Single packet source-tracing method based on storage resource adaptive adjustment
A technology for self-adaptive adjustment and storage resources, applied in the field of anonymous packet tracking, which can solve problems such as failure, high traceability and false alarm rate, and reduce traceability storage overhead, so as to improve utilization rate, improve traceability accuracy, and reduce traceability and false alarm rate. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
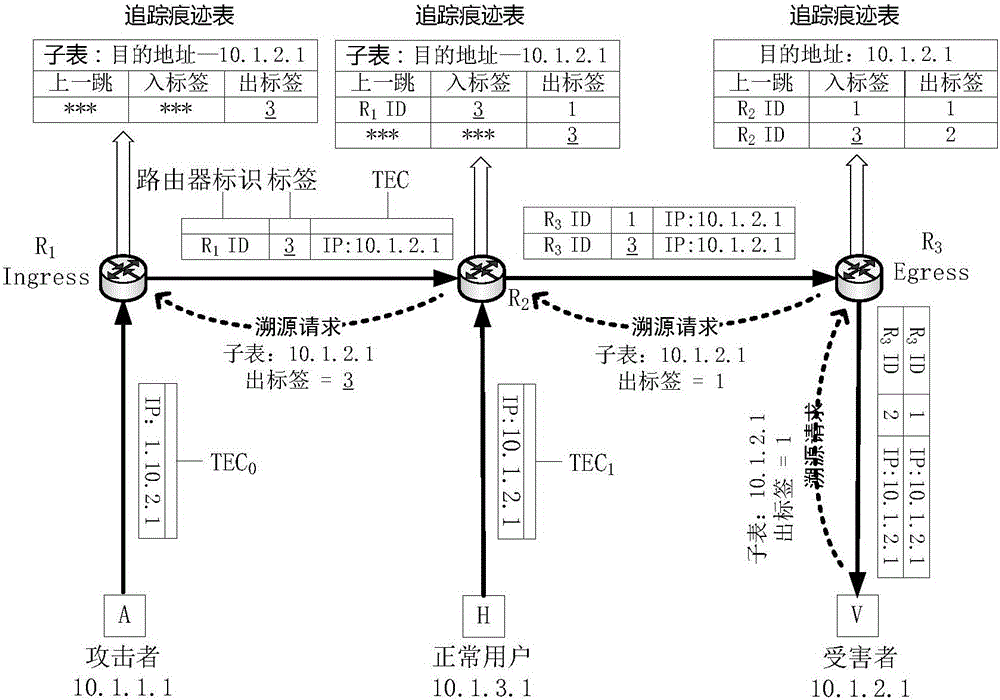
[0056] Embodiment 1 of the present invention: a single packet traceability method based on adaptive adjustment of storage resources, such as Figure 1 ~ Figure 3 shown, including the following steps:
[0057] S1, by estimating each source router R i The ratio of traceability paths carried by all routers to traceability paths M(R i ) to estimate the load of each traceability router and allocate storage resources for it; if the traceability system has been deployed in the whole network, then M(R i ) is calculated by:
[0058] M ( R i ) = Σ s ∠ R i ∠ t g s t ( ...
Embodiment 2
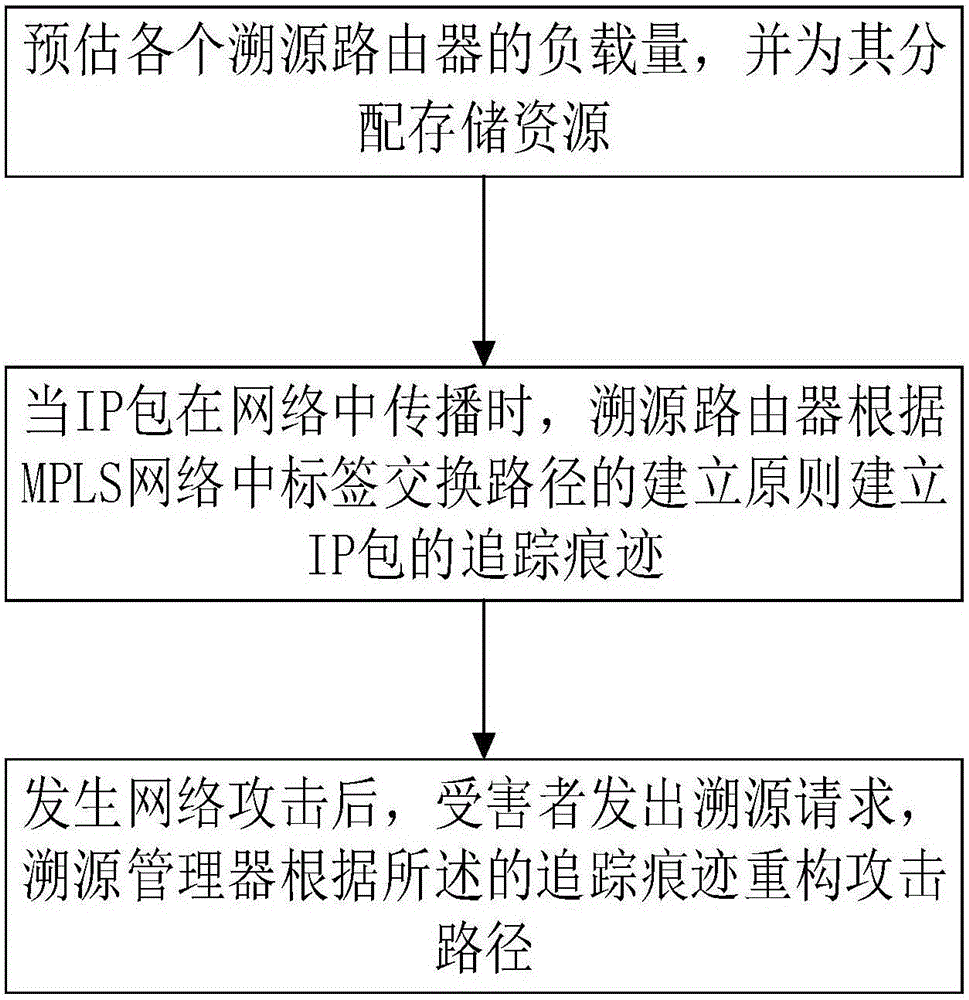
[0076] Embodiment 2: A single packet traceability method based on adaptive adjustment of storage resources, comprising the following steps:
[0077] S1, estimate the load of each traceability router, and allocate storage resources for it;
