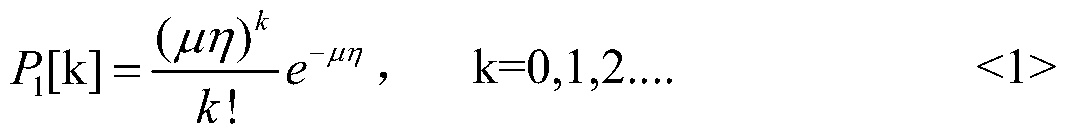Eavesdropping Discrimination Method Based on Quantum Key Distribution Based on bb84 Protocol
A quantum key distribution, BB84 technology, applied in the field of quantum communication, to achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
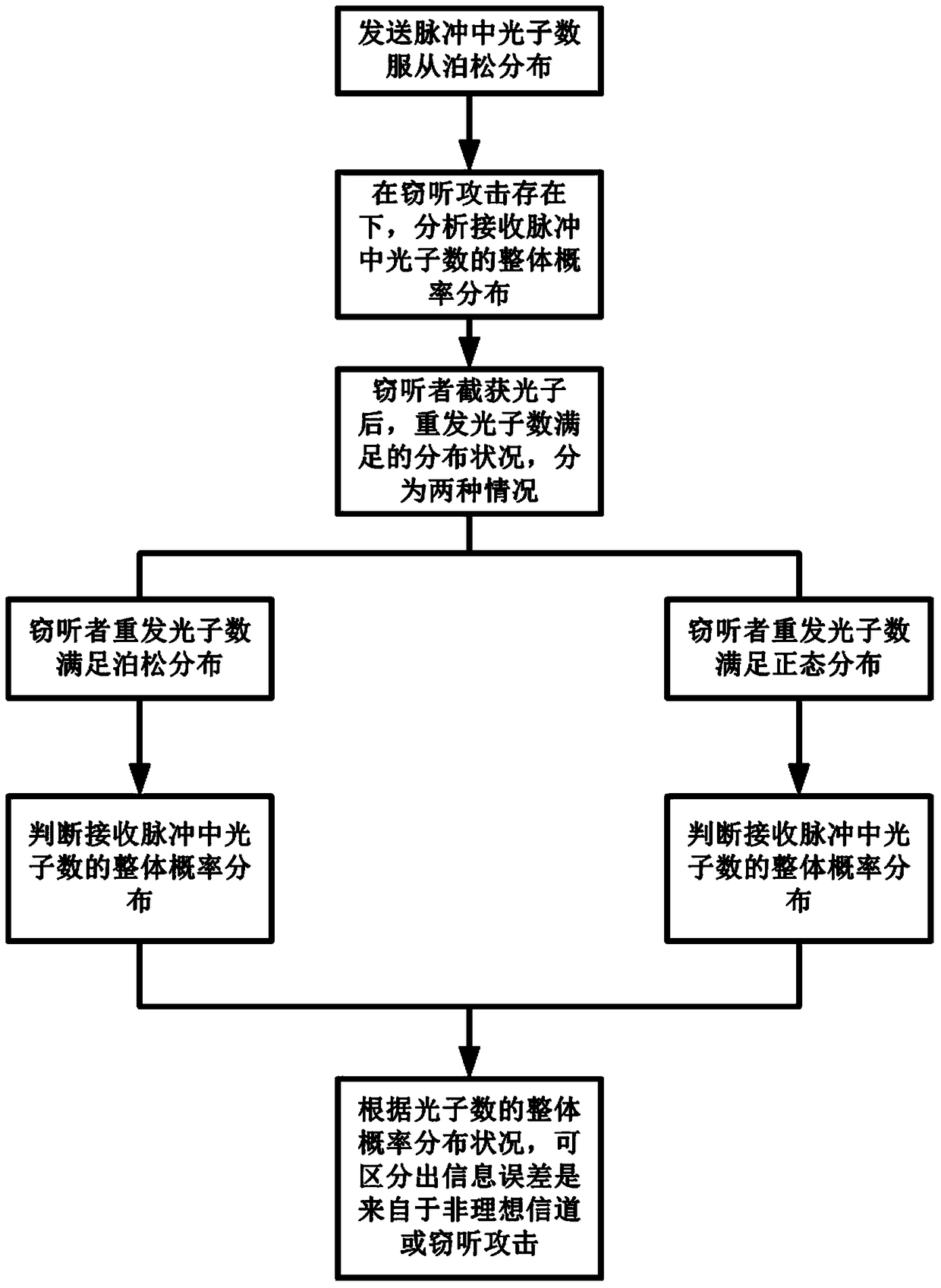
[0049] refer to figure 1 , the implementation steps of the present invention are as follows:
[0050] Step 1, according to the average photon number parameter in the BB84 protocol, define the Poisson distribution formula that the number of photons in the sent pulse obeys, namely
[0051]
[0052] Among them, μ is the number of photons in the transmitted pulse, η is the transmission efficiency under different channel conditions, η≤1, μη is the average number of photons in the pulse after channel loss, k is the average number of photons in the pulse, P 1 [k] is the probability of the number of photons in the pulse after channel loss, k! is the factorial of k and e is the natural exponent.
