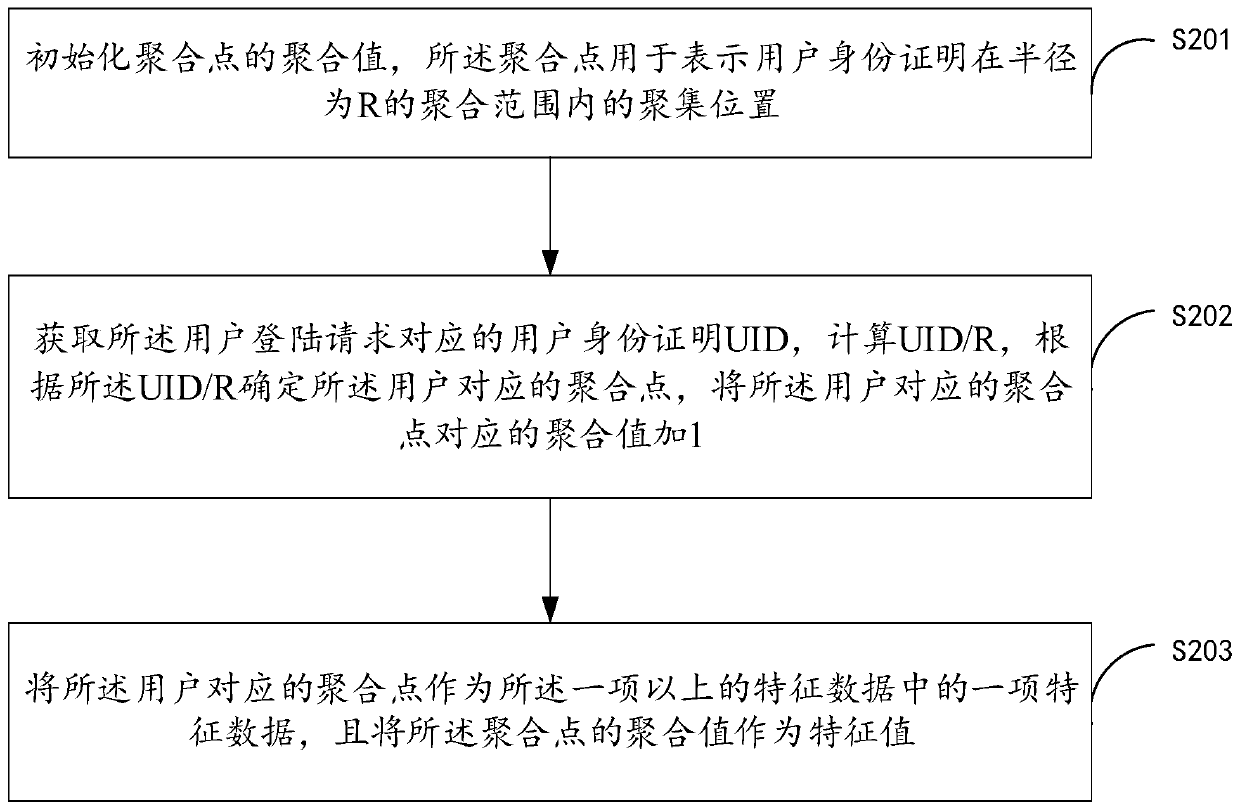
[0046] Embodiment 2 of the present invention is similar to Embodiment 1, the difference is that Embodiment 2 obtains one item of feature data among the above one or more items of feature data through the following method, wherein, figure 2 The schematic flowchart for obtaining a piece of feature data provided by Embodiment 2 of the present invention specifically includes steps S201-S203.
[0047] Step S201, initialize the aggregation value of the aggregation point, the aggregation point is used to represent the aggregation position of the user identity certificate within the aggregation range with a radius of R. Specifically, the aggregation values of the aggregation points are all initialized to 0. Wherein, the radius R refers to the number of all users participating in the current activity, for example, 1000.
[0048] Step S202, obtain the user identity certificate UID corresponding to the user login request, such as 10001, calculate UID / R, for example, 10001 / 1000=10, de...