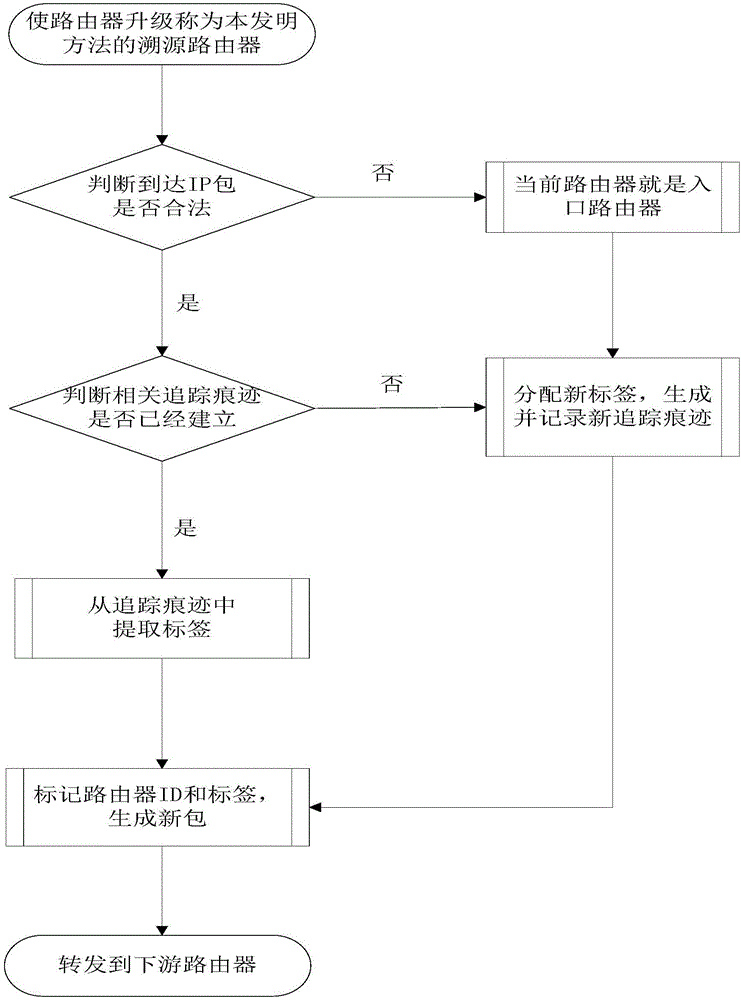
[0078] S2, when the IP packet propagates in the network, the traceability router establishes the tracking trace of the IP packet according to the establishment principle of the label switching path in the MPLS network;
[0079] S3. After a network attack occurs, the victim sends a traceability request, and the traceability manager reconstructs the attack path according to the trace trace; specifically, the following steps are included:
[0080] S31. After a network attack occurs, the victim identifies the IP anonymous packet, and then sends the IP anonymous packet to the traceability manager in the form of a traceability request;
[0081] S32. After receiving the request, the traceability manager extracts the tag information [upstream rout...
Embodiment 3
[0084] Embodiment 3: A single packet traceability method based on adaptive adjustment of storage resources, comprising the following steps:
[0085] S1, by estimating each source router R i The ratio of traceability paths carried by all routers to traceability paths M(R i ) to estimate the load of each traceability router and allocate storage resources for it; if the traceability system has been deployed in the whole network, then M(R i ) is calculated by:
[0086] M ( R i ) = Σ s ∠ R i ∠ t g s t ( R i ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com