Anonymous bidirectional authentication method in mobile social network based on single hash function and false identity
A mobile social network and single-item hashing technology, which is applied in the field of anonymous two-way authentication based on single-item hash functions and pseudo-identities, can solve the problems of easy information leakage, large amount of encryption and decryption calculations, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
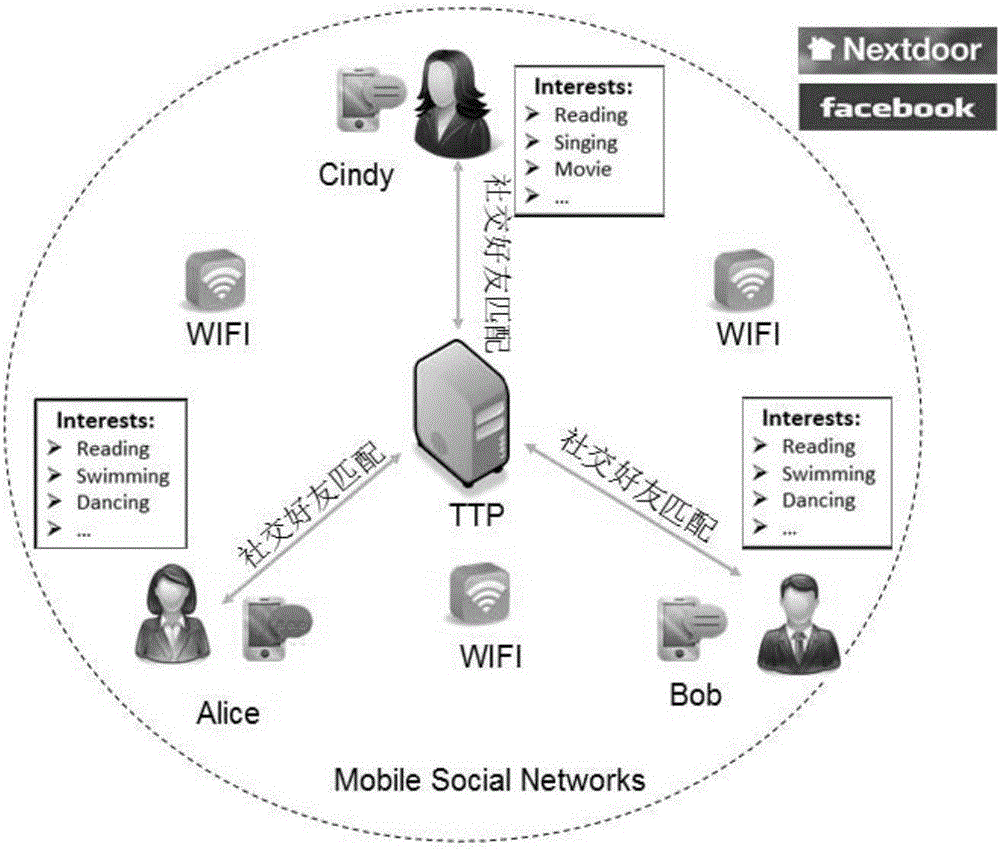
[0057] The following typical mobile social network scenario: Each user carries a smart mobile terminal, and can communicate with each other through WIFI or 4G. When they want to participate in social activities such as making friends on the mobile social network, they will respectively start the The same mobile application APP and initiates a registration request to the trusted server TTP that provides the service. Due to the privacy of these information, users hope to ensure that other irrelevant private information is not disclosed while obtaining the calculation results of common interests (attribute intersection) between users. The attribute matching model of mobile social network is as follows: figure 1 shown.
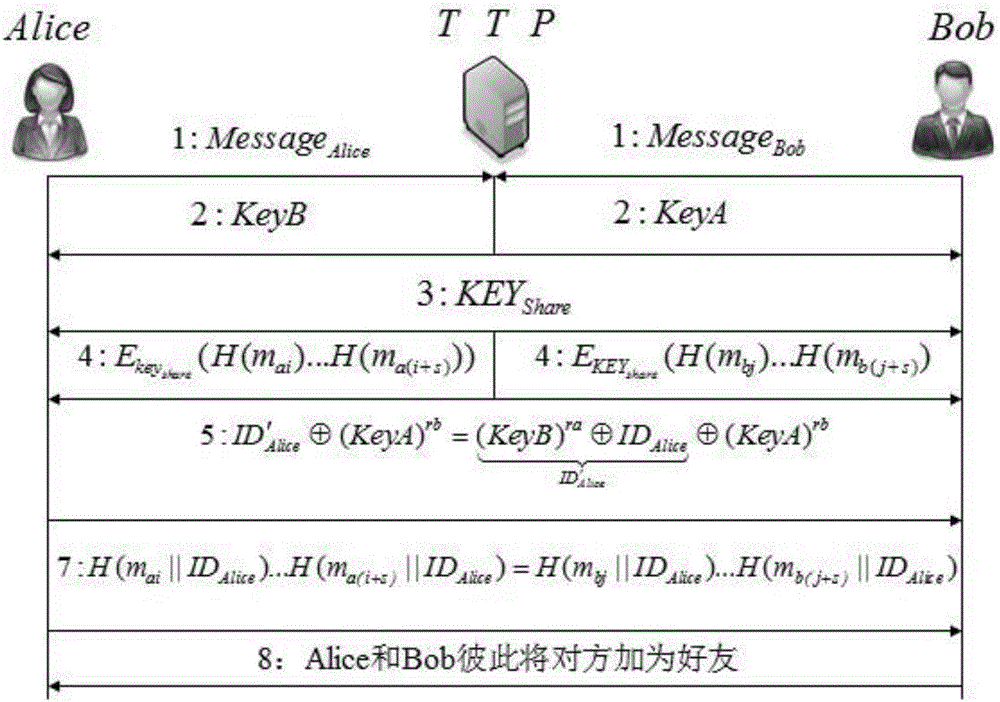
[0058] The specific process of the method of the present invention is as figure 2 As shown, the specific example steps are as follows:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com