A command encryption method applied in broadcast communication
An encryption method and communication technology, which is applied to secure communication devices and key distribution, can solve problems such as the inability to decrypt ciphertext, and achieve the effects of improving security, preventing decryption, and increasing the difficulty of deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
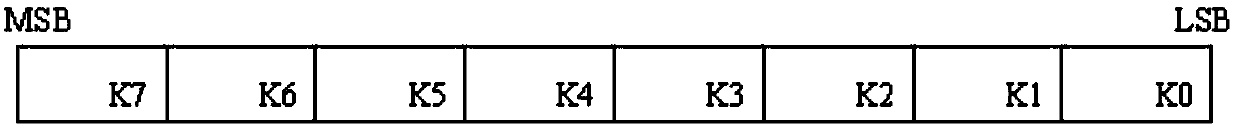
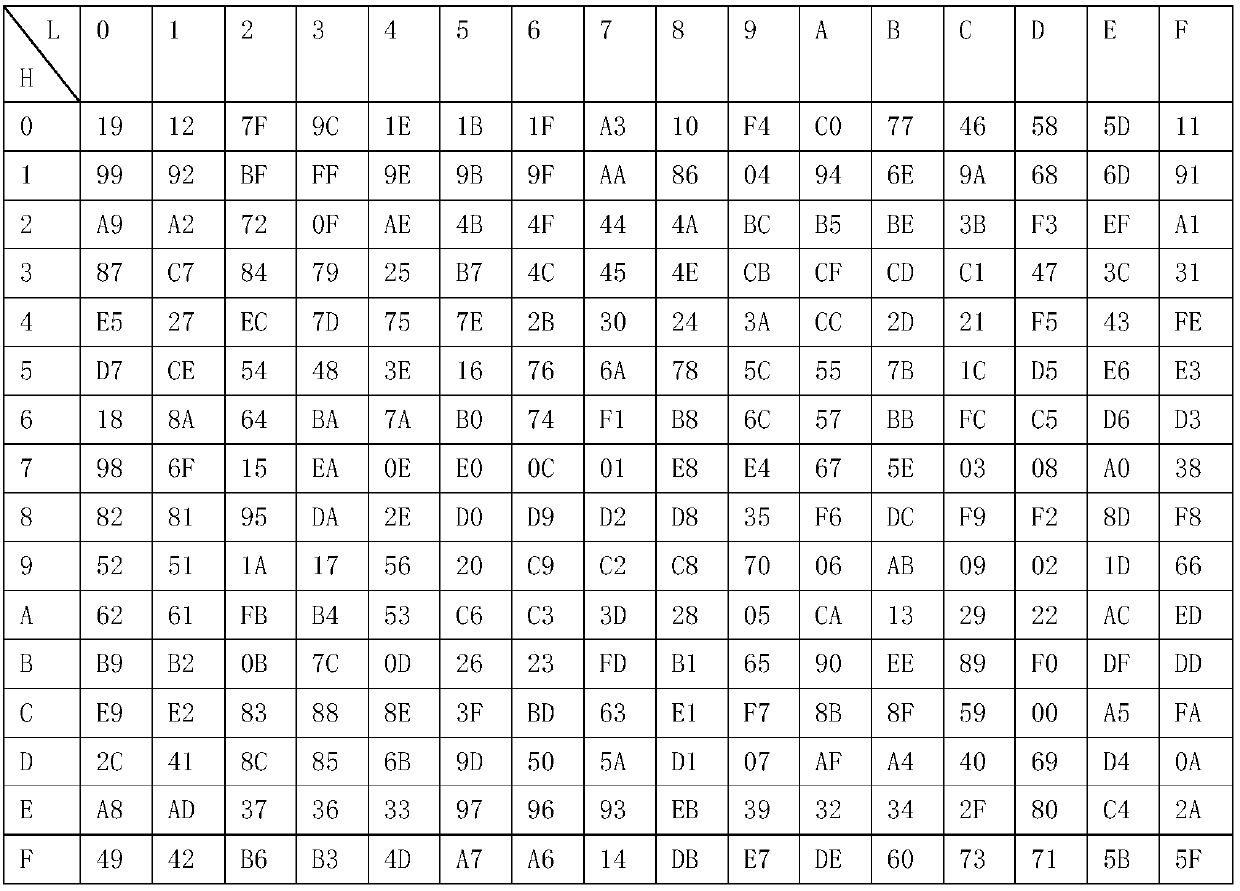
[0032] This embodiment is an instruction encryption method applied in broadcast communication, comprising the following steps:
[0033] 1) The key serial number SSN and the system master key SKEY are set in the front-end equipment system, and the key serial number update command is obtained through operation A, and sent to the terminal equipment system, wherein the front-end equipment system is provided with a timer, The timer updates the key serial number SSN every one minute, and recycles steps 1)-4) after each update of the key serial number SSN, and the system master key SKEY is unique and fixed;
[0034] 2) The terminal equipment system receives the key serial number update instruction, and obtains the key serial number SSN through the inverse operation of operation A, and the terminal equipment system calculates the received key serial number SSN and the system master key SKEY preset in the terminal equipment B obtains the system dynamic subkey SSKEY;
[0035] 3) The fr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com