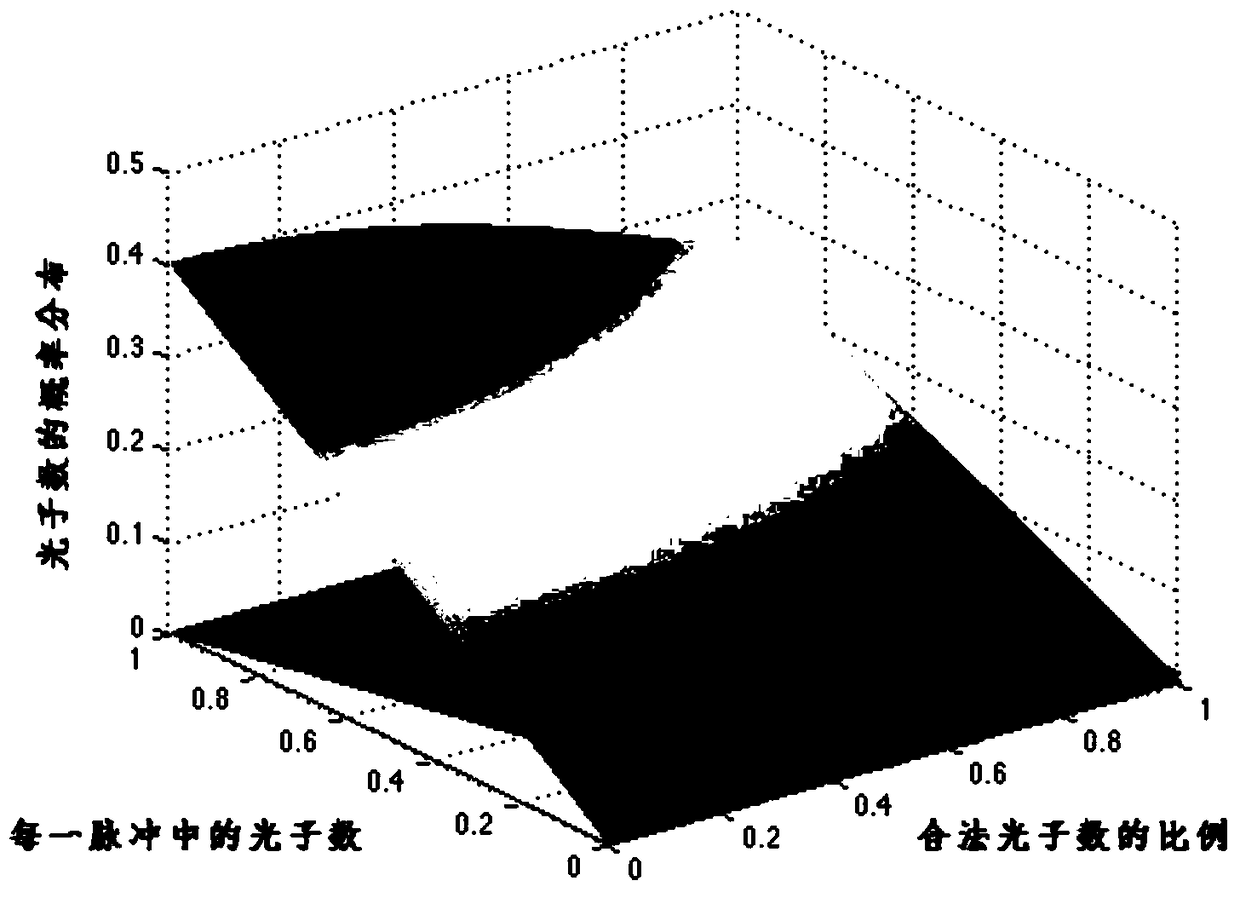
[0053] Step 2, according to the distribution state satisfied by the number of re-photons after the eavesdropper intercepts a part of the photons, the overall probability distribution of the number of photons in the received pulse sequence is judged:
[0054] When the eavesdropper interc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com