Embodiment 3
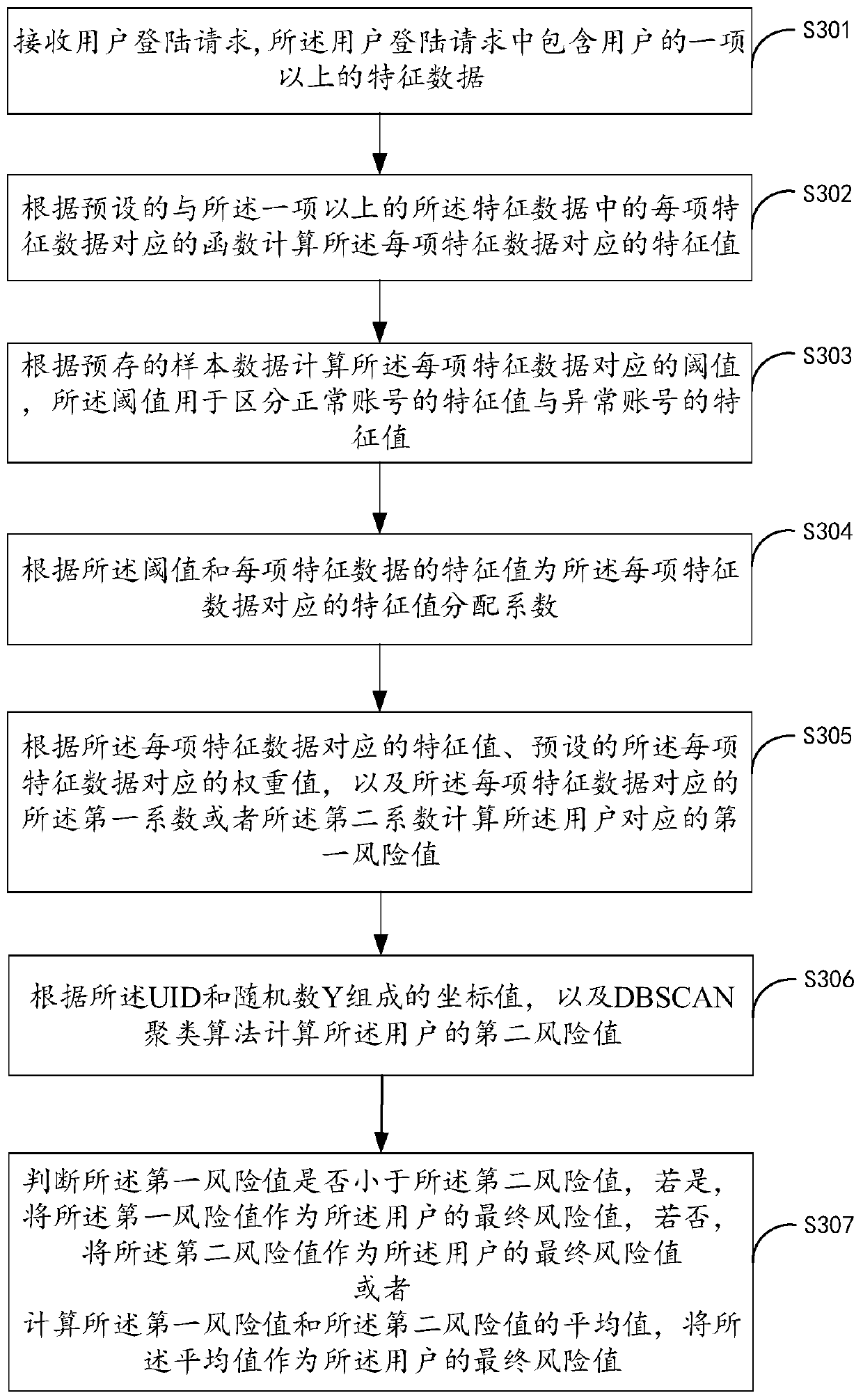
[0052] image 3 It is a schematic flowchart of the user identification method in Embodiment 3 of the present invention. The user identification method is applied to electronic equipment, such as image 3 As shown, the user identification method includes the following steps S301-S307.
[0053] Step S301, receiving a user login request, wherein the user login request is generated by an electronic device in response to a user's login operation.
[0054] Specifically, the user login request includes more than one characteristic data of the user. Wherein, the one or more items of characteristic data include, but are not limited to, registration time, last login time, current login time, registration information, completeness of registration information, similarity of registration information, UID and request IP, etc. . Wherein, the similarity of the registration information refers to the similarity between multiple pieces of registration information of the user, for example, if...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com