Authorized user safe transmission oriented power distribution method in cognitive wireless network
A technology for authorized users and cognitive users, which is applied in the field of power allocation for secure transmission of authorized users, and can solve problems such as cognitive user performance impact and perception errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0095] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
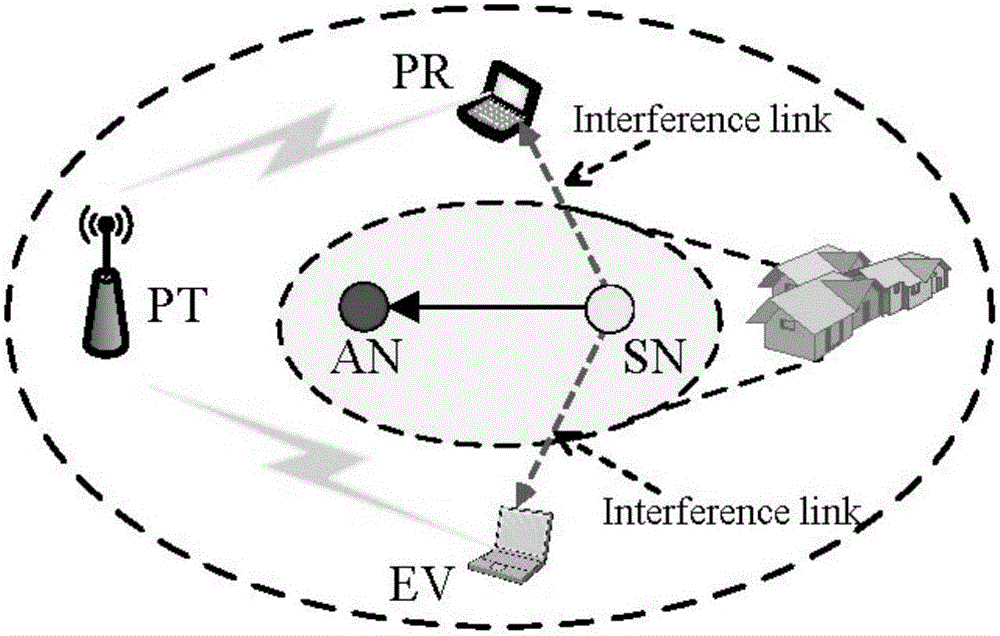
[0096] The present invention considers an Overlay network, such as figure 1 shown. The authorized user network is composed of an authorized user sending end (PT) and an authorized user receiving end (PR). At the same time, authorized users face the threat of eavesdropping by an eavesdropping end (EV). A cognitive user consists of a cognitive sender (SN) and a cognitive receiver (AN). Cognitive users use the Overlay method to access the network. Cognitive users perceive the spectrum occupancy and determine the transmission power. Due to the existence of perception errors, the transmissions of cognitive users interfere with the transmissions of authorized users. Considering that the cognitive user's transmission can also interfere with the authorized user's eavesdropping end, the authorized...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com