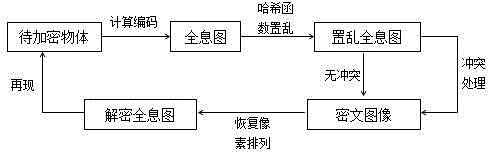
Calculating holographic encryption method based on Hash function
A technology of hash function and encryption method, applied in computing, image data processing, image data processing and other directions, can solve the problems of affecting decryption effect, complicated operation, strict requirements on optical path and parameter accuracy of holographic encryption method, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The following describes in detail a typical embodiment of a computational holographic encryption method based on a hash function of the present invention, and further specifically describes the present invention. It is necessary to point out that the following examples are only used for further description of the present invention, and cannot be interpreted as limiting the protection scope of the present invention, and those skilled in the art make some non-essential improvements to the present invention according to the above-mentioned content of the present invention And adjustments still belong to the protection scope of the present invention.
[0028] The concrete steps of an embodiment of the present invention are:
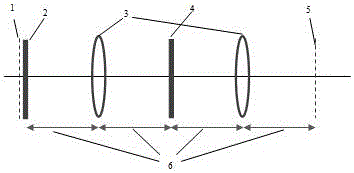
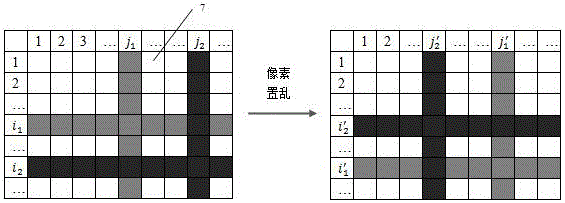
[0029] Step 1: Use MATLAB R2013a version program to read in the attached Figure 4 The original image shown for encryption has a pixel resolution of 1920x1080, namely M =1920, N =1080. After 30 times of Gerchberg-Saxton (GS) iterative cycles, the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com