Security verification method and system
A security verification and verification code technology, applied in user identity/authority verification, digital data authentication, etc., can solve the problems of low resolution and poor experience of 12306 verification codes, solve the problem of incompatibility between security and user experience, and improve accuracy rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
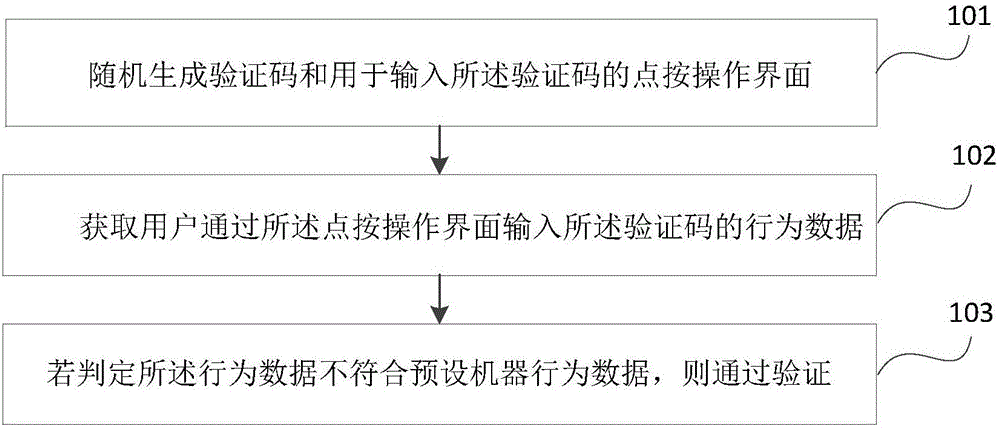
[0060] Such as figure 1 As shown, it is a flowchart of a security verification method according to an embodiment of the present invention, including the following steps:
[0061] Step 101, randomly generating a verification code and a point-and-click operation interface for inputting the verification code;
[0062] Step 102, acquiring the behavior data of the user inputting the verification code through the point-and-click operation interface;
[0063] What needs to be explained here is that what is acquired is the behavior data of inputting "the said verification code". Therefore, if it is not the said verification code, that is, if the input verification code is wrong, it will be ignored directly, and the behavior data will not be obtained and stored any more; at the same time Prompt the user for re-enter.
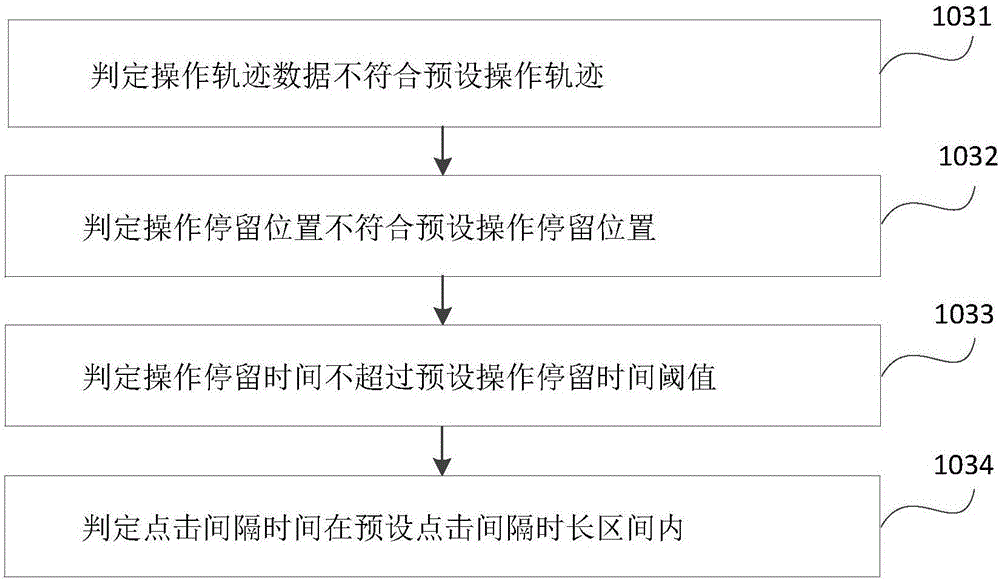
[0064] Step 103, if it is determined that the behavior data does not conform to the preset machine behavior data, the verification is passed.
[0065] preferred,
[...
Embodiment 2
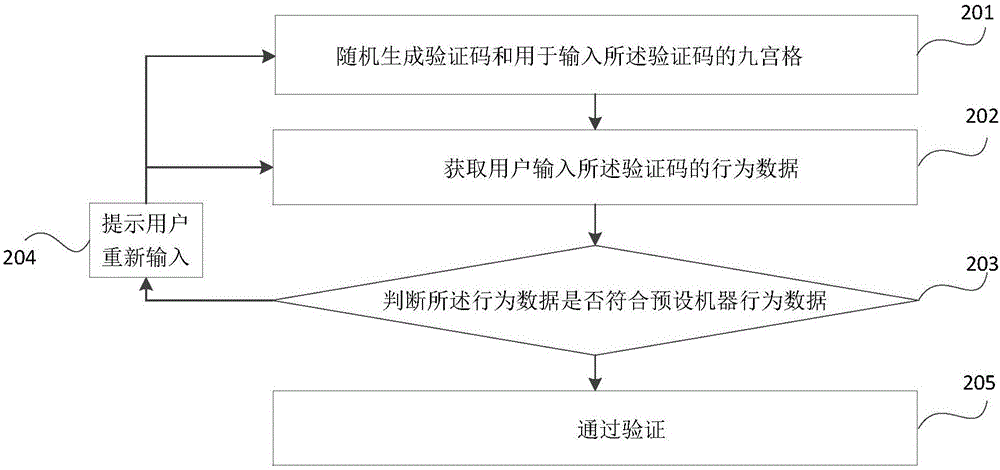
[0092] Such as image 3 As shown, it is a schematic flowchart of the security verification method in this embodiment.
[0093] In this embodiment, the verification code is a digital verification code, and the point-and-click operation interface is a nine-square grid as an example for illustration.
[0094] Step 201, randomly generate a verification code and a Jiugongge for inputting the verification code.
[0095] In this embodiment, preferably, the verification code is a 4-digit verification code. In this embodiment, the verification code is 2971 for illustration.
[0096] There are nine numbers from 1 to 9 on the Jiugong grid, which can be arranged in any order.
[0097] Step 202, acquiring behavior data of the user inputting the verification code.
[0098] Here firstly it is necessary to judge whether the verification code input by the user is 2971, and if so, proceed to step 203 to perform the Turing test, if not, then there is no need to perform the Turing test again, ...
Embodiment 3
[0117] Such as Figure 4 Shown is a schematic structural diagram of a security verification system according to an embodiment of the present invention, including:
[0118] A verification code generating unit 301, configured to randomly generate a verification code and a point-and-click operation interface for inputting the verification code;
[0119] A user behavior data acquisition unit 302, configured to acquire the behavior data of the user inputting the verification code through the point-and-click operation interface;
[0120] What needs to be explained here is that what is acquired is the behavior data of inputting "the said verification code". Therefore, if it is not the said verification code, that is, if the input verification code is wrong, it will be ignored directly, and the behavior data will not be obtained and stored any more; at the same time Prompt the user for re-enter.
[0121] The Turing test unit 303 is configured to pass the verification when it is dